
No one expects securing mobile devices to be a fast check-off on IT and security to-do lists. But one area that seems manageable on the surface, becomes increasingly complex when you dig into the details – – updating to the current operating system.
The variety of mobile devices – over 25,000 different models in 2019 – combined with dozens of potential OSs and hundreds of OS versions, connected by some 100 wireless carriers in the US alone, leads the security-minded to conclude that this a much bigger problem than it seems on the surface.
Let’s break down the scope of the challenge. Traditional endpoints (laptops, desktops), at this point, are comparatively easy to secure. A key reason for this is, the user is not the admin of the laptop or desktop. IT is the admin and is responsible for providing multiple layers of defense and remote administration. Through manual and automated activities, they keep them updated and reduce the likelihood of successful attacks.
The problem is traditional endpoints only account for about 40 percent of endpoints in a typical organization. The remaining 60 percent do not enjoy the same luxurious security attentiveness which results in an increased likelihood of a successful mobile targeted attack.
Why mobile isn’t as secure as traditional endpoints
We already established mobile devices come in a vast selection of flavors. Add to that the speed at which mobile attacks are proliferating, which is much faster than the speed at which mobile security solutions are developing. In short, mobile threats are outpacing its own security.
Next, factor in the way people use mobile devices. A typical mobile device user (remember they are the admin and can do just about anything on the device) will happily download apps without giving security a second thought.
Adventurous users jailbreak or root their devices to enable options they otherwise might not have, weakening their device’s security in the process. Many will click on email links that they wouldn’t on a laptop or desktop, for a variety of reasons including the smaller form factor making it more difficult to tell if the link is suspicious, or a simple comfort level with these very personal devices.
Regardless of the reason, they are more likely to click on a phishing link on mobile than traditional endpoints. And when was the last time you heard someone say, “I really need a connection, but this free Wi-Fi seems kind of sketchy, so I’ll just stay offline?” It’s not happening.
But back to our original point, let’s say a few words about security patches for mobile. The fragmented Android market has different vendors delivering different patches via different carriers at different times – all for the same known vulnerability. Android and Apple patches are subject to the whims of the device user, who, as we noted, is the device administrator. The end result is that, according to Zimperium’s 2019 State of Enterprise Mobile Security Report, when it comes to installing OS patches, six out of 10 Android devices and three out of 10 iOS devices are more than five versions behind the latest release.
Why bad mobile security is really good news for very bad actors
As valuable corporate data follows enterprise workers through the corporate firewall and into the wild, riding happily on mobile devices, cybercriminals see a lucrative business model. That may seem like common sense – of course bad guys will go after easy, free-range target with a big return. But why just make that assumption when you can do the math?
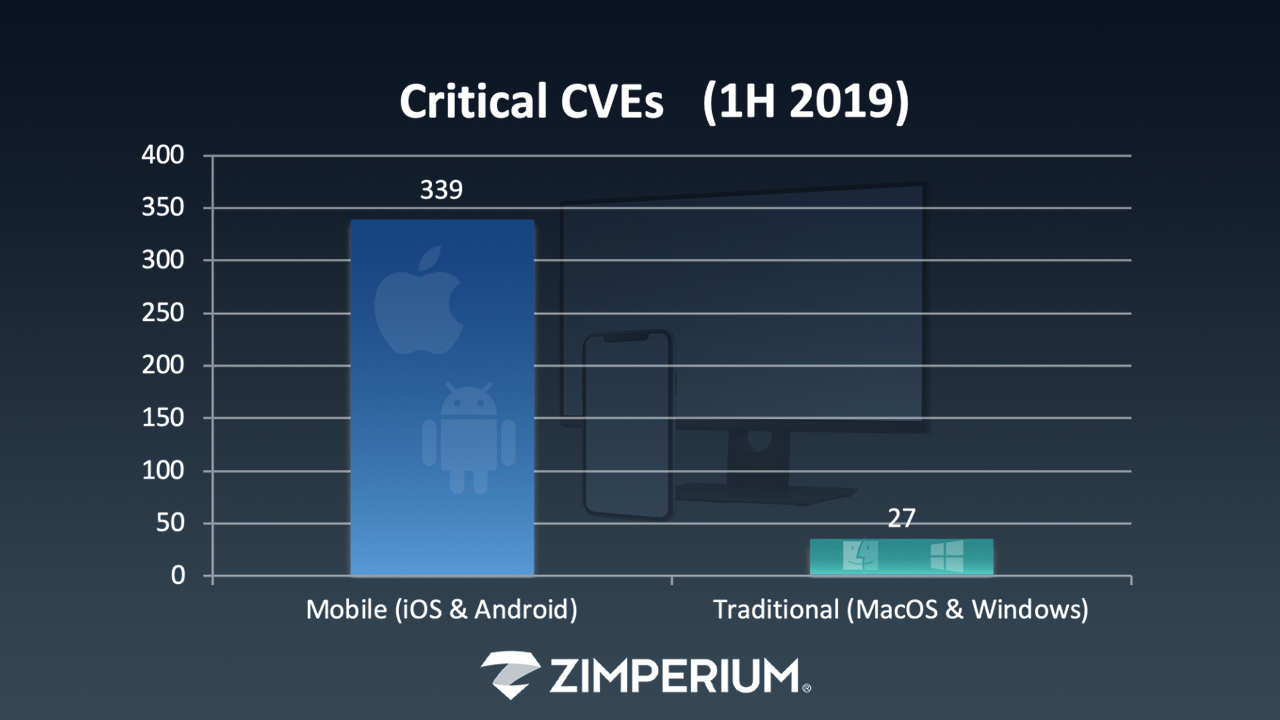
So, here’s the math. In the first half of 2019, Apple patched 147 CVEs (Common Vulnerabilities and Exposures). Some 59 percent of those CVEs were considered “critical” security threats. During that same time period, Google patched 255 CVEs, of which 99 percent were considered “critical” or “high” security threats.
Let’s put that into perspective by comparing it with figures for traditional endpoints—i.e., desktops. In the first half of 2019, Apple patched 133 CVEs for Mac OSs, of which only three percent were classified as critical. And, again in 1H 2019, Microsoft patched 193 CVEs on Windows 10 (version 1809) of which only 12 percent were classified as critical.
How Zimperium protects mobile devices, patched and otherwise
Let’s recap. There are lots of mobile devices, OSs and carriers. The enterprise has to secure them to protect corporate data and ensure regulatory compliance. The devices are administered by the users, are likely to be multiple versions of operating systems behind (therefore exposed to exploits that are freely available on the internet), typically have unknown and possibly compromised apps on them, and, to add to the enterprise risk, often connect to untrusted or fake Wi-Fi networks.
What can you do about this? We’re glad you asked. Zimperium offers real time, on-device protection for enterprise mobile devices against Android and iOS attacks. The Zimperium platform leverages our award-winning machine learning-based engine – z9 – to protect mobile data, apps and sessions against device compromises, network attacks, phishing attempts and malicious apps.
To date, z9 has detected 100 percent of zero-day device exploits in the wild without requiring an update, needing to connect to a network or suffering from the delays and limitations of cloud-based detection or legacy security architectures. How’s that for keeping up?
If you’d like to know more, we’d like to hear from you. Contact us here.



