Advanced, Scalable, Enterprise-Grade On-Device Mobile Security
The Zimperium z9™ mobile threat defense engine is our patented, dynamically updatable engine that uses behavioral and machine learning techniques to detect device, network, phishing, and application mobile attacks on-device and in real-time. Leveraging behavioral and system parameters, the z9™ engine powers on-device Zimperium security solutions against the unique threats targeting iOS, Android, and ChromeOS endpoints.
The on-device capabilities provided by Zimperium z9™ enable it to be privacy-focused and not rely on cloud-based lookups, content scanning, or other privacy-invasive techniques to keep mobile endpoints secure. This gives enterprises mobile security confidence and peace of mind across their personal and corporate-managed devices without relying on mobile device management tools.
As enterprises scale and adopt broader bring your own device (BYOD) policies, security teams can be confident that the z9™ engine is ready and able to adapt to the latest threats. Designed to receive updates with new and refined detections, the z9 engine provides the industry’s most advanced, on-device machine learning, all without requiring the endpoint to download an updated app.
Extensive, On-Device Detection and Forensics
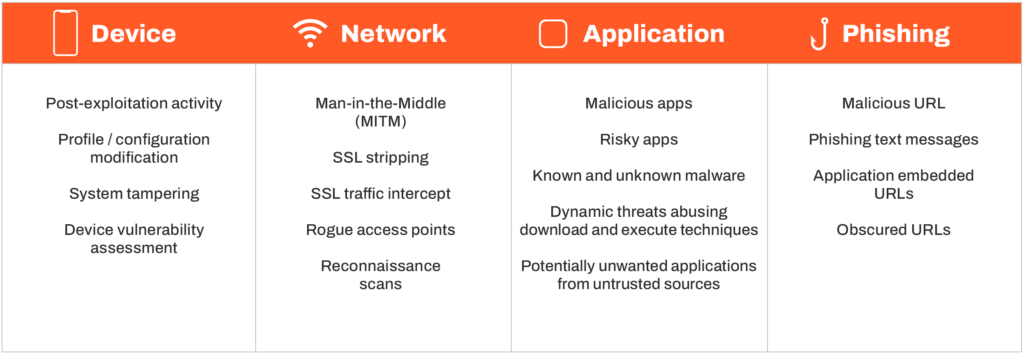
Zimperium z9™ detects known and unknown threats by analyzing the behavior of a mobile device. Capable of analyzing even the slightest deviations in the mobile device’s systems, including OS statistics and other system parameters, z9™ can accurately identify the specific type of malicious attack. Security teams can rely on z9™ capabilities to assess mobile system deviations, applications that behave as malware, anomalous network traffic, and advanced phishing attacks. Zimperium z9™ also provides critical mobile forensics necessary for security teams to assess and respond to security incidents, reducing the mean time to remediation.
Stop Mobile Zero-Day Threats
Unlike legacy mobile security engines, Zimperium z9™ monitors for malicious activity and attacks from the mobile attack vectors: phishing, network, application, and device. Zimperium z9™ is resistant to evasion techniques such as virtual machine awareness, execution techniques, and binary obfuscation. This enables Zimperium solutions to detect and protect against known, zero-day, and new threats even when disconnected from the network.


