Mobile App Security
What is Mobile App Security?
Mobile app security refers to the measures and practices used to develop and maintain applications that can protect themselves against various threats and vulnerabilities. To earn the trust of its customers, mobile-powered businesses must maintain the confidentiality, integrity, and availability of user data on their mobile apps.
However, to understand and identify the level of security required, we must first understand where risks to mobile applications arise. Risks associated with mobile apps primarily emerge in three areas:
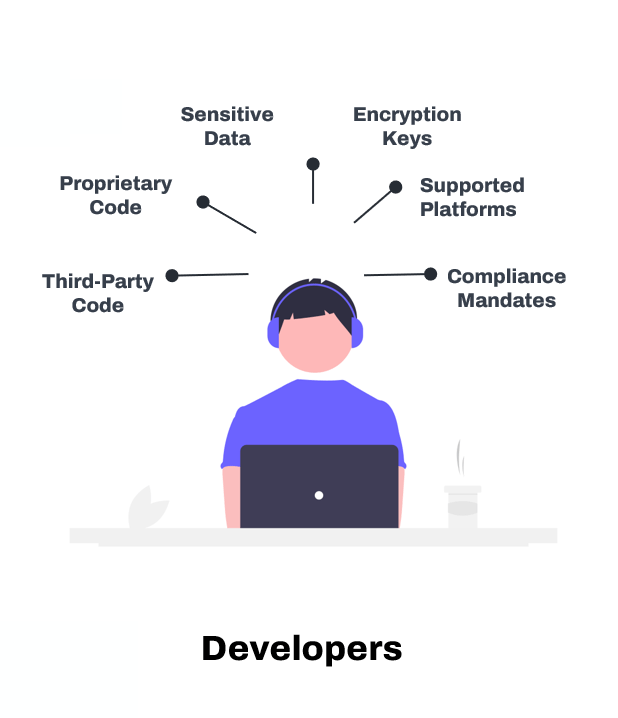
DURING DEVELOPMENT
App teams focused on reducing time-to-market
ONCE PUBLISHED
Attackers downloading & reverse-engineering the app
ON END-USER DEVICES
End-users’ habits make the device untrustworthy
Mobile App Security During the Development Process
Mobile app developers are globally distributed, have varying experience levels, minimal secure coding knowledge, and are pressured to deliver features quickly. They often need the proper security tooling to avoid inadvertently introducing security and privacy risks during development.
Below are some key contributing factors that result in vulnerabilities being inadvertently introduced into apps during the development process.
Development Environment

Mobile Development Languages
Development for multiple platforms (iOS, Android, etc.) may introduce inconsistencies in security implementations across platforms, resulting in vulnerabilities. The platforms and the development languages are evolving, making it difficult for app teams to keep up with all the changes.

Insecure Third-party Libraries
In the hurry to develop new features and get the app to market, developers might rely on third-party libraries without adequately vetting their security. Third-party libraries can introduce unknown vulnerabilities into the application. Many enterprises don’t have the luxury of a governance team that can vet third-party components and catalog them to be used enterprise-wide.

Limited Threat Modeling Data
The lack of threat data makes it difficult to determine which threats are most harmful to the app. This results in an overreliance on industry security standards without the data to decide how much security is required across different application functionality aspects.

Lack of Proper Tooling
Teams often lack the necessary mobile-specific tooling. Most teams tend to repurpose their tools for web applications, which do not focus on how apps are exploited in the store and end-user devices.
Limited Security Expertise

Weak Code Protection
There is insufficient protection against tampering. Most developers fail to understand how easily malicious actors can monitor and inspect their apps. Code obfuscation is done using freeware or open-source tools that are easily reversible.

Hard-Coding Credentials
When pressed for time, developers may take shortcuts like hard-coding credentials or other sensitive information within the code, making it accessible to anyone who can view it.
.

Poor Encryption
Most teams choose robust algorithms but fail to secure the keys. Mobile app teams rely too heavily on device hardware to store keys without realizing that even secure hardware can be compromised.

Lack of Runtime Protection
Most development teams have little to no threat visibility once the app is published. Runtime protection is mainly ignored when it comes to mobile applications.
Limited Capacity

Not Enough Mobile App Developers
Developer shortage remains the top challenge for most businesses. Digital transformation initiatives across the private and public sectors have made the marketplace competitive for skilled developers.

Not Enough App Security Engineers
The ratio of developers to security engineers is 10:1. Security teams can’t scale to provide timely guidance to app dev teams, increasing their reliance on security tools.
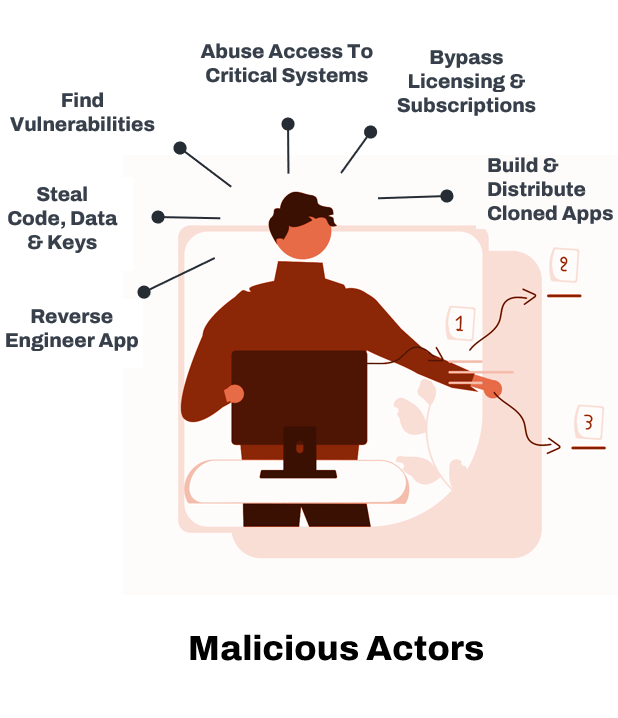
Mobile App Security when Apps Reside in Public Stores
Ubiquitous in today’s connected world, mobile applications are readily available in public app stores, waiting to be downloaded by anyone with a valid account. While this open access fosters a sense of community and sharing, it also reveals a disturbing lack of control and security. Even though app stores maintain specific requirements during the app upload process, they lack the means to determine whether a download will be used for malicious purposes. This security gap creates a playground for malicious actors who can download any app with a simple Gmail or iTunes account.
Let’s look at how malicious actors abuse apps in the app stores.
1. For Android Applications:
- JADX (Java Decompiler): An open-source tool that can convert Android’s DEX (Dalvik Executable) format into human-readable Java source code.
- Apktool: A tool for reverse engineering Android APK files, allowing disassembly, decompilation, and recompilation of the code. It helps in understanding the resources, manifest, and Smali code.
- Dex2Jar: This tool converts Android’s DEX files into Java’s JAR format, allowing further analysis with Java decompilers.
- JD-GUI: Often used with Dex2Jar, it’s a standalone graphical utility that displays Java source code from JAR files.
- Frida: A powerful dynamic instrumentation toolkit that lets you inject code into running apps to monitor and manipulate their behavior at runtime.
2. For iOS Applications:
- Hopper: A reverse engineering tool, Hopper can be used on iOS and other platforms. It disassembles, decompiles, and debugs the applications, providing a graphical interface to visualize the code’s structure.
- Ghidra: Created by the NSA, Ghidra is a versatile open-source reverse engineering tool supporting various platforms, including iOS.
- IDA Pro: One of the most popular reverse engineering tools, IDA Pro provides comprehensive features for analyzing binary code, including iOS applications.
- Frida: Similar to its application in Android reverse engineering, Frida is widely used in iOS for dynamic analysis and code manipulation.
3. Apps are Tampered
Once malicious actors have reverse-engineered a mobile application, they can manipulate, tamper with, and exploit it in various ways. Tampering with mobile applications after reverse engineering them represents a severe threat to the application’s integrity and users’ privacy and security.
Here’s how this tampering can happen and what it might entail:
- Inserting Malicious Code: By understanding the application’s structure and logic, attackers can embed additional malicious code that can steal data, display ads, launch attacks on other systems, or perform other unauthorized activities.
- Bypassing Security Measures: Many applications contain security controls like license verification, encryption, and authentication. Attackers can identify, remove, or modify these measures, rendering them ineffective or bypassing them altogether.
- Repackaging the Application: The altered application, complete with malicious additions or modifications, can be repackaged and redistributed. Unsuspecting users might download and install these rogue applications, thinking they are legitimate.
- Stealing Intellectual Property: After reverse engineering, attackers may copy proprietary algorithms, designs, or other intellectual property for personal gain or competitive advantage.
- Modifying Application Behavior: Attackers can change how the application functions, such as redirecting network traffic to malicious servers, altering transaction processes or manipulating how the application interacts with the user.
- Creating Fraudulent Versions: Using the original code as a base, attackers might create fraudulent versions of popular applications, luring users into providing personal or financial information.
- Unlocking Paid Features: In some cases, attackers may tamper with the application to unlock premium features, essentially pirating the content or services provided.
- Discovering and Exploiting Vulnerabilities: Through reverse engineering, attackers might uncover vulnerabilities that can be exploited in targeted attacks against users or organizations responsible for the app.
- Accessing Sensitive Information: By delving into the application’s inner workings, attackers may uncover encryption keys, API secrets, or other sensitive details that can be used for broader system attacks or data breaches.
- Spreading Malware: The tampered application can be used as a vector to spread malware to other devices, leveraging the trust and permissions granted to the original application.
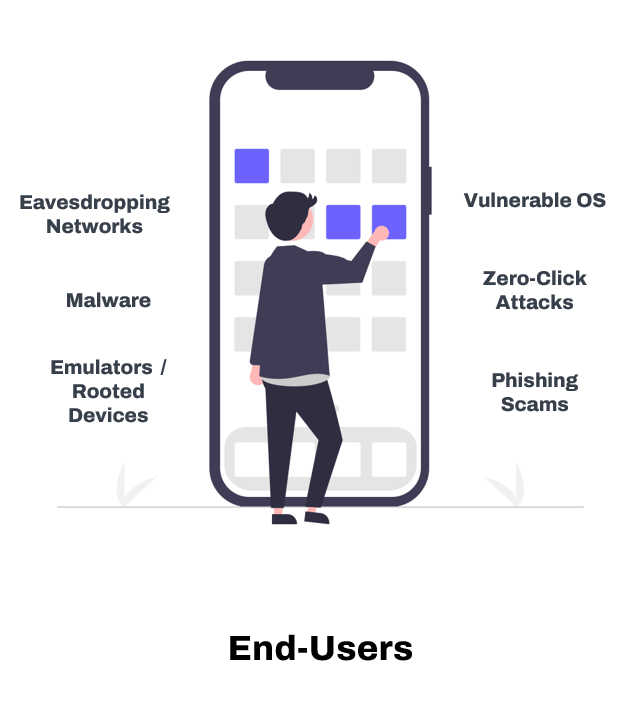
Mobile App Security When Apps are Running on End-user Devices
Mobile applications are eventually downloaded and installed on end users’ devices outside the control of the business that developed the application. Three key factors make the app vulnerable to exploitation and abuse during runtime.
App teams find it difficult to secure against all possibilities due to the following factors:
1. Device Fragmentation
Devices and models run different hardware and operating system (OS) versions worldwide. More than 1,000 companies are building more than 2500 Android models alone. Manufacturers release various smartphone models with custom OSs to meet the needs of different market segments in the smartphone market.
Here are some key drivers of fragmentation in the market:
- Major Manufacturers: Companies like Apple, Samsung, Huawei, Xiaomi, OPPO, and others offer various models catering to different market segments, from budget to high-end flagship devices.
- Number of Models: There are thousands of different smartphone models available worldwide when considering all the various brands, regions, and market segments.
- Operating Systems: Android, as an open-source platform, is used by many manufacturers, each with its line of devices. iOS is exclusive to Apple, contributing to a more consolidated product line.
2. Multiple Application Stores
There are over 300 app stores worldwide with millions of mobile apps to download. Apart from Google and Apple, there are third-party app stores, manufacturer-based app stores, operator stores, country-specific stores, and many more with millions of apps. The proliferation of app stores presents several challenges to mobile app security. Here are the primary reasons:
- Different Security Standards: Each app store may have different security review processes, policies, and standards. Some app stores may lack rigorous security checks altogether.
- Fragmented Oversight: With so many app stores, it’s challenging for a single governing body to oversee or regulate security standards.
- Fake Apps: With many third-party app stores, there’s an increased risk of counterfeit or copycat apps. These apps might look and function similarly to genuine ones but can contain malicious code, spyware, or other threats.
- Data Privacy: Different app stores may have varied data collection, storage, and sharing policies. If these policies are not strictly enforced, there could be potential risks to user data privacy.
3. End-User Cyber Hygiene
Cyber hygiene refers to practices and habits that individuals and organizations employ to maintain the health and security of their data on mobile. Several bad habits put data at risk on mobile.
- Trusting Public Wi-Fi: Using public networks without protection can expose your data to eavesdroppers.
- Clicking on Unknown Links: Often in SMS messages, emails, or social media, these can lead to phishing sites or malware downloads.
- Not Checking App Permissions: Blindly allowing all permissions can lead to unnecessary data exposure.
- Not Checking App Permissions: Blindly allowing all permissions can lead to unnecessary data exposure.
- Trusting all QR Codes: We are conditioned to trust QR codes in our personal lives unquestioningly. This trust creates ideal conditions for us to fall victim to QR code-based phishing and malware campaigns in the workplace.
What's Next: A Platform Approach to Mobile App Security
Although traditional mobile app security practices and solutions have made significant progress in protecting apps, they have been unable to keep up with the evolving threat landscape. Most solutions are built for the web and retrofitted for mobile, are free or open source with little support, and provide little to no visibility and protection once published. In the face of increasing speed to market pressures, enterprises, and mobile-powered businesses need help to adopt practical mobile app security solutions.
Zimperium provides an alternative approach with a single, integrated platform that protects from mobile app development through runtime.
Zimperium’s Mobile Application Protection Suite (MAPS) A vital component of the Zimperium Mobile-First Security Platform™, MAPS helps enterprises build safe and secure mobile apps resistant to attacks. It is the only unified solution that combines comprehensive in-app protection with centralized threat visibility. The platform provides app shielding, key protection, app scanning, and runtime protection capabilities. In addition, a threat management dashboard provides real-time threat visibility and the ability to respond to emerging threats instantly without an app update. MAPS consists of four products:
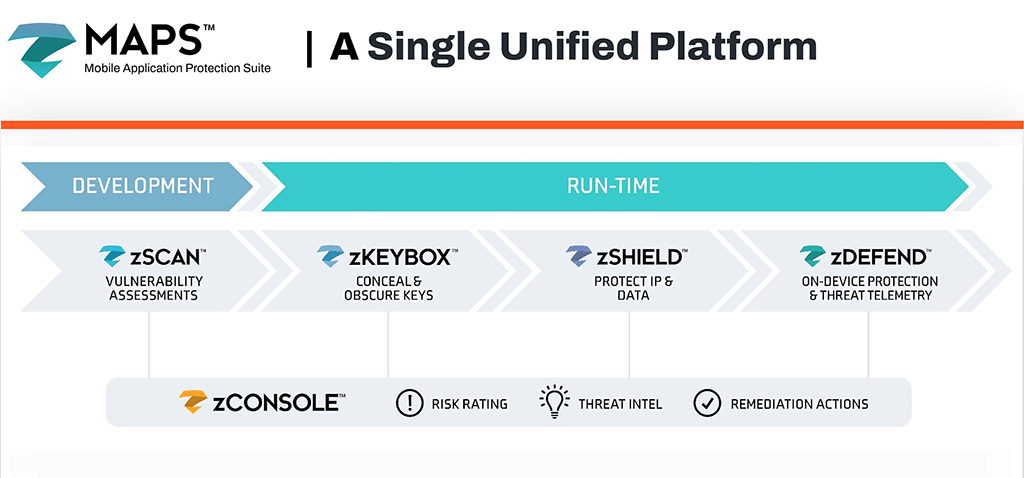
zScan
Discover and fix compliance, privacy, and security issues within the development process before publicly releasing your apps.
Learn more about zScanzKeyBox
Protect confidential data by securing cryptographic keys with white-box cryptography so they cannot be discovered, extracted, or manipulated.
Learn more about zKeyBoxzShield
Harden and protect the app with advanced obfuscation and anti-tampering functionality to protect the source code, intellectual property (IP), and data within the application.
Learn more about zShieldzDefend
Enable the mobile application to detect and proactively protect itself by taking actions on the end user’s device, even without network connectivity.
Learn more about zDefend
Top 5 Mobile App Security Best Practices
The primary objective of security best practices is to safeguard an organization’s data, systems, and networks associated with mobile applications. With these best practices, organizations can gain visibility into threats, detect threats proactively, comply with regulations, and respond to security incidents quickly, enabling them to build secure, compliant, and resilient mobile applications. The top 5 best practices are as follows:
- Integrate Mobile-Specific App Scanning: Developers and testers should leverage mobile-focused binary scanning solutions to complement traditional source code scanners. These scanners focus on identifying and mitigating exploitable vulnerabilities that allow abuse and exploitation of stores and end-user devices.
- Enable Runtime Threat Visibility: Embrace in-app security solutions that enable runtime threat visibility across device, malware, network, and phishing threat vectors. The real-time alerts allow SOC teams to monitor and respond to apps being abused continuously. Deep forensics enables app development teams to perform threat modeling to ensure they are secured against the most relevant threats.
- Look Beyond Code Obfuscation: Code obfuscation is a significant first step to protecting mobile app code. But real protection lies in progressing towards comprehensive application shielding. Application shielding aims to prevent and detect tampering and reverse engineering attacks. Shielding is an in-app security technology, which means its capabilities are implemented directly within the application itself rather than on the server.
- Focus on On-Device Protection: Mobile apps run on end-user devices outside the control of the app team. End-user cyber hygiene exposes apps to malware, rogue networks, compromised devices, and phishing attacks. As all these attacks occur on the device, the app must respond on-device without relying on network connectivity or cloud computing.
- Move Toward Dynamic Security: Attack techniques, malware, and vulnerabilities are emerging more frequently. Using in-app security updates over the air can prevent these evolving risks without publishing a new app. Your solution should allow you to update detection capabilities and in-app threat responses dynamically.
Top Mobile App Security & Privacy Frameworks
By following several practices, developers can enhance mobile application security, including securing code, regular security testing, encryption of data, authentication mechanisms, updates, and patches, and staying on top of the latest security threats. Several widely used security and privacy frameworks can help you start your journey toward securing your mobile applications. Let’s look at the top frameworks:
- OWASP Mobile Security Project: The Open Web Application Security Project’s (OWASP) Mobile Security Project provides guidelines and best practices for creating secure mobile apps. It identifies critical security risks facing mobile apps as well as strategies on how to mitigate them effectively.
- Mobile Application Security Verification Standard (MASVS): The Mobile Application Security Verification Standard (MASVS), developed by OWASP, sets security requirements and serves as a testing guide for mobile apps. With three levels (basic, intermediate, and advanced), the standard seeks to assist developers with creating secure apps.
- Mobile App Security Requirements and Verification (MASVR) Framework: The Mobile App Security Requirements and Verification Framework from OWASP serves as another initiative that works alongside MASVS by offering detailed requirements and verification procedures for mobile apps to ensure they comply with necessary security standards.
- NIST Cybersecurity Framework: The NIST (National Institute of Standards and Technology) Cybersecurity Framework is a comprehensive set of guidelines, standards, and best practices to assist organizations in managing and improving their cybersecurity risk management, not just mobile applications. Click here for specific NIST guidance on Mobile Endpoint Security and Mobile Application Security.
- GDPR: GDPR stands for the General Data Protection Regulation. It is a regulation introduced by the European Union in 2018 to safeguard the personal data and privacy of EU citizens for transactions that occur within EU member states. It also addresses the export of personal data outside the EU. GDPR ensures mobile apps prioritize user privacy by collecting only essential data and enhancing security measures, including robust encryption and regular testing. It mandates clear consent forms, promotes privacy from the design phase, and enforces accountability through regular audits and a verifiable compliance framework.
- PCI DSS (Payment Card Industry Data Security Standard): For mobile apps that handle payment card data, PCI DSS provides essential guidelines for securing this data. Encouraging secure coding practices, regular testing, and ensuring compliance from any third-party vendors or services helps protect sensitive payment data.
- HIPAA (Health Insurance Portability and Accountability Act): For healthcare-related apps in the U.S., HIPAA compliance is essential for protecting patient data.
Recommended Reading
Mobile App Security Whitepapers & Reports
Mobile App Security News
- Zimperium Launches the Only Unified Mobile Security Platform for Threat Detection Visibility and Response for both Endpoints and Apps
- Zimperium Named Winner in the 19th Annual 2023 Globee Cybersecurity Awards
- Zimperium Positioned as the Leader in the 2023 SPARK Matrix™ for In-App Protection by Quadrant Knowledge Solutions
Mobile App Security Glossary Terms & FAQs