Continuous Mobile Application Security Scanning

Mobile App Security: Critical Vulnerability Checklist for Android

Why Traditional Pen Testing Falls Short
For most enterprises, manual pen testing can be vital – and for those subject to regulation, it can even be required. But pen testing is not just cost and time-prohibitive but counterproductive to development teams incentivized to develop and release faster. Enterprises have a unique opportunity to add value by integrating automated security testing into their DevOps process to complement end-of-cycle pen testing.
Automated Security Testing with zScan
Zimperium’s zScan offers rapid, automated penetration tests for each build, ensuring vulnerabilities are detected and addressed promptly without slowing down releases. zScan focuses on finding vulnerabilities that make the application prone to abuse and exploitation once on the app stores and end-user devices. The scan runs in minutes, so developers can integrate it into DevOps workflows while maintaining development velocity, increasing remediation time, and reducing costs associated with end-of-cycle pen testing.
We’re redefining mobile app risk identification based on our powerful app analysis engine, APPVisualizer®. Our technology doesn’t just spot exploitable vulnerabilities on mobile – it highlights best practices and recommends countermeasures. It allows users to gain meaningful insights into app risks to help them make better decisions.


Key Capabilities
Performs an in-depth static and dynamic analysis of the binary and provides prioritized security and privacy findings.
Uncovers compliance violations tied to NIAP, PCI, GDPR, OWASP, MASVS, HIPPA and more to avoid costly fines.
Assesses the app’s SBOM to identify risks within third-party components to mitigate supply chain risks.
Allows for frictionless integration across the DevSecOps lifecycle integration via plugins, APIs, and GitHub actions.
Assessments are available via JSON, SARIF and PDF formats for flexibility in providing insights tailored to diverse management and technical personas.
Free Mobile App Scans for 30 Days via GitHub Action

Why Zimperium is Different
Adopts the Mindset of an Adversary
Applies adversary techniques for authentic threat simulations.
Highlights Insufficient Protection
Checks if code, data, and key protections are adequate.
Apply Countermeasures
Enables in-app protections within the platform.
Deep Inspection
Uses machine learning and rule-sets to uncover latent issues in first-party and third-party code.
Runs in Minutes
Quick scans drive developer motivation and productivity.
Reduces Device Overhead
Uses real devices and emulators for static and dynamic analysis.
“Mobile applications are central to a company’s digital transformation. Ensuring these apps do not present vulnerabilities that can be exploited is essential to enable this transformative process. Mobile AST largely uses similar techniques to traditional AST, but it must adapt those techniques to the mobile device environment and the more agile development processes that come with it.”
Gartner Hype Cycle for Application Security, 2022
By Joerg Fritsch
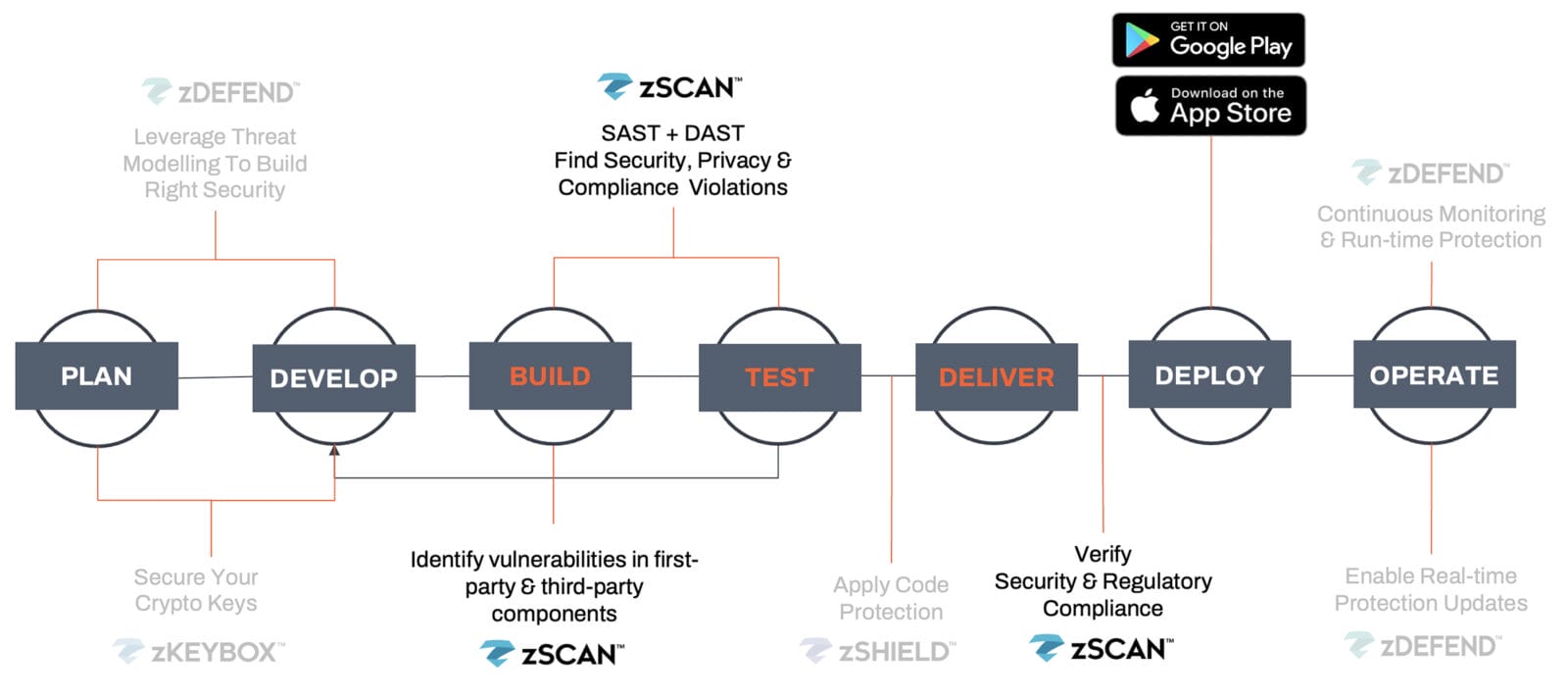
How zScan Transforms Release Cycle
Continuous Scanning During Development & Pre-Release Phases
Meet Compliance Requirements







