Earlier this week, Zimperium (@ZIMPERIUM), the leader in mobile threat protection, unveiled a major vulnerability in Android – Stagefright. Joshua Drake (@jduck), VP of Platform Research and Exploitation and a senior member of Zimperium zLabs, proactively studied the code. According to a few firms, other people have identified vulnerabilities in […]
Protecting from Hacking Team’s Mobile APT
While the world was going through the emails and exploits that Hacking Team’s leak revealed, we tested our mobile threat protection solution with one of the most advanced attack mechanisms. The result? Zimperium customers are safe from Hacking Team’s attacks, without any engine update! Hacking Team used advanced mobile APT […]
Zimperium customers are safe from Samsung Keyboard Security Risk
A potential security risk has been discovered on a large number of Android Smartphones as discovered by Nowsecure. Some of the latest devices, such as Samsung Galaxy S6, and Galaxy S5, come pre-loaded with a third-party keyboard app, SwiftKey, which fetches an update over unsecure and invalidated channel. This allows the […]
Joshua Drake and Jimmy Shah join zLabs Advanced Research and Exploitation Team
As the security industry kicks off RSA 2015 the Zimperium team is excited to announce the addition of two long time security experts to the zLabs Advanced Research and Exploitation team this week. Joshua J. Drake will be joining us as the new senior director of platform research and exploitation, […]
Zimperium Raises $12M in Series B Funding Led by Telstra
We are excited to announce that Zimperium raised $12M in Series B Funding. This is a major milestone for Zimperium and is a testament to the quality of the Z-Team, the products we develop and the customers we have in place successfully using Zimperium’s Mobile Threat Defense. 2014 was a […]
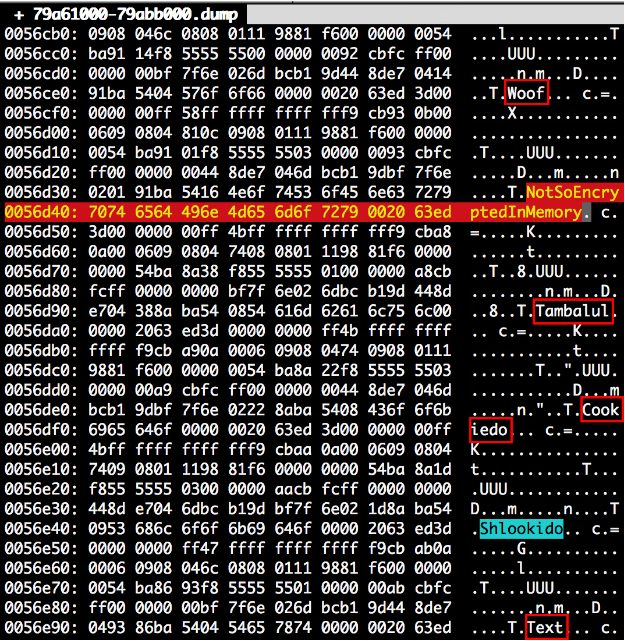
Telegram App Store Secret-Chat Messages in Plain-Text Database
EDIT: The following post * was not on a rooted or jailbroken device *. In order to access the plain-text secret-chat database containing the messages, we used our implementation of CVE-2014-3153. The claims that the device is rooted / jailbroken are incorrect and misleading. I will start by quoting CryptoFail […]
Cutting through the Weekly Mobile Security Noise: The Kaspersky Lab Disclosure
This week we’ve been monitoring reactions to a report released on Monday by Kaspersky, the Moscow-based internet security company. The firm claims it has uncovered spying software inside the hard drives of several institutions across thirty different countries, making it “the most sophisticated attack the world has seen to date.” […]
Does Your BYOD Policy Allow Bad Apps
BYOD policies enable economies of scale but also introduce vulnerabilities to the enterprise. Many employees unknowingly bring malicious apps to work compromising identities and enabling conduits for spies. But what is the effect of BYOD on enterprise security? What are the best-practice BYOD security policies for organizations looking to embrace […]
Cutting Through the Weekly Mobile Security Noise: We are all in this together
This week in cyber security we have seen that in the face of attacks from seemingly every angle the best way to fight back and move forward may be as a united front. While the concept might not seem far-fetched considering that it only takes one weak link (perhaps a […]
Cutting Through the Weekly Mobile Security Noise: The Weakest Link
In the world of cyber security there is no denying that we are only as strong as our weakest link. The main issue however is trying to predict which link is most likely to make a mistake and leave an organization vulnerable to a potential security breach. This week we […]