While the world was going through the emails and exploits that Hacking Team’s leak revealed, we tested our mobile threat protection solution with one of the most advanced attack mechanisms.
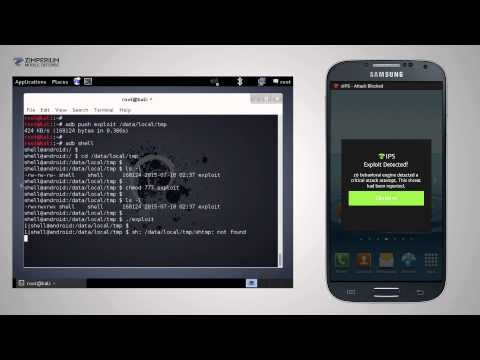
The result? Zimperium customers are safe from Hacking Team’s attacks, without any engine update! Hacking Team used advanced mobile APT techniques that bypass ALL of the mobile security solutions in the market except for Zimperium’s! Watch the video to see how zIPS users are protected from the Hacking Team exploits:
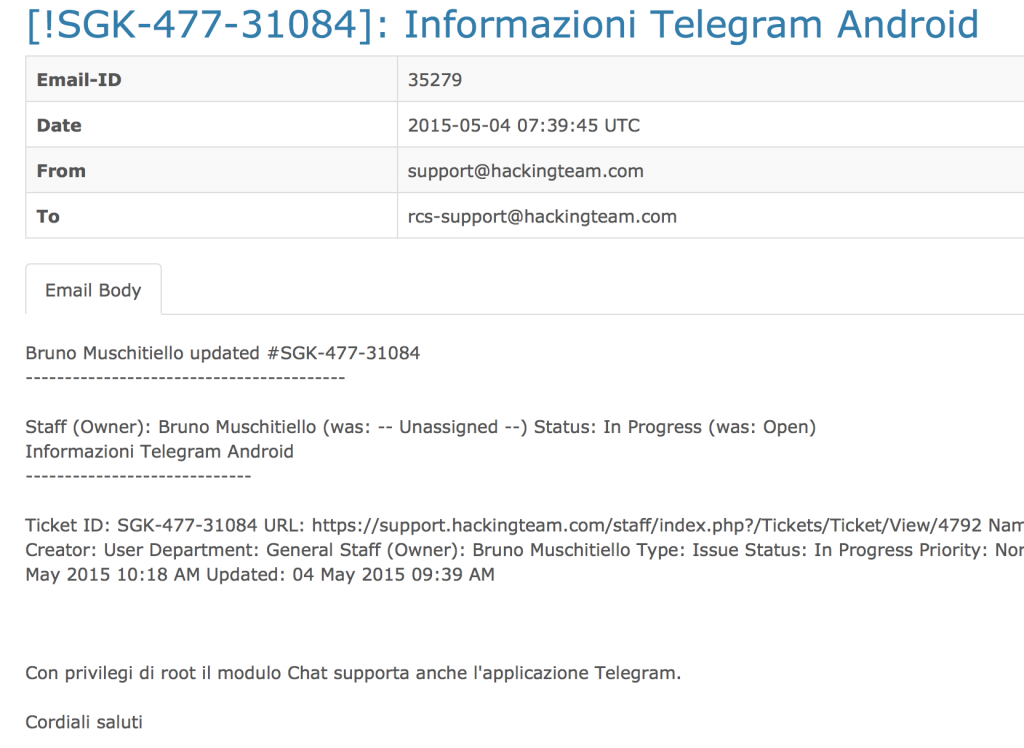
Hacking Team launched several attacks specifically targeting mobile devices. According to the following communication by the Hacking Team, the most critical attack they had was an Android remote browser exploit bundled with kernel exploit. While the industry has been oblivious to such attack vectors, our team has been highlighting them across multiple reports such as The Real Mobile Threat Landscape and the Response to Verizon’s Report.
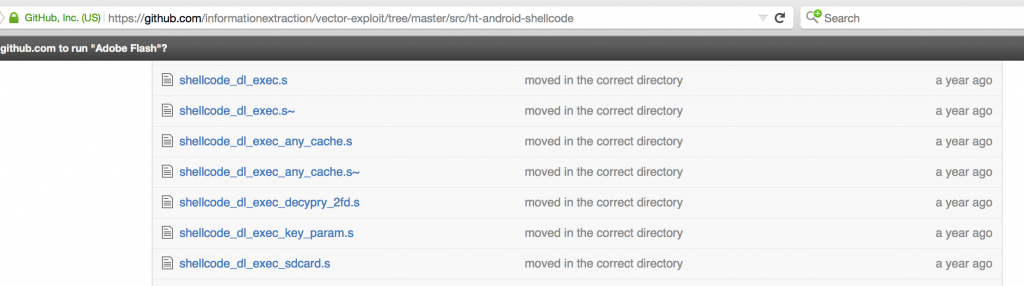
Our research team at zLabs analyzed their emails and files, and saw a clear strategy – to gain code execution on the device, using remote exploits including browser exploit or physical access that circumvent all security restrictions by running a kernel exploit. The Hacking Team attackers have used modified versions of public exploits like TowelRoot, Putuser and Framaroot, Zergrush and others as well their own exploits. Hacking Team did customize these exploits, thus bypassing signature-based solutions.
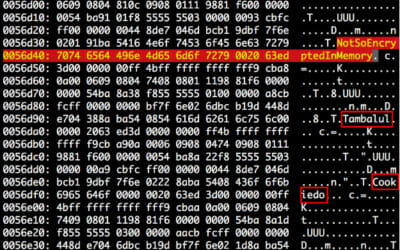
Other techniques used by the Hacking Team include running Kernel or OS exploits to gain system-wide permissions and used it to spy over software like Telegram, Whatsapp, Skype and others. Zimperium described the Telegram weaknesses in a blog post in February – and Zimperium customers are safe from this threat as-well.
zIPS has proven to be the only solution in the market that is capable of protecting against ‘Download and Execute’ shellcodes techniques used by Hacking Team.
In nut shell, Hacking Team helped us validate that Zimperium’s solution design is the ideal approach to protect from mobile Advanced Persistent Threat (mobile APT). We are the first, and still the only player, to offer an on-device behavioural engine that is capable of detecting HackingTeam exploits regardless of the method of delivery.
It is time for enterprises to understand the mechanisms of advanced mobile APT, and adopt relevant solutions. Several industry leaders including Samsung and Telstra have backed and partnered with Zimperium to help bring advanced mobile protection to the enterprises at large.
If you would like to protect your organization from advanced mobile threats, reach out to us here.
Follow us on twitter @ZIMPERIUM