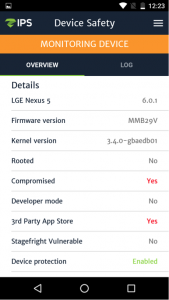
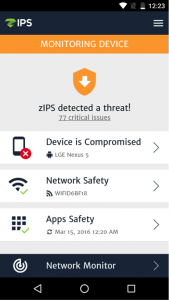
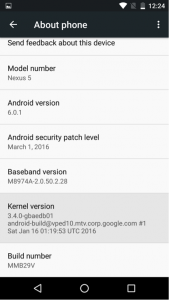
 On March 15th, Zimperium’s zIPS Mobile Threat Protection solution identified a zero-day mobile attack and its zLabs research team immediately reported the exploit to the Android Security Team. The reported attack is delivered via a publicly-available rooting application, KingRoot, using an unpatched local elevation of privilege vulnerability in the kernel reported as CVE-2015-1805. Affected devices are unpatched Android devices on kernel versions 3.4, 3.10 and 3.14, including Google’s own Nexus 5 and Nexus 6 devices running the March 01, 2016 Security patch level or below.
On March 15th, Zimperium’s zIPS Mobile Threat Protection solution identified a zero-day mobile attack and its zLabs research team immediately reported the exploit to the Android Security Team. The reported attack is delivered via a publicly-available rooting application, KingRoot, using an unpatched local elevation of privilege vulnerability in the kernel reported as CVE-2015-1805. Affected devices are unpatched Android devices on kernel versions 3.4, 3.10 and 3.14, including Google’s own Nexus 5 and Nexus 6 devices running the March 01, 2016 Security patch level or below.
From RedHat’s Bugzilla 1202855: “A flaw was found in the way pipe_iov_copy_from_user() and pipe_iov_copy_to_user() functions handled iovecs remaining len accounting on failed atomic access. An unprivileged local user could ‘use’ this flaw to crash the system or, potentially, escalate their privileges on the system.”

Just three days after reporting our findings, on March 18th, Google released an emergency patch addressing the vulnerability and exploit to the Android Open Source Project (AOSP).
Google’s advisory: http://source.android.com/security/advisory/2016-03-18.html
Fixes
Google has released a fix in the AOSP repository for multiple kernel versions. Android partners have been notified of these fixes and are encouraged to apply them. If further updates are required Google will publish them directly to AOSP.
| Kernel Version | Patch |
| 3.4 | AOSP patch |
| 3.10 | AOSP patch |
| 3.14 | AOSP patch |
| 3.18+ | Patched in public Linux kernel |
Mitigations and Recommendations
Additional mitigations that were cited in the Android Advisory include:
- Verify Apps has been updated to block the installation of rooting applications that use this vulnerability both within and outside of Google Play
- Google Play does not allow rooting applications, like the one seeking to exploit this issue
- Android devices using Linux kernel version 3.18 or higher are not vulnerable.
Zimperium recommendations:
- Restrict download of applications from unknown sources where possible
- Leverage mobile security solutions such as zIPS to provide immediate notification and remediation of devices that may be under attack from both the rooting tool, or other vectors leveraging the same exploit mechanism
Zimperium Handset Alliance (ZHA)
Zimperium also notified 30+ carriers and device manufacturers, members of the ZHA, of the advisory and emergency patch on March 18th. We encouraged our vendor members to heed the Google advisory recommendation to apply the fixes and our carrier members to release an update for the affected devices once an update is available.
Zimperium Customers and Partners
Zimperium customers and partners are safe from this and many more device, network and application threats. zIPS detected this exploit as well as its associated device tampering and persistent OS modifications, providing detailed forensics without requiring an update or modification to our z9 engine. No further action is required on your behalf.
As a large proportion of devices are vulnerable to this exploit, it would not be surprising to see this exploit leveraged via other attack vectors (app, email, Stagefright, etc) in the near future.
Acknowledgement
We would like to thank the Google Security Team for this immediate analysis and patch. Three days from initial email to patch is impressive!