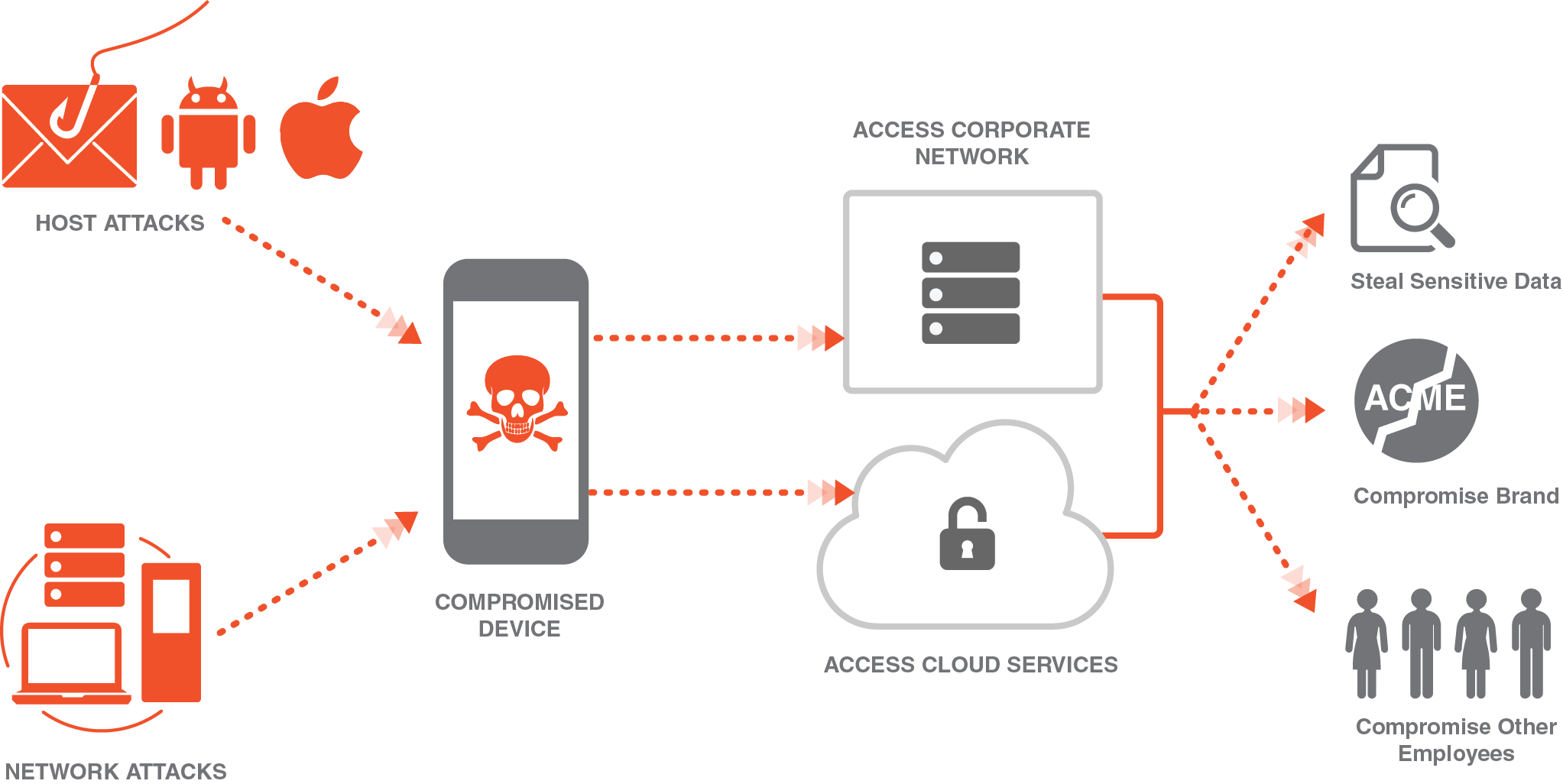
What Is a Mobile Threat?
The sophistication and continuous evolution of advanced threats is a serious problem for modern enterprises. Mobile malware, malicious apps, targeted data-stealing attacks on iOS and Android devices are introducing new challenges for IT security. Like viruses and malware that can infect your PC, there are a variety of security threats that can affect mobile devices. We categorize these mobile threats into host and network-based attacks. Advanced techniques, such as polymorphic engines or runtime binary encryption, can easily evade traditional signature-based security methods like mobile AV, and compromise a mobile device. Once the mobile device is compromised it can expose not just the device owner, but rather the entire corporate network and/and or cloud services the device connects to. If successful, the attacker can steal private information, such as contacts and passwords, and more importantly, enterprise data like customer lists and sensitive IP. One compromised device can jeopardize the organization’s brand and the employees who work for it.
While hacking has become increasingly difficult on traditional PCs, mobile devices are still relatively unprotected and enable hackers to pivot through these devices to access internal networks easily. Malicious actors are switching from attacking PCs to performing targeted attacks on employees’ mobile devices. The best defense strategy should focus on protecting the “front lines,” the mobile devices that are leading your business outside the company’s fortressed network.
Network-based Threats
Mobile devices are designed to automatically connect to the strongest signal – whether that be a cellular network or a local or public wireless network. Both connections can be compromised leading to a network exploit. Next generation attacks prey on iOS and Android devices traveling across public and private networks all over the world. Existing network security solutions lack the visibility required to protect mobile devices once they leave the corporate network, and in most case — inside the corporate network as well. Network exploits take advantage of flaws in the mobile operating system or other software that operates on local or cellular networks. Once connected, they can install malware on your phone without your knowledge. Many applications and web pages do not enforce proper security measures. Data can be intercepted and read by traveling between the device and the WiFi access point. Some popular examples of Network attacks on mobile devices include: reconnaissance scans, network traffic redirection attacks (Man-in-the-middle), SSL stripping techniques, rogue access points, and Rogue cell towers.
Host-based Threats
Host based attacks prey on the carelessness of users. Malware, spyware, malicious applications can post major security issues for mobile devices. Unsuspecting users can be compromised without their knowledge and attacks can silently collect private data, browser history, passwords, and worse – control over the mobile device. Vulnerable applications that don’t adhere to security best practices can be easily exploited for malicious purposes. The traditional Spear-Phishing approach that was used to hack many enterprises via PC, applies to mobile devices, too. Hackers will socially engineer an email to trick a user into opening a malicious attachment like .doc or .pdf file or clicking on a malicious link that contains a client-side vulnerability. Once the device is compromised, the attacker can connect to corporate resources using the device and leverage email, VPN and CRM access to lead to a massive security breach. Some other popular examples of host attacks on mobile devices include: malicious apps such as time bombs or self-modifying apps, OS and kernel exploits.
Detect and Protect Cyberattacks
Much like a doctor can diagnose an illness by analyzing the symptoms your body is exhibiting, Zimperium Mobile Threat Defense can detect both known and unknown threats by analyzing the behavior of a mobile device. By analyzing slight deviations to the mobile device’s statistics, processes, memory, CPU and other parameters, Zimperium can accurately identify not only the specific type of malicious attack, but the forensics that indicate who, what, when and how the attack occurred. Zimperium developed the revolutionary “z9 Behavioral Defense Engine” by training it over many years with proprietary machine-learning algorithms that distinguish normal behavior from malicious behavior on Android and iOS devices. Unlike cloud-based mobile security solutions that employ app sandboxing or tunnel all of your traffic through the cloud, the z9 engine sits directly on the mobile devices within the zIPS app, to provide complete protection around the clock.
Enterprise Mobile Security
Zimperium offers enterprise class protection for mobile devices against the next generation of advanced mobile attacks. Zimperium is the first and only company to provide a complete mobile security system that continuously runs on the device to provide visibility, security and management for iOS and Android devices. With its non-intrusive approach, users can be confident that their data and their privacy are protected at all times—both on and off the corporate network.
Contact us for a FREE demonstration.