Nicolás Chiaraviglio (@chiconara)
The GSMA Mobile World Congress, taking place every year in Barcelona, is undoubtedly the most important event for the mobile industry – with an average attendance of more than 100k people each year. Every important company is represented, with salespeople and high ranking executives taking the chance to eat local food, visit the always beautiful Barcelona, and …close important deals to boost their companies.

This represents a great opportunity. For everyone. Including hackers.
But there is not much to be concerned about, right? Salespeople don’t attend conferences with information on every potential customer they communicate with and C-level executives are not traveling with company secrets in their pockets. Right..? Oh, wait! They are all carrying their mobile phones… the most vulnerable devices!
These days, mobile devices hold tons of company information and a lot of our own and family personal data. That said, we are still not fully aware of the risks we face.
We protect our personal computers with antivirus, firewalls, VPNs, anti-spyware and every anti-X solution we can find. However, very few people do the same with their mobile devices, even though they are carrying extremely important information. Hackers also know this, making the mobile device the easiest attack vector to fully compromise an organization.
Most attacks start with the most used feature on a mobile device: the WiFi connections. Unfortunately, WiFi relies on mostly insecure protocols and standards, making them easy to impersonate or intercept, mislead and redirect traffic. This can be done independently on how new or updated your device is; it’s only related to how the underlying WiFi infrastructure works.
Many times you don’t even need to perform any action to start the attack. Do you remember that WiFi network you once connected to while visiting France, having a coffee at that international coffee franchise? In order to make your life easier, your device will connect to it automatically if it’s seen again. Even when it’s not the same network… it just has to claim to be it. And you don’t need to be a skilled hacker to perform such attack. There are a lot of tools available to do so, just to name a few, check the hak 5’s Pineapple and Bettercap which can be used in almost any laptop.
Everyday, Zimperium detects six hundred millions threat events. We process the most relevant network attacks to create what we call the Danger Zone – a real time map that can warn and prevent you from connecting to malicious WiFi networks.
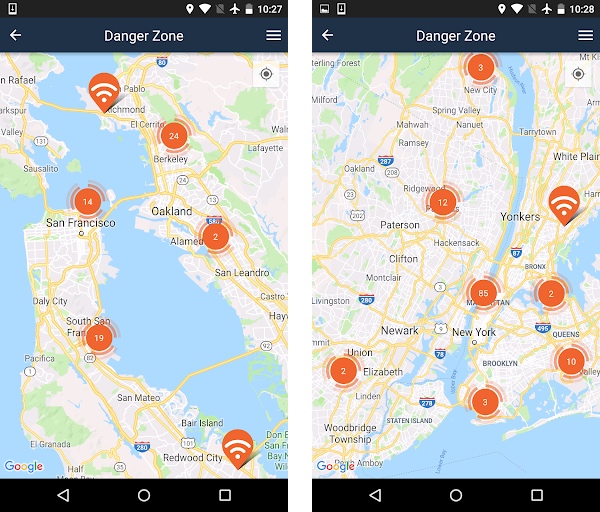
Before we dive into MWC’s host city, let’s check how the San Francisco and the New York areas look like on it :
Each WiFi sign is a location in which we detected (and prevented) an attack over a WiFi network during the last year. If the right information is collected, we can tag that network as malicious, being able to warn other users that attempt to connect to it. The information is condensed, and as an example – near Berkeley we find a circle with a 24 inside. This means that 24 networks are flagged as dangerous in that area. Zooming in we are able to get more detail about their location.
In this blog post, we’ll show you what Danger Zone can tell you about your next visit to Barcelona–for example when you attend MWC!
Landing at Barcelona El Prat Airport
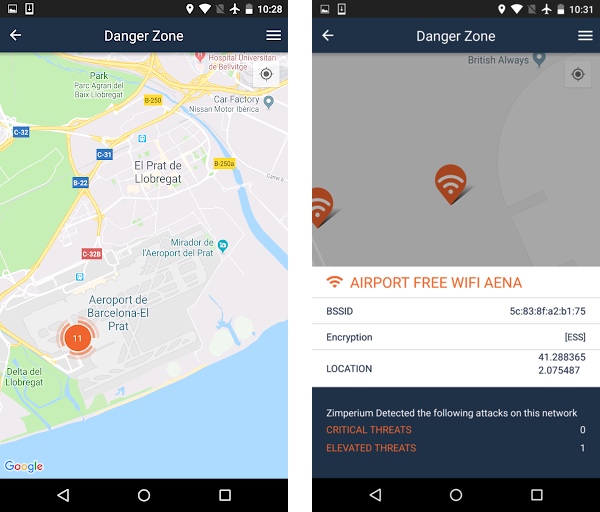
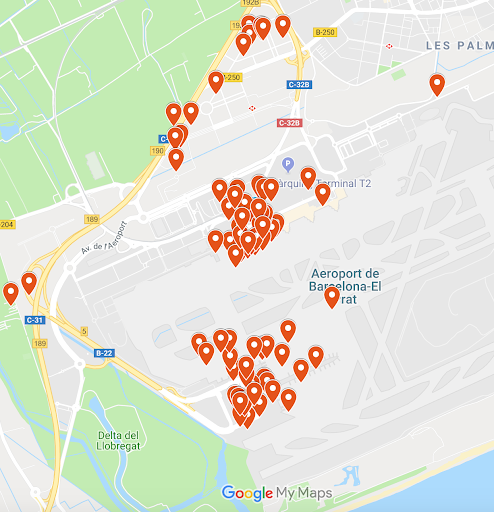
Airports are some of the most secure facilities in the world, aren’t they? When it comes to hackers, that doesn’t apply anymore. Just at the Barcelona airport alone, we detected 11 malicious WiFi networks. Most of them impersonate the legit WiFi of the airport, so if you’ve connected to it before, you won’t notice that something is happening.
But to be fair, Danger Zone will only show events with these current limitations:
- The attack took place less than a year from the current date.
- The severity of the attack must be what we call Critical or Elevated. This means threats in which the attack type can compromise the device.
- Full GPS location must be available from the attacked device.
Let’s remove limitation two (severity) and let’s create a new map with all the events we’ve detected at the airport.
To clarify what constitutes a critical or elevated threat, let’s think about different attack types. If an attacker is performing a scan to discover devices in the network, we will warn the user about this, but it doesn’t represent a critical threat on its own.
Once the attacker knows about your device, he/she can perform a “man in the middle attack” (routing all your traffic to his/her own device, thus being able to steal information). This will be considered a critical threat since personal information may be compromised. If a user is using zIPS, most attacks are prevented while the scan is taking place, but some attacks don’t start with one and we’ll get events with higher severity. So, let’s also add to the map the attacks prevented in an early stage.
The landscape looks like this:
Visiting the city
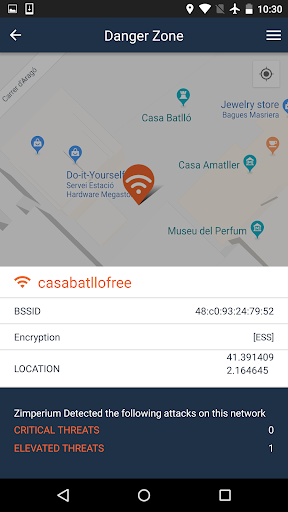
One of the reasons why Barcelona is such an interesting city is due to Antoni Gaudí‘s unique architecture style. You’ll be tempted to visit some of the buildings he designed, such as Sagrada Familia, Casa Batlló or La Pedrera. Most offer a WiFi connection for visiting tourists. Before using these WiFi networks, think twice:
We’ve also detected attacks on other locations frequented by tourists such as Sagrada Familia, La Pedrera, the casino, shopping malls, fast food restaurants, coffee shop franchises, museums, banks and even at Barcelona tour buses.
What about the MWC Venue?
As we stated before, Danger Zone only shows attacks with the limitations listed. This means most of the attacks during 2018’s MWC are not shown anymore (since those WiFi networks don’t even exist today).
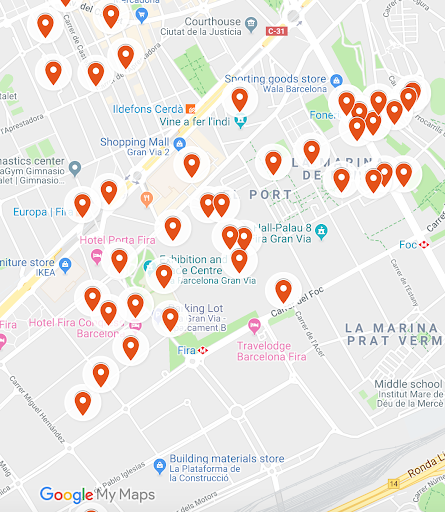
Anyway, let’s take a look at what happened last year at Fira Gran Via (the place in which MWC takes place):
Among the SSIDs of the detected attacks, we found: “#MWC18:pw=connectme”, “fb-MWC” and several other networks generated by private companies at the venue.
You’ve convinced me, I’ll stay in my hotel
Bad idea, mate. Hackers doing industrial espionage also need to sleep somewhere, and hotels are an ideal location to mess with the WiFi networks: plenty of people connected to mostly insecure networks. We found more than 40 hotels with WiFi attacks – we won’t show here any specific location for privacy reasons, but you get the idea by now.
Show me all
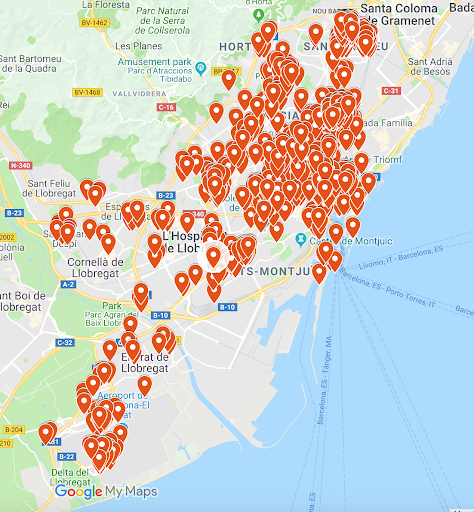
In case you were wondering how does the city look like if we show all the events we registered, it looks like the image below. There is not really too much left to see.
How can I protect my [self/enterprise/employees]?
Unfortunately, the fixes aren’t easy. And in the case of a company, every employee must follow the rules. If one employee doesn’t comply, the entire enterprise will be at risk. This is why working with the right mobile security solution is your best bet – – doing so ensures every employee – and therefore the business – is properly protected. That said, here are a few things users can do on their own to prevent these kinds of attacks:
- Configure devices to not connect automatically to known networks. This can be done easily on iOS, but on Android it has to be done for each network. A workaround is to delete known networks periodically.
- Don’t connect to open WiFi networks or networks using weak encryption protocols.
- Since users will likely ignore recommendation number two, avoid activities involving credentials (email, social media, bank, etc). This won’t prevent hackers from seeing traffic, but no credentials can be accessed by sniffing the traffic (although hackers are still able to perform other kinds of attacks like directing the user to a malicious website in which the user can be tricked to install malicious apps, etc,.).
- Use a VPN which will encrypt traffic and show an attacker a nice set of nonsense characters. That said, VPNs will not protect against malware detection, anomalies in processes, phishing attacks, device compromises and malicious profiles.
As with every year, we are attending MWC. If you want to hear more about us, go to our website: www.zimperium.com or contact: sales@zimperium.com
[1] https://www.mwcbarcelona.com
[2] https://blog.zimperium.com/our-most-vulnerable-devices-are-in-our-pockets/
[3] https://en.wikipedia.org/wiki/Evil_twin_(wireless_networks)
[4] https://en.wikipedia.org/wiki/Packet_analyzer
[5] https://blog.zimperium.com/detecting-krack-man-in-the-middle-attacks/
[6] https://en.wikipedia.org/wiki/Man-in-the-middle_attack
[7] https://shop.hak5.org/products/wifi-pineapple
[8] https://github.com/bettercap/bettercap
[9] https://blog.zimperium.com/zimperium-scales-billions-thats-b/
[10] https://blog.zimperium.com/identify-dangerous-wifi-danger-zone/
[11] https://en.wikipedia.org/wiki/Antoni_Gaud%C3%AD
[12] https://en.wikipedia.org/wiki/Sagrada_Fam%C3%ADlia
[13] https://en.wikipedia.org/wiki/Casa_Batlló
[14] https://en.wikipedia.org/wiki/Casa_Milà
[15] https://blog.zimperium.com/zimperium-wins-2018-cyber-defense-global-awards/