The Other MWC, Revisited
 Nicolás Chiaraviglio (@chiconara)
Nicolás Chiaraviglio (@chiconara)
(This post is a follow up of an earlier blog post)
Last week, we released a blog warning about how hackers leverage massive events like the Mobile World Congress (MWC) to attack high profile corporates to steal company data. We showed the network attacks we detected last year in Barcelona, which we used to create Danger Zone. There really wasn’t any place to hide; every conceivable WiFi network you can think of was attacked: tour busses, hotels, the casino, fast food chains, coffee franchises, restaurants, the airport, you name it.
Today is February 27, 2019 – three days into this year’s MWC, with one more to go – and more than 100 thousand people in the city, most without any Mobile Threat Defense (MTD) solution in their pockets.
In this blog, we will show you what happened in Barcelona from Saturday, February 23 to Wednesday, February 27 at 6 pm.
As a reminder, the data we are showing is based only on phones using the Zimperium’s zIPS app, the world’s first mobile intrusion prevention system app that provides comprehensive protection for iOS and Android devices against mobile network, device, phishing and application cyber attacks.
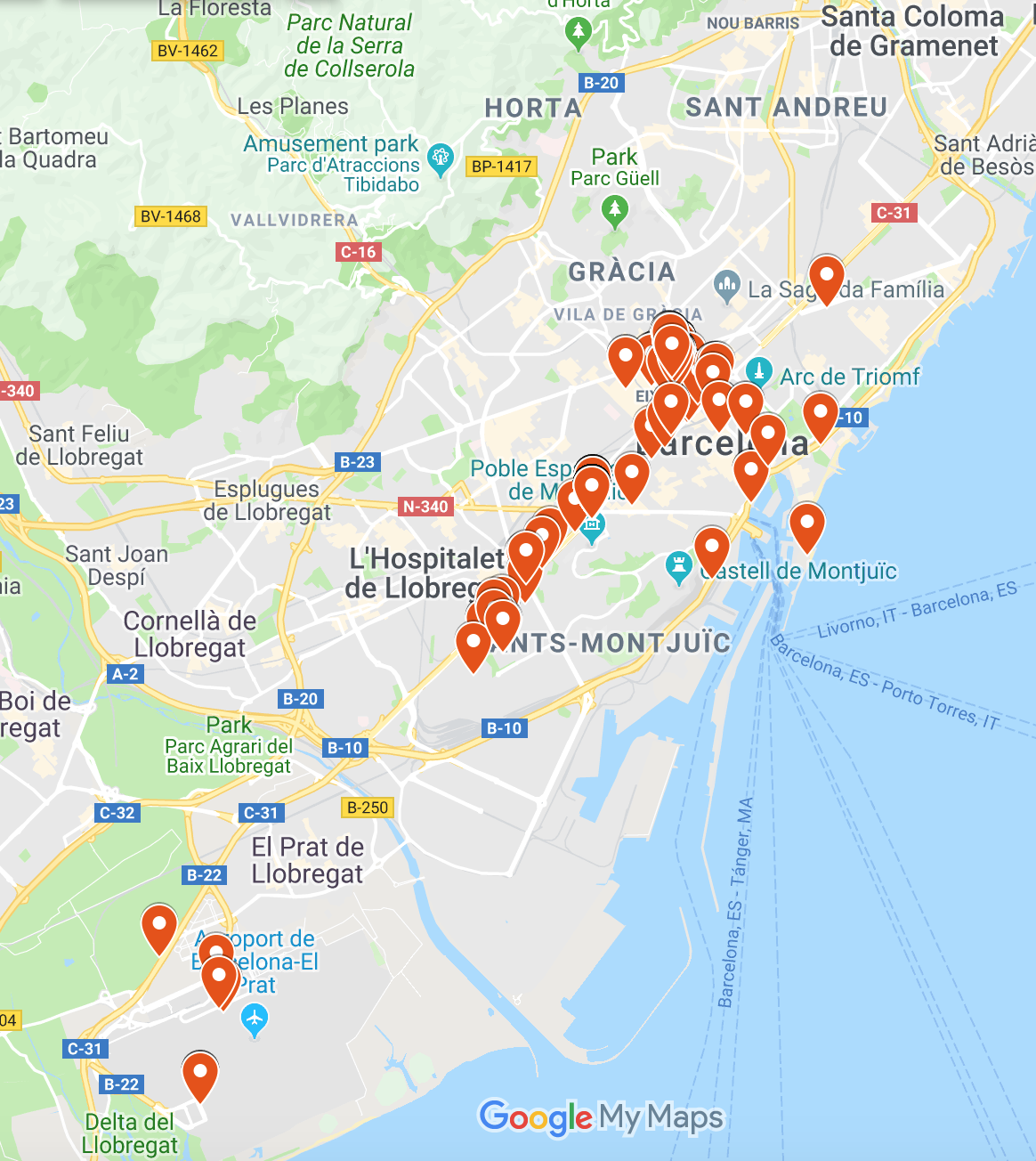
Let’s start with the whole picture. The map of the city with events we’ve detected looks like this:
Just like last year, we found several attacks at the airport, restaurants, tourist attractions, etc. We explained why confining yourself to your hotel would not be a good option to avoid attacks. In fact, going through the detected events, we found almost 25% of all detected events at MWC19 took place in hotels. What’s more, 70% of those events were detected in 5 star hotels.
Most of these attacks took place after 7 pm – meaning after MWC show hours had ended for the day, and folks were likely back in their hotel rooms. These were targeted attacks at individual hotels. Someone clearly had targets in mind. Fortunately for zIPS users, we were there to prevent the attack.
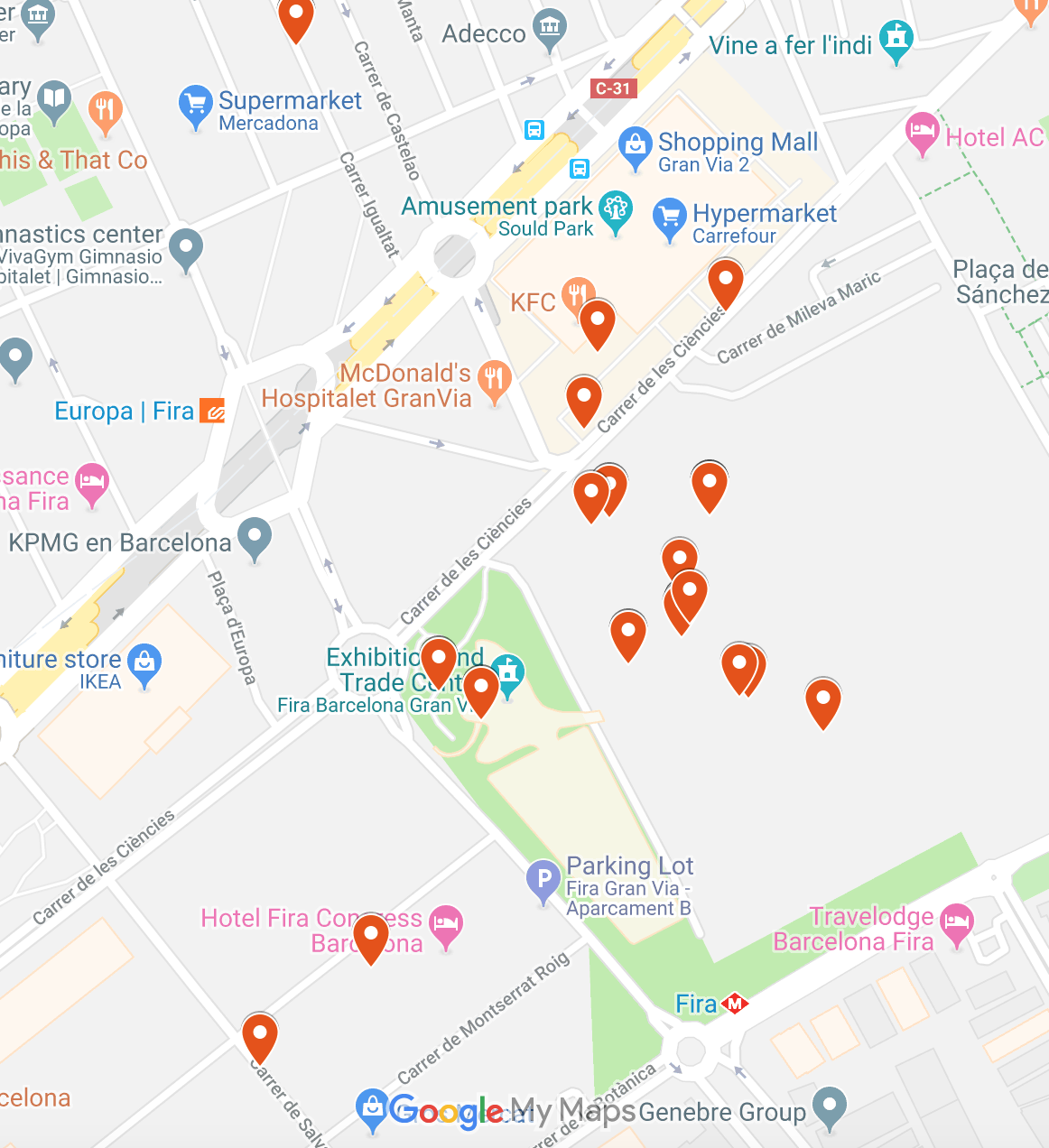
Let’s now take a look at the MWC venues. There are two locations related to this event: Fira Gran Via, which is where the majority of attendees are, and Fira Montjuic, a smaller venue. Let’s first take a look at Fira Gran Via:
We’ve detected attacks on the networks “MWC19:pw=connectme” (which is the open network that can be used by everyone attending the event), “EXHIBITION_WEB” (which is the network reserved for exhibitors) and some private networks such as “Express Wi-Fi by Facebook”.
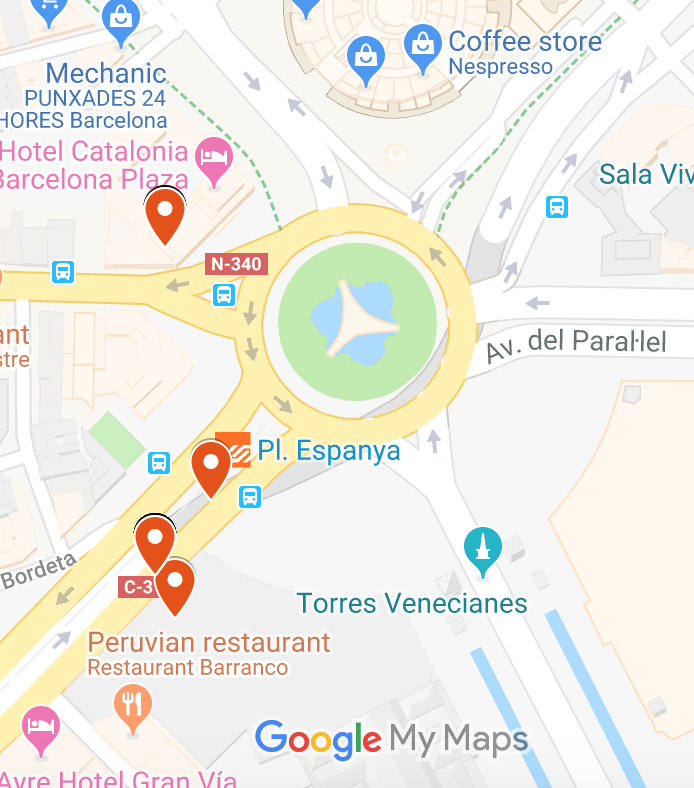
Fira Montjuic doesn’t look much better:
In this venue, the exhibitors’ network was also attacked.
So before you catch your breath, let’s crunch some numbers…
- In just 5 days, we’ve detected over 200 attacks;
- According to GSMA data, there are 5 billion mobile devices in the world, and approximately 3.7 billion of these have internet accessibility;
- Zimperium detection is installed on approximately 100M devices, this represents 2.7 % of all the total devices in the world. Keep in mind, we can only detect attacks if zIPS is installed on a device – – we’re blind elsewhere. Given this, it is fair to assume that we’ve detected only 2.7 % of the attacks that took place in Barcelona (I know, this really depends on how our devices are distributed and the types of customers we have, but let’s make a rough estimation…); and
- With these calculations, let’s estimate that 7400 attacks took place in Barcelona during MWC. And since we’re just making an estimation, let’s compensate for any overestimation by dividing this number by 2 (or even 10 for the skeptics), so let’s say there were 3700 (or 740) attacks in just four days in one city.
Friends, MWC isn’t over. We have 1 more day to go. Be safe. Use zIPS.