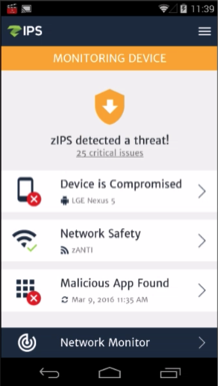
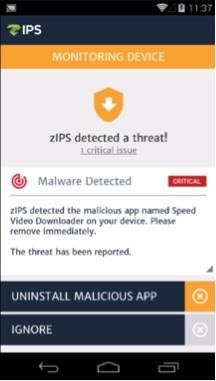
Triada is now the “umbrella” name for the three mobile Trojan families – Ztorg, Gorpo and Leech – that, as we mentioned before, primarily exploit users of Android 4.4.4 and earlier versions of the mobile OS. In this blog post, the zLabs team presents specifically the findings from our testing […]
Resources
Reflecting on Stagefright Patches
42.84% of Android devices tested are vulnerable to CVE-2015-3864. Although Google issued an update to the Hangout app that disabled automatic processing of media files, we know that CVE-2015-3864 can be exploited remotely and reliably via the browser. The number of Android devices is estimated to be between 1.4 and […]
Zimperium Expands Global Presence With Deutsche Telekom Partnership
We’re pleased to announce that Deutsche Telekom, one of the largest and most trusted telecommunications companies in the world, selected Zimperium to power a critical security initiative to secure millions of endpoints. Deutsche Telekom will use Zimperium’s technology to power Mobile Protect Pro, a new offering for business customers from […]
Triada Gets Tripped by Zimperium’s z9 Engine
Triada, a modular, stealthy and persistent Trojan targeting Android devices, was recently seen in the wild and reported on March 3, 2016. It, like so many others that we see daily, actively uses root privileges and operates silently to take over a device. Triada is primarily propagated through malicious applications […]
Zimperium Wins Cyber Defense Magazine’s ‘Best in Breed’ for Mobile Endpoint Security Award
We’re honored to announce that Zimperium’s Mobile Threat Protection solution won Cyber Defense Magazine’s award for ‘Best in Breed’ in Mobile Endpoint Security Solutions. Leading independent information security experts selected Zimperium as a winner after months of careful review and will be recognizing our solution at the RSA Conference in […]
Zimperium Enhances Mobile Threat Protection Suite, Adds Self-Protecting Apps
We are excited to announce that our 3.0 Mobile Protection Suite is now available and includes a brand new product called zIAP. The solution enables self-protecting mobile applications and 3.0 also brings new capabilities to our on-device detection technology, zIPS, and underlying threat management console, zConsole. The zIAP addition makes […]
Reflecting on Recent iOS and Android Security Updates
By:Zuk Avraham Follow Zuk Avraham (@ihackbanme)Joshua Drake Follow Joshua Drake (@jduck)Nikias Bassen Follow Nikias Bassen (@pimskeks) The last thirty days proven to be yet another exciting time for the mobile security ecosystem. Apple and Google released updates for their respective mobile operating systems that fix several critical issues — including […]
Analysis of iOS & OS X Vulnerability: CVE-2016-1722
By:Joshua Drake Follow Joshua Drake (@jduck)Nikias Bassen Follow Nikias Bassen (@pimskeks) Apple released iOS 9.2.1 update, the first iOS security update in 2016. As part of this update, Apple fixed code execution vulnerability in syslogd that was reported by Zimperium zLabs researchers Nikias Bassen and Joshua J. Drake. In this […]
Video: Zimperium takes over Nexus 6 using Stagefright
Just how safe is your phone from hackers? Our own zLabs VP of Research Joshua Drake and founder and chairman Zuk Avraham sat down with Crime Watch Daily’s Ana Garcia to show viewers just how dangerous hackers abusing the Stagefright vulnerabilities can be. One of the most common ways for hackers […]
Zimperium’s z9 Engine Detected the Recent Adware with Rooting Capabilities without an Update
Last week, a new strain of trojan adware was discovered, bearing automatic device-rooting capabilities that make it almost impossible to remove from affected Android devices. This malware, dubbed Shuanet is another example of increasing sophistication in mobile threats. Shuanet is the third family in a trilogy of recently discovered malicious […]
Mobile Security Updates
Recent Posts
- What Good Mobile App Security Visibility Looks Like: Discover What Lurks Within Your Enterprise’s Mobile Ecosystem
- Zimperium Positioned as the Leader in the 2024 SPARK MatrixTM for In-App Protection by Quadrant Knowledge Solutions
- Understanding IRAP: Australia’s Commitment to Upholding Best-in-Class Security Standards