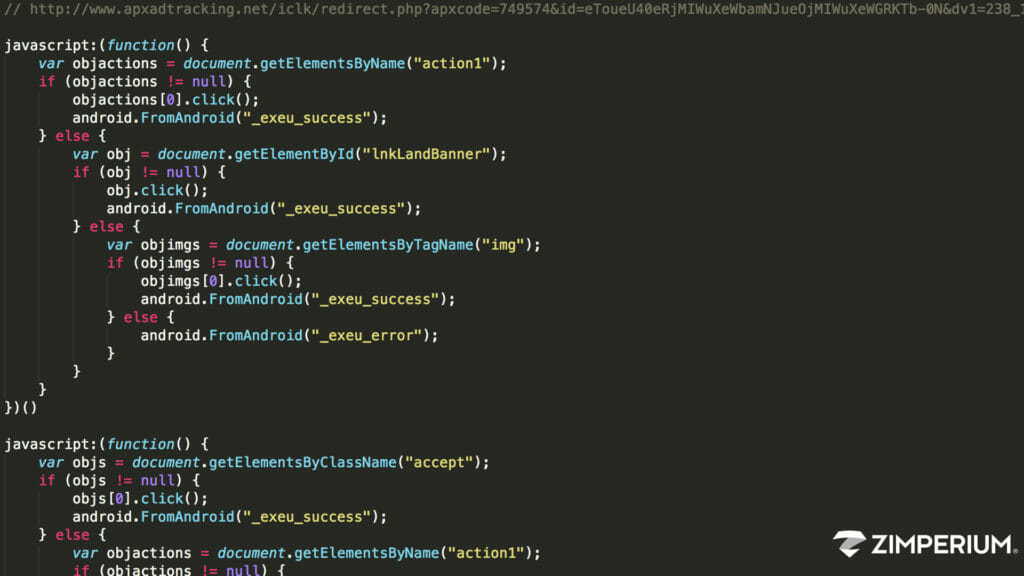
Cyber crime, like any crime, has its motives; each malware has its own malicious profit. Spyware spies on you. Ransomware demands a ransom to decrypt your private digital data. Phishing Malware phishes for your username, password or account numbers. Installation-fraud achieves fake software installations. Ad fraud fraudulently represents online advertisement […]
Resources
Detecting DoubleLocker Ransomware
What is DoubleLocker? Security researchers at ESET discovered a new ransomware infecting Android phones called DoubleLocker. DoubleLocker is an exploit that encrypts data on the infected device and then changes the device PIN to a random number. Victims remain locked out of their device unless they pay a ransom to the hackers. DoubleLocker spreads […]
Detecting KRACK Man in the Middle Attacks
What is KRACK? KRACK (Key Reinstallation attaCKs, KRACKs) is a serious weakness in the WPA2 protocol. WPA2 secures all modern protected Wi-Fi networks including those used by smartphones. Attackers within physical range of a Wi-Fi network can exploit protocol weaknesses by using key reinstallation attacks. The attack works against all […]
Validating Machine Learning Detection of Mobile Malware with Zimperium’s z9
Zimperium’s core machine learning engine, z9, has a proven track record of detecting zero-day exploits. We recently announced an extension of the framework that detects previously unknown mobile malware. This extension is known as “z9 for Mobile Malware”, and was officially announced in September 2017. Internally, the code name has […]
Zimperium Named a Leader in the IDC MarketScape for Mobile Threat Management
Zimperium has been positioned as a leader in the IDC MarketScape* on worldwide Mobile Threat Management Security Software. The IDC MarketScape provides a clear framework in which the product and service offerings, capabilities and strategies, and current and future market success factors of IT and telecommunications vendors can be meaningfully […]
MobileIron and Zimperium Create First Real Time Detection and Remediation for Mobile Threats
Zimperium and MobileIron are coming together and simplifying mobile threat defense. MobileIron will integrate with Zimperium’s machine learning based threat detection and provide a comprehensive security solution for enterprise customers. The integration of our machine-learning driven threat detection with MobileIron’s security and compliance engine provides enterprises with speed and scalability […]
Zimperium Mobile Threat Detection & Defense Available in Oracle Cloud
In recent weeks we have been discussing some of the ways Zimperium delivers mobile threat defense (MTD) at scale. As the only true enterprise-class MTD solution available, we take that role seriously. So we are pleased to deliver another option for enterprises to implement mobile threat defense and take advantage […]
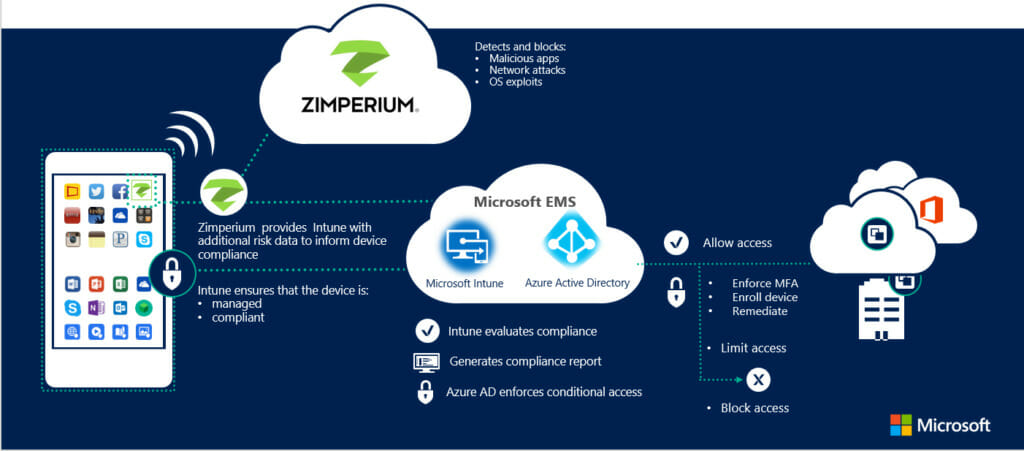
Mobile Threat Defense for Intune
Zimperium’s z9 technology and mobile threat defense is available for Microsoft Enterprise Mobility + Security deployments. Customers using Intune can receive threat intelligence from mobile devices and implement the risk-based conditional access policies popular with Intune deployments. John Michelsen has been leading the efforts with Microsoft and is excited to […]
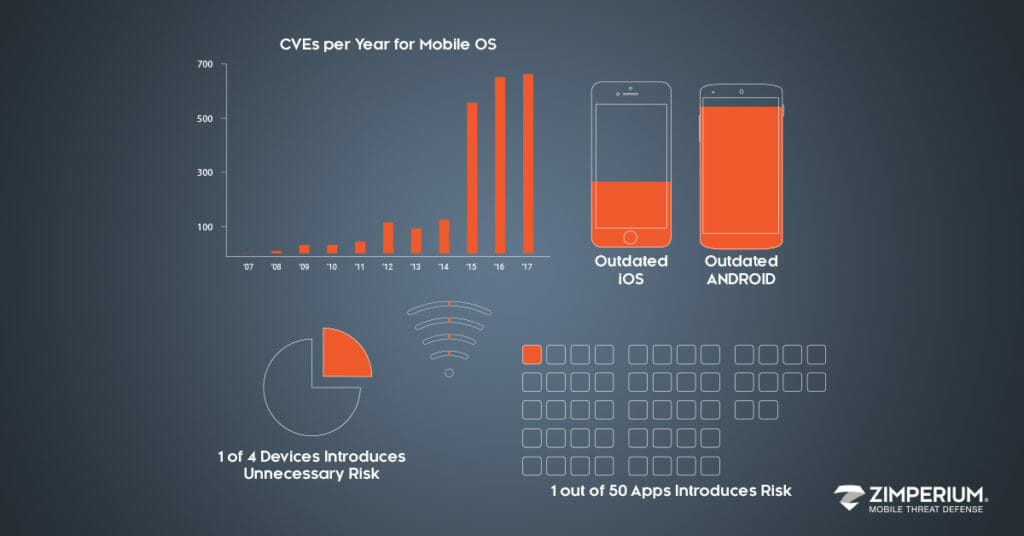
Mobile Threat Data Q2 2017
Zimperium is releasing its most recent summarized mobile threat data detected via our global enterprise customers. The data provides insight into what type of threats our customers are detecting by having the zIPS mobile threat defense app on corporate and BYO devices. zIPS enables companies to detect threats to mobile devices […]
Gartner Mobile Threat Defense and Enterprise Mobile Security Guide
“The signs are clear that mobile threats can no longer be ignored. Security and risk management leaders must familiarize themselves with mobile threat defense solutions and plan to gradually integrate them to mitigate mobile risks.”* *Gartner Market Guide for Mobile Threat Defense Solutions, Dionisio Zumerle, John Girard, 22 August 2017 […]