As Valentine’s Day approaches, love is in the air, and what better time to celebrate the perfect union between Mobile Device Management (MDM) and Mobile Threat Defense (MTD)? These two security solutions have found their match in each other, creating a bond that protects enterprises’ and employees’ sensitive information. Let’s dive into their love story and discover why MDM and MTD are truly better together.
The Foundation of Mobile Security: Mobile Device Management
Mobile Device Management (MDM) is a fundamental tool for overseeing or “managing” mobile devices within an organization. It operates at a foundational level, akin to a younger sibling in the hierarchy of mobile device security. Management solutions include Enterprise Mobility Management (EMM), which expands upon MDM by encompassing a broader scope, including managing applications and content across the mobile ecosystem. Unified Endpoint Management (UEM) represents an advanced stage that has evolved past MDM and EMM, as it handles the management of a broader collection of endpoints, spanning mobile devices, laptops, desktops, Internet of Things (IoT), and virtual machines (VMs).
Security frameworks like the National Institute of Science and Technology (NIST) SP800-124R2: Guidelines for Managing the Security of Mobile Devices in the Enterprise recommend integrating MDM, EMM, or UEM with a MTD solution to enable automated response to remediate detected vulnerabilities or quarantine apps or devices.
Now that we’ve explored the various mobile and endpoint management types – let’s focus on the foundational security MDM offers. Through MDM, IT administrators can configure, monitor, and manage employee-owned or corporate-issued devices remotely, ensuring compliance with corporate policies and security standards. The key advantage lies in scalability, as security teams and IT departments leverage MDM to install an email app pre-configured with the employee’s credentials, enhancing the user experience and reducing the workload associated with setting up corporate resources.
Think of it this way: the ultimate goal of MDM is to ensure that devices are in a more secure state and adhere to corporate policies before allowing access to corporate resources. For instance, if an employee’s device is identified as posing a higher risk than what is deemed acceptable by the security team, with an MDM installed, IT can take actions such as removing access to corporate apps and even remotely locking or wiping the device as necessary.
Striking the Balance: Reframing Mobile Security Strategies
However, the pursuit of effective management can lead to a pitfall: over-management. Security teams and IT departments fall into the trap of equating mobile devices with traditional endpoints and applying similar risk management strategies that result in excessive control. Even with features like manual blocking of URLs and web content filtering, there is still a heavy reliance on human judgment to determine what should be blocked. Mobile devices require a more nuanced approach to security that addresses the unique threats and challenges encountered in the ever-evolving mobile landscape.
The Vigilant Guardian: Mobile Threat Defense for Multi-Layer Security
But where does Mobile Threat Defense (MTD) fit into this relationship? MTD is the vigilant guardian, specifically designed to safeguard mobile devices – and the access they provide – from a variety of risks and threats spanning device exploits, network vulnerabilities, app attacks (such as malware), and phishing attempts. Using threat intelligence, MTD identifies threats and attacks that evade conventional security policies, improving the security posture of enterprises.
MTD does more than protect against known attacks like malware and network intrusions; it excels in detecting suspicious behaviors that could indicate a compromise, improving threat visibility. For instance, it can assess apps, pinpoint risks, and notify administrators where the app sends data, what vulnerability or CVE it has, and permission abuse. MDMs can’t respond to threats, but MTD can block content based on categories and more, providing full spectrum phishing protection.
MDM + Zimperium = Comprehensive Mobile Security
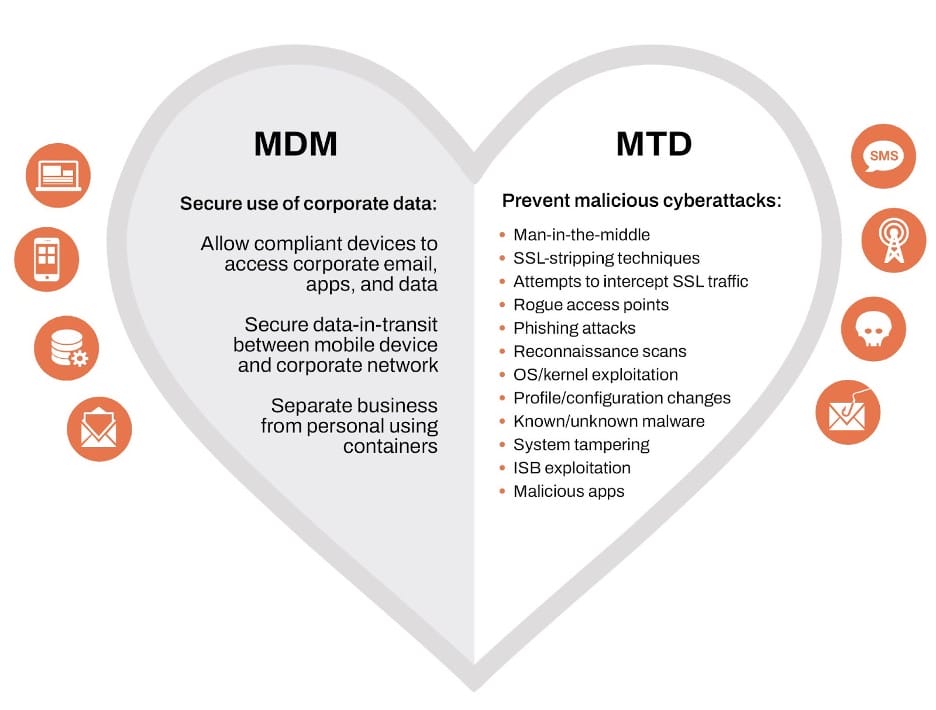
Together, MDM and Zimperium MTD can simplify mobile security for enterprises. Additionally, no user interaction is required to achieve comprehensive mobile security on enrolled devices across the enterprise. Organizations are able to protect corporate data, meet compliance standards, and achieve 100% user adoption, ensuring employees stay protected from mobile risks.
All administration is conducted within Zimperium’s Mobile-First Security Platform™, eliminating the need for local servers or connectors to deploy and manage policies. Furthermore, policy-based compliance actions assist security teams in notifying users of risky behaviors, restrict access to corporate resources and apps (complementing zero-trust architecture), quarantine devices to protect corporate apps and data and erase all provisioned content and settings when necessary.
By integrating MDM and MTD, teams enhance their visibility and control over mobile security. With access to dashboards and reports, they can effectively increase awareness of device, OS, network, and application risks, enabling prompt and efficient responses to emerging threats.
Benefits of Securing Enterprise Mobile Devices with Zimperium
Zimperium Mobile Threat Defense (MTD) is a privacy-first application that seamlessly integrates with UEM, EMM, and MDM solutions to provide enterprises with comprehensive mobile device security. It is designed to provide security teams and IT departments with mobile vulnerability and risk management, valuable insights into the risk of mobile applications, and threat protection to secure employee-owned and corporate-issued devices from advanced persistent threats across device, network, phishing, and app risks.
Once deployed on a mobile device, Zimperium MTD protects the device against all primary attack vectors, even when the device is not connected to a network. As the mobile attack surface broadens, so does Zimperium’s On-Device Dynamic Detection Engine. With Zimperium MTD, incident response teams finally have visibility into mobile threats and risks through integrations with SIEM, SOAR, and XDR systems. The unmatched forensics provided by Zimperium MTD prevents a compromise from becoming an outbreak.
How do we solve the problem?
- Detection: Device, Network, Apps, and Phishing threat detection
- Visibility: Proactive visibility into risk postures and vulnerabilities
- Remediation: On-device remediation and UEM-driven compliance
- Threat Intelligence: Deep forensics for Threat Hunting and Incident Response
The Perfect Match: Zimperium MTD Integrates Seamlessly with MDM
In the spirit of Valentine’s Day, let’s celebrate the relationship between MDM and MTD. Adequate mobile security isn’t just about defense; it’s also about communication and collaboration. While MDM primarily focuses on device management, MTD offers the threat intelligence needed to automate security for the mobile-first business. With this dynamic duo, enterprises can confidently navigate the ever-changing landscape of mobile technology, knowing that together these solutions are stronger, safer, and infinitely better.
To learn more about Zimperium Mobile Threat Defense and integration with your Mobile Device Management solution, contact us today.



