Mobile banking is a killer mobile app. We can now easily move money from one account to another to pay bills, credit vendors and send cash to friends and family. In previous years these transactions required tellers, checks and nightly batch runs in the bank’s back office. Now with the ubiquity of mobile banking, customers expect this to happen at a moment’s notice and without any issues.
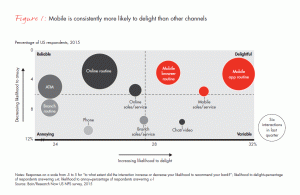 According to a report from Bain & Company in late 2014 ¹, the number of banking sessions when a person “visited” their bank took place on a mobile device 30% of the time. This will only increase as banks move more transactions to mobile to reduce costs and decrease customer churn. A recent 2015 survey from Bain & Company found customers that frequent branches are three times more likely to switch banks. A branch visit is twice as likely to annoy a customer than a mobile interaction². All points lead to mobile to lower delivery cost, reduce customer churn and increase customer delight.
According to a report from Bain & Company in late 2014 ¹, the number of banking sessions when a person “visited” their bank took place on a mobile device 30% of the time. This will only increase as banks move more transactions to mobile to reduce costs and decrease customer churn. A recent 2015 survey from Bain & Company found customers that frequent branches are three times more likely to switch banks. A branch visit is twice as likely to annoy a customer than a mobile interaction². All points lead to mobile to lower delivery cost, reduce customer churn and increase customer delight.
This shift enables Chief Digital Officers, in their customer engagement role, to increase the level of service personalization by using data from the customer’s mobile device. However, this also increases the threat of criminal activity since transactions can now take place anywhere on almost any device and regardless of the state of the device.
A threat disclosure earlier this year, re-discovered a malware targeting mobile banking users in Australia, New Zealand and Turkey. This mobile trojan, dubbed Android/Agent.Spy.SI, targets users of 20 different banking applications to steal login credentials. After the malware is installed on a user’s device the attack interrogates the device to specifically look for banking apps. If such an app is present on the user’s device, attackers place an overlay on the app to capture credentials when the user types in a username and password. Once the credentials have been captured the crime ring logs in to steal funds. Users do not notice the attacks until they get their banking statement or an email from the bank.
The technology shift creates risks
The security of the interaction resides entirely with the app provider — the bank. Users download the app, run it on brand new, jailbroken, rooted or unpatched devices to interact with the bank. They aren’t paying attention to the integrity of their device. Interactions with your financial institution rest solely on the app that the bank provides and users will blame the latter if anything goes wrong.
If users notice transactions on their account they claim were not initiated by them, they file a complaint. They claim, for instance, a $500 withdrawal is not theirs and the bank is to blame for a “glitch” in the system. Depending on the value of the customer, this $500 could be back in the user’s account on the same day. The bank has then placed a $500 fraud claim or written the entire amount off as a loss. Either way the bank loses.
Banks are on the hook for fraud originating inside their mobile app
We are speaking of the most current mobile banking threat disclosure but this is just the beginning. On an average mobile device, how many apps are connected to or contain financial or credit card information?
Anything going wrong inside an app exposes the consumer to inconvenience, but it also exposes the company producing the app to fraud. It is the responsibility of the Chief Digital Officer or the executive in charge of the mobile channel to understand the consumer use case, as well as potential policies that could be enforced.
Just as banks have fraud detection mechanisms for debit or credit cards, it is also their Chief Digital Officers’ role to provide fraud detection and protection in their apps. The number of variables and use cases, however, represent too many scenarios to keep up with, but there’s one exception: you can control your app. You do control the functions and the security model in your app. You owe it to yourself and your company to eliminate fraudulent transactions via mobile interactions.
This isn’t someone else’s issue. Unlike telecommunication providers, for example, who can offer basic security through a partner, the responsibility lies with the bank and must be integrated in the Chief Digital Officer’s strategic-planning process..
A Solution Exists
The latest attack targeting banking apps is solvable. Technology exists that detects the threats acting on your mobile banking users if you provide it in the app.
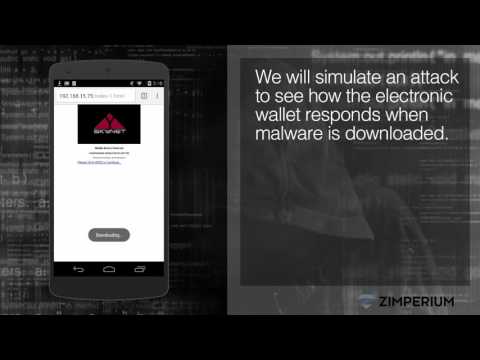
zIAP provides threat detection and remediation logic to protect your app from criminals. This benefits you and your consumer. The threat detection technology uses machine-learning algorithms to determine abnormal activity on the device when your banking app is running and reports back to you. If it detects an anomaly or foreign object, it simply closes itself like a clamshell and performs no other transactions until it’s repaired. When all of your customers are running this version you get the benefit of seeing the attacks at first strike instead of having to investigate fraud. Below is an example of the embedded threat detection capability in using an open-source ewallet app.