
Whether it’s on the trade show floor, at the conference center, hotel or local restaurant, mobile device usage is particularly high, with attendees, and oftentimes devices, constantly trying to connect to the different networks. Ironically, that includes industry events whose primary purpose is to share knowledge on, and bolster, security measures. In other words, conferences where fighting attackers is top of mind.
One of the highest-profile mobile trade shows – the RSA Conference in San Francisco – highlights the opportunistic approach hackers take. With security as either the primary topic or one of the primary topics at these events, you might think that the plentiful security expertise would result in a fairly hacker-resistant experience for attendees.
That thinking, though, is wrong.
In fact, the opposite is true, especially for threats to mobile devices. The density of threats tends to skyrocket at events like RSA. Let’s look at the numbers we observed at the last two RSA conferences.
Walking in the Danger Zone
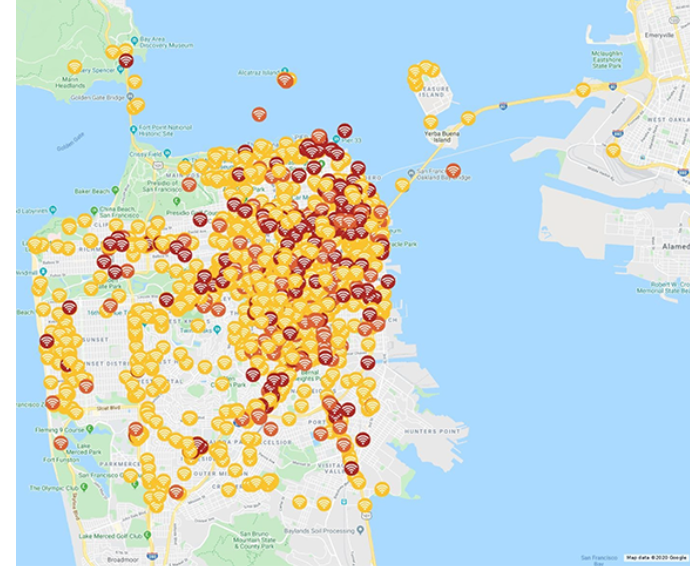
Zimperium’s Danger Zone is a real-time map that shows malicious private and public Wi-Fi networks. Danger Zone numbers are generally conservative since the data we are showing is based only on mobile devices using Zimperium’s zIPS app.
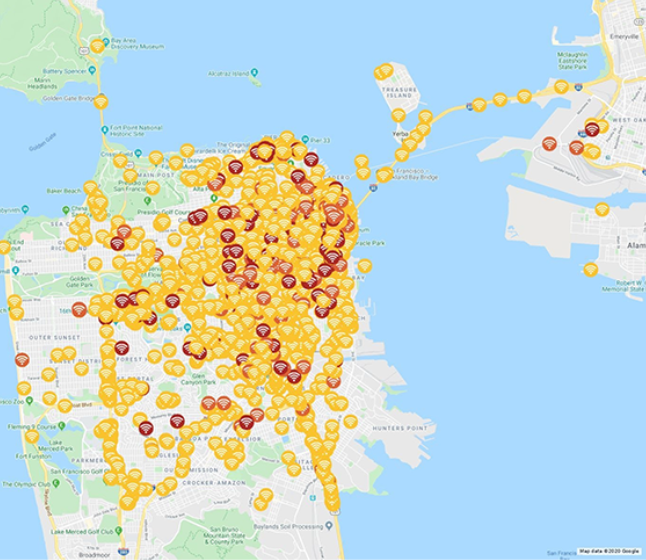
During the RSA Conferences in San Francisco we identified 6,208 threats April 16th – April 20th 2018 and 13,353 threats March 4th – March 8th 2019.
April 16 – April 20, 2018
March 4 – March 8, 2019
Breaking Down the Threats
Since not all threats are equally dangerous, we break the total numbers of threats into three types of levels: low, elevated and critical. This is the breakdown:
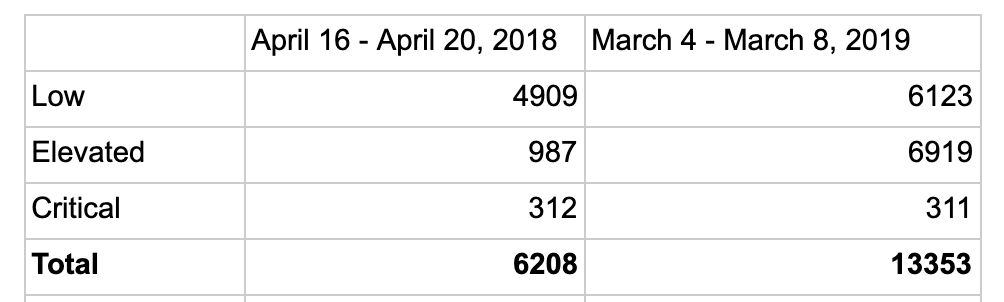
Here’s what each event means:
![]() LOW: Low threat events are, for example, network scans. A network scan is a device inspecting IP addresses on the network to find active devices connected to it. It’s not a problem on its own, but it is a technique that attackers use to find potential victims. While there is no real compromise to the device itself, it’s a sign you should probably disconnect from that network.
LOW: Low threat events are, for example, network scans. A network scan is a device inspecting IP addresses on the network to find active devices connected to it. It’s not a problem on its own, but it is a technique that attackers use to find potential victims. While there is no real compromise to the device itself, it’s a sign you should probably disconnect from that network.
![]() ELEVATED: An elevated threat is, for example, if you are indeed connected to a network that we know presents attacks. This means the user ignored the first warning and moved further. Again, this doesn’t mean the device is compromised, but that the device was used in a potentially harmful situation.
ELEVATED: An elevated threat is, for example, if you are indeed connected to a network that we know presents attacks. This means the user ignored the first warning and moved further. Again, this doesn’t mean the device is compromised, but that the device was used in a potentially harmful situation.
![]() CRITICAL: A critical threat is when we know someone is compromising the data coming from the device. For example, someone is performing a man in the middle attack (MiTM), which means a hacker is routing all your traffic to his/her own device, and thus is able to steal information. Incidentally, zIPS detects MiTM attacks in about a second, which is not enough time for an attacker to get any useful information.
CRITICAL: A critical threat is when we know someone is compromising the data coming from the device. For example, someone is performing a man in the middle attack (MiTM), which means a hacker is routing all your traffic to his/her own device, and thus is able to steal information. Incidentally, zIPS detects MiTM attacks in about a second, which is not enough time for an attacker to get any useful information.
How to Stay Safe Using Public WiFi
What will the 2020 RSA Conference hold? There will be low, elevated and critical threats. Guaranteed.
But what can be done to lower the numbers?
There are private and public WiFi security solutions available. If adhered to, they will help ensure you are connecting to a legitimate WiFi. That said, they will not protect against a host of attack techniques. These attack techniques range from malware detection to anomalies in processes to phishing attacks to device compromises and malicious profiles. Your best best is working with the right mobile security solution. This ensures every employee – and therefore your company – is properly protected.
That said, here are a few things users can do on their own to prevent these kinds of attacks:
- Configure devices to not connect automatically to known networks. This can be done easily on iOS, but on Android it has to be done for each network. A workaround is to delete known networks periodically.
- Don’t connect to open WiFi networks or networks using weak encryption protocols.
- Since users will likely ignore recommendation number two, avoid activities involving credentials (email, social media, bank, etc). This won’t prevent hackers from seeing traffic, but no credentials can be accessed by sniffing the traffic. That said, hackers are still able to perform other kinds of attacks. Attacks like directing the user to a malicious website. In this instance, the user can be tricked to install malicious apps, etc.
- Use a VPN which will encrypt traffic and show an attacker a nice set of nonsense characters.
For those attending RSA, Zimperium will be at Exhibitor Booth 3230, providing in-depth look at industry-leading research, mobile device security solutions and mobile app security solutions. To meet exclusively with the Zimperium team, schedule a time.
Contact Us
To learn more on how Zimperium delivers protection against device, network, phishing and malicious app attacks, please contact us.



