By:Nikias Bassen
Follow Nikias Bassen (@pimskeks)
An enterprise security vendor, Palo Alto Networks, followed up on a threat discovered by Cheetah Mobile and Qihoo360, and identified a malware spreading through social media and other channels. This malware, named YiSpecter, is abusing enterprise code signing to trick the user into installing a malicious app. Following Zimperium’s investigation, we have not observed any ‘never-seen-before’ tricks in this malware and the main infection point is through social engineering. In the original blog by PAN it appears that ISPs are helping to spread out this malware – we could not verify this claim at this time.
The YiSpecter is abusing a signed enterprise certificate of “Beijing Yingmob Interaction Technology Co., ltd.” to deploy the malware, which is not part of the official iOS store.
At Zimperium zLabs, we created a command line tool for OSX and Windows to remove any known instances of YiSpecter. You can download the tool for free here:
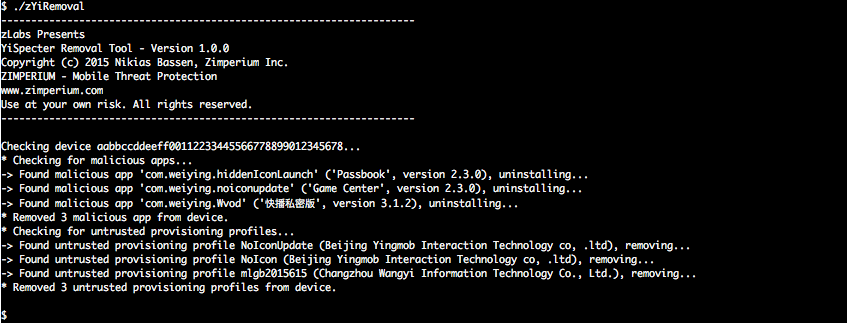
To use the tool plug your infected iOS device and simply execute it from the terminal:
./zYiRemoval
zYiRemoval will enumerate all connected devices and perform the administrative actions to remove malicious apps and profiles planted by YiSpecter.
It is advised to take the following steps to ensure that you are not impacted by YiSpecter:
Upgrade to iOS 9.0.2 as soon as possible.
If you were impacted by zYiSpecter, use zYiRemoval to uninstall the following profiles / apps, or perform this steps manually.
Uninstall any of the following profiles:
- “Changzhou Wangyi Information Technology Co., Ltd.”
- “Baiwochuangxiang Technology Co., Ltd.”
- Beijing Yingmob Interaction Technology Co., ltd.
If you any of the apps below installed on your device, delete them:
- “情涩播放器”
- “快播私密版”
- “快播0”
- HYQvod (bundle id: weiying.Wvod)
- DaPian (bundle id: weiying.DaPian)
- NoIcon (bundle id: com.weiying.hiddenIconLaunch)
NoIcon silently installs two additional malicious apps “ADPage” and “NoIconUpdate”.
- ADPage (bundle id: com.weiying.ad)
- NoIconUpdate (bundle id: com.weiying.noiconupdate)
Do not install profiles from unknown developers – be extra careful when typing your pin-code: iOS asks you to type your pincode before installing new profiles.
C&C IPs
According to the original analysis, YiSpecter uses these subdomains:
- iosnoico [dot] bb800 [dot] com: used to upload information, download configs and commands, download – currently responds to: 182.254.147.109
- qvod [dot] bb800 [dot] com: used to download main app – 182.254.131.13
- qvios [dot] od [dot] bb800 [dot] com: used to download main app – 182.254.131.13
- dp [dot] bb800 [dot] com: used to download promoted iOS apps – 182.254.145.194
- iosads [dot] cdn [dot] bb800 [dot] com: used to download promoted iOS apps and malicious components – 112.90.51.173
We are currently in the process of notifying all of our customers if any instance of YiSpecter is found and we are taking action to ensure that our enterprise customers are protected.
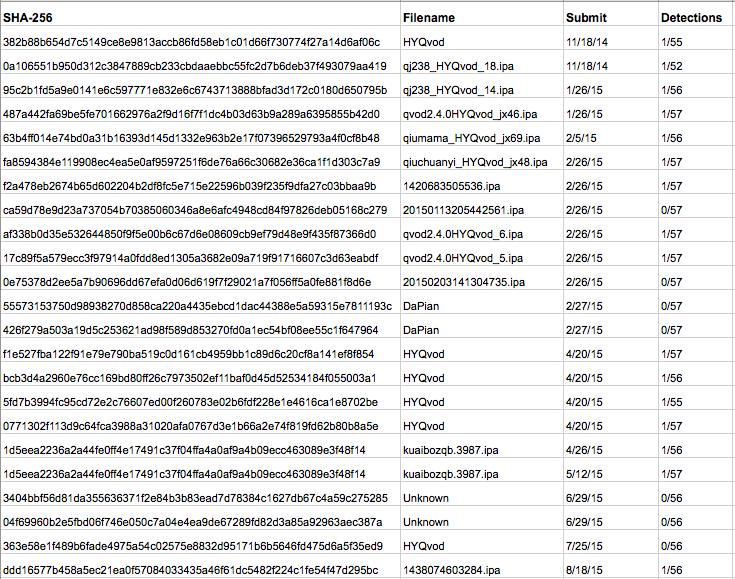
Additional IOCs:
Samples of YiSpecter from the original analysis:
57cc101ee4a9f306236d1d4fb5ccb3bb96fa76210142a5ec483a49321d2bd603 ADPage
4938b9861b7c55fbbe47d2ba04e9aff2da186e282f1e9ff0a15bbb22a5f6e0e7 ADPage.ipa
fc55c5ced1027b48885780c87980a286181d3639dfc97d03ebe04ec012a1b677 DaPian
5259854994945a165996d994e6484c1afc1c7e628cb5df2dc3750f4f9f92202e DaPian.ipa
7714dbb85c5ebcd85cd1d93299479cff2cc82ad0ed11803c24c44106530d2e2f HYQvod
ddd16577b458a5ec21ea0f57084033435a46f61dc5482f224c1fe54f47d295bc HYQvod.ipa
8fa135fc74583e05be208752e8ce191060b1617447815a007efac78662b425d0 HYQvod_3.3.3
526e1dc893629c00c017fbe62b53392cb26bc6b15947e7b8b7df10a62f40cbad HYQvod_3.3.3.ipa
41176825ba0627f61981280b27689a0c5cc6bfb310a408fa623515e6239b8647 NoIcon
98e9e65d6e674620eccaf3d024af1e7b736cc889e94a698685623d146d4fb15f NoIcon.ipa
e7f071929a4304447cf638057d9499df9970b2a3d53d328a609f191a4bc29ffd NoIconUpdate
8873908061f9c8d563de26fe6fa671080a90a2d60f795cc0664ef686e1162955 NoIconUpdate.ipa
Samples in VirusTotal