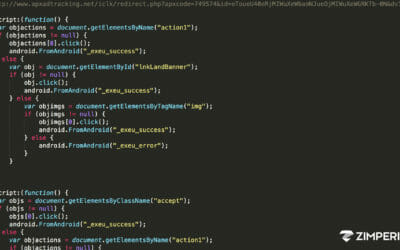
Background:
On June 28th, Zimperium zLab researchers observed that Joe Sandbox published a tweet that mentioned an application package file (APK) that could not be analyzed from most of the anti-decompilation tools, but could be installed on Android devices whose OS version is above Android 9 Pie (API 28). This sample uses a technique that limits the possibility of decompiling the application for a large number of tools, reducing the possibilities of being analyzed. In order to do that, the apk (which is in essence a zip file), is using an unsupported decompression method.
This technique is not new. In fact, a 2014 paper, “Leaving our ZIP Undone: How to Abuse ZIP to Deliver Malware Apps”, demonstrated how the compression algorithm (method) used in an APK could be tampered in order to remove automatic script analysis and hinder static analysis. This field (compression method) is a 16-bit field, meaning that 65,536 methods can be defined.
However, Android’s APK, which uses the ZIP format, supports only two compression methods. One is without any compression, i.e. the STORED method (0x0000), and the other is the DEFLATE (0x0008) compression algorithm. Depending on the Android version, the default behavior for unknown or unsupported methods differs:
- In Android 4.3 and below, Java ZIP-handling code checks against the method being DEFLATE, and assumes that the STORED method has been used if it does not match.
- In versions greater than Android 4.3, Android ZIP-handling assumes the compression method to be DEFLATE if the method specified does not match with STORED.
In Android versions below 9, applications using unsupportedunknown compression methods are not installable, but they work properly on versions above it. Similarly, many tools used for the decompilation and analysis of Android applications were not able to handle these samples as shown in the following pictures:
JADX
APKtool
Some decompressor tools (e.g., MacOS Archive Utility tool) cannot unzip the APK or ignore important files needed for the analysis such as AndroidManifest.xml.
Another tool, JEB added support in its last version to support this bad compression method.
On top of this technique, we identify further corruptions to the APK files in order to prevent analysis tools from running properly. These techniques are:
- Filenames with more than 256 bytes:This technique is based on the differences between the standard of ZIP regarding the maximum size of a filename (0xFFFF bytes) and the maximum filename size in Android (0xFF). The sample with the sha: a8feda3a888751f9efd7223462381514a35910d0c7e92a8cc32f5b5c0bdc8271, has declared elements with filename bigger than 0xFF (0x1B6B).
The use of this technique generates that some tools such as apktool, or some zip decompressor crashed, when trying to decompile/extract this APK.
- Malformed AndroidManifest.xml file: The presence of malformed axml is a well known technique from malware authors in order to obfuscate information about the application.In the sample reported by Joe Sandbox (Sha-1: 0ad5289c6b7a438e3970149b183e74b89f534109), we identify some issues that are responsible of crashing some open-source decompiled tools ( Androguard…), during the AndroidManifest parsing.
- Malformed String Pool: The structure of the data contained of the string pool header in this apk is the following:
Immediately following the StringPool chunk header, is present the field stringCount [32-bit size]. The stringCount (954) field specifies the number of strings in the StringPool. The field stringsStart specifies the offset from the start of the StringPool chunk to the start of the string data in the body of this chunk. However, if there is a discrepancy between the content of the stringCount (954) and the number of indices (164) defined in the StringPool chunk body, this can cause certain tools to crash during the parsing of Android XML files.
Zimperium Detection:
Zimperium zLabs identified how many samples were using a manipulated compression method field. By running a retrohunt on public application repositories, we found 3,300 samples that are using an unsupportedunknown compression method in order to hinder analysis. Most of these samples are corrupted beyond the point that the OS is able to load them.
However, our team identified 71 malicious samples that the Android OS is able to load properly. None of these applications are currently available in the Google PlayStore and we do not have any evidence to support that they were at any point in time. For this reason, it’s likely that the distribution method was through third party stores or through tricking the user to sideload the app using some sort of social engineering or phishing attack.
Zimperium Customers:
Zimperium Mobile Threat Defense (MTD) customers are protected against these threats. Our dynamic on-device threat detection engine provides protection against malicious apps installed with this technique and others Additionally, Zimperium MTD’s enhanced phishing detection can prevent phishing attacks from being successful, stopping the whole attack chain from the initial attack vector.
Indicators of Compromise
Malicious applications that is using an unsupported unknown compression method :
- com.freerdplalobydarkhack.con
- package.name.suffix
- com.google.android.inputmethod.latia
- numeric.contents.desktor
- health.karl.authority
- charlie.warning.professional
- imperial.xi.asia
- turner.encouraged.matches
- insta.pro.prints
- com.ace.measures
- eyes.acquisition.handed
- xhtml.peripherals.bs
- com.google.services
- google.clood.suffix
- friends.exec.items
- com.deveops.frogenet.service
- com.yc.pfdl
- publicity.inter.brooklyn
- consist.prior.struck
- disaster.considering.illinois
- splash.app.main
- labeled.configuring.servies
- regarded.editors.association
- com.appser.verapp
- widely.sharp.rugs
- handmade.catalogs.urgent
- com.gem.holidays
- lemon.continental.prince
- com.koi.tokenerror
- cmf0.c3b5bm90zq.patch
- com.ilogen.com
- one.enix.smsforward
- com.app.app
- per.hourly.wiki
- com.mobihk.v
- com.gmail.net
- broadway.ssl.seasonal
- Fees.abc.laugh
- tjb0n81d.j9hqk.eg0ekih
- 9fji8.pgzckbu7.nuputk
- bullet.default.til
- factor.apnic.constitutes
List of Hashes:
- 8a81ae6b6e9d57e5a8488ff0e1531fd86434ea93dd3bc6d2d5b03be96b5f90fe
- 3ddd867f47ab3b822690fdf56e2159ee5315b0990a4a5758f032373139fcb1a9
- 0278ecf7616cdf0970a755027ea95ba6295f34e778d741c52c4fe9cae5c541b1
- 9a34f00048c729359c006f3e486cc0f1ba373a5eb01ee6c62de4baef6ed4af8c
- 1cf4dd2a7f4102d208c54cf7ee7f5df9af3393ce3f87379040af28868de4829d
- b9af1bf509480059449f9166e048003c8f03f8d64ea8a6fb517b866512a0b755
- ebe384dfe8d4f8d23faa1ed07a40c72e0d6eff848ed963b0536e5264a875bd92
- a77f3cfac151fc7fa263febcec64bde20d8f176dcd8da512bb668e01b9ca2602
- b8200525622b1fab3245a076018aea18a613f4b64e9ae4969ed49c875c87bc3e
- 27279b62d681b7ebe46e0f7bae75e1c6e64e52819f72a33b0a8dcbd80363cdf0
- 1cab0e8d2c1a8665bf293b4046663ab9fda7158883b19087e7c4fa56fd01acf3
- 00c23ff1949927c7517b0876d7e64e186be28f853fec09662e3abda1da60876a
- ab390ed662e29cba27e6da2f1ecef53cb31959170e763fdd88b2f5f5bb3db6bd
- 37cdf1d157b4084c463b079cf80b581b3a8d1e0f9ed1fb51ef6753f31d44bb8e
- e02dee1e52c3ec5076a23ce0d8b0157c045e292caa67c92a4ff2111ecaa91b78
- 85f486f81c07e541470695e8ec79ca4c773e3aad323bd5778814cbf85fa7eecf
- 8db53e9532bb550d0ee6128fe24ceaf133b5234b9c418bbc96a255ad485e0756
- c49c5ef4107aa2dd4c2684186a2c683177a7376230042b3dfbf3623ebbf9c387
- 639cdfbfc0effd6ecd7cd676f75edf11d1dc0d73c0f3f1e9387a754de9e23095
- 767dd5b31ce22f22500212ee7c3a0856bb61b0c63a8880c399d872b7d3cfca2c
- fb60c55633bcc7c1242942deb284b7d9dd9590aaf260e4fb4b57096b06e1e2fb
- 0d3cdb83edb8ff6ecf37e6dcf47971b1b992938fe03749cf3c689f5dbda23960
- 62493226f475c82919e26cfefb41dd35ecb5d01b493ed5fd204fbc8f35956fe2
- b258643133127df87ca13549d6d23a7fc945a3a9789babee9e68984c25ca6067
- 62175d88487a524066b4583cb139811efe8d2762e0d38354f65d95241c7f035e
- 2ee5583720184a714f5002e122132da61a024feb4eae8241a44077b38b1fc422
- fdd5abde9b92d90814602718e11c8a4eaa4974fcbffbd17b23730c697d7f516a
- 7b376a08c56cc6439c96cab3be0445c9b130c6df61fa76afefe11f68af18e7f4
- f23f87fa2c53c337c453a1ef6e0f9a55d8b7b747075ee8c27f70a72b5bfa1246
- 16494248965138f07512793215c59bfdb8ea123135c44965c40ebb75bc589fb9
- 29d36ea8fafbda1e16633a95b39a94b2ad1302cfb0488f8b016973d20cce23b2
- ca9c13c45e1debada4674d72458432f7829ec72a92c2969999b7b5c2212ca6c5
- 341640b3b2b4bf83a656c509587eefd4d7204725e5be7943588572b9664bf0b7
- 8621541ac0cbb1b31d21099deea91a198ab144bfb04b0b62814a5a916f0b8313
- 43f1b6c8913129f0307e655beb0b43cbca8ec060f22923b78490f430caed8c45
- 12e06e546a46ca7674dd0b49fb5b80f3d8806003cc0abafcc8b1e586daf23074
- 5a3f1331b8e0d916f19a3c4971640df4ce04de3558ec7b28fc04848f59cc0033
- 660b0bc7c7c5ba0143a6a1c2e7074d2c0120a4dbaa66e2a977d2927e5ba34c78
- 2761bd6c34a7b0a65ed28617c717fdb79c5a9d1b9c2ad01ee527f7b14bbd9a07
- 59d8f01e4a9fb0af4b994122409ae5986685d43bfa20e5c1106b80bf9a8ec08e
- 6daf16115a518707e974fa5f3f8593e2d127a8a72576aef9d90462199bde1a55
- 858d7db898440fdd90aa01252f28e48114352e6bd1c8f0f23f80ea135b7c0db0
- 9becc5cdf0980e08e23581f3aec5906410300ff4b77d5cedc7acef55f31929e7
- 56258e2608210417ce1b656f269b7af42e74ca37c3c6934f0026a19a0d0fc561
- c32bdd1b6f14af2bb06368fe2ffc3817b07bacb63ef53bb35f0e4cf95dc7aa69
- eee0df82a764372b569ad2050fd775a6f5647571789e386b2fe2489480b8b4e9
- 520a2726794c46149e88a63d1251e01096ec01ccc3feb177a21d99c8248b55c3
- 5dbebbf3c20c67d5d598a4449b97bb60287086ce1e6ee86a640ab3a9705c6b2e
- fe1ff4793710ecef947a7c0bf9dab843ca294304de0d3ffa6a13b688be340768
- 06f6953e62ad5d51d842af7fa8ec591728044b801b16b83a4235ca339744e3f5
- 65c38d1947fa9babd51ec10ebe354cccafc256bbb4e46d25296e923842e9a853
- 4af465f1c9aa0958f8bb32d62cd02b16e50dbab10d66363963299e5359b6bf51
- 68531aaf4254c85e66c4a05dd9b7a13dd57054a17f70797b7256da8fe6e4c151
- 77e832796e16ec6cdd97c3b2a3ecf10c6aba7c7c084d3451887eaf3d63097abe
- 3f3e5abc0577c58fb1d7b4c5ff083d54a296f2b29325da7cbaf52eaeef26bcfc
- 1e829180329d4f33966289b96cb31f5f849b0029b03bba43618eaa021c9c50b3
- 5ef83c6264d40219a992d752b29dc8bd95b11a8c9fd9b0d1a903c61db1de2d6a
- 5aa3bc297f3aa94bf408c33a95f487f88053a038b4d1d8316fa5b1221cc95a47
- 8490258d7212039e3a2eda632aa918ccf4b361414b03fba351b1ea991c87be96
- d4f8c57accbfee26690ba94e2416ca88ab5f6ebdc821b0cf73b9e6d886375444
- 12b8736f7411bec6ed1b179c910e7a5a7eed7175b82b9456d7bfcdfa7037de6a
- 98f456dd21e90536736321b948032107e76b4d4c06b276e6a607425b4d19678e
- 861121c20d087e8ea7d8db1f0b5897393a26037db7e3486eeedd14b8c8cfe46a
- ff6061936f2ffa2c0d27d2d1efae6fdb990569a81b744600e9c02f720760c76a
- 50775695b67cf7b25ab385cd51f0be1d540ddfecd38f67fa5c4a3f3b6ea790c8
- dce71131597b20aea87b8398fe4ecf5734dfdcff88d42d812532e26588377932
- 661b9af1c92c145b557ea9b886413b7236bfe55d39c42a8596f87398f5a22dd4
- c94ef08929ecffc3b048ae867735bec8ab2672a054e5c88a98c3657e95cb8c73
- 1402f350880c5b32a05fa1dffac3578823c6a289ef9690e760ec7202769d6365
- c7e4c98c69f7c029d2d8e1eeee2bf1a165c43774f7492af7c19b808b2ab1bd0d
- b66cf325561ea9aa1bc1a0a27339f95b80e3ad03fe39bb513754f5ea624539cb
Thanks to Alex Calleja, Aazim Yaswant, Vishnu Madhav, and Gianluca Braga for their research on this malware.