
Researcher: Christy Philip Mathew (@christypriory)
Relevant Devices: iPhone 6s and later, iPad Air 2 and later, iPad mini 4 and later, and iPod touch 7th generation
CVE: CVE-2019-8804
Summary
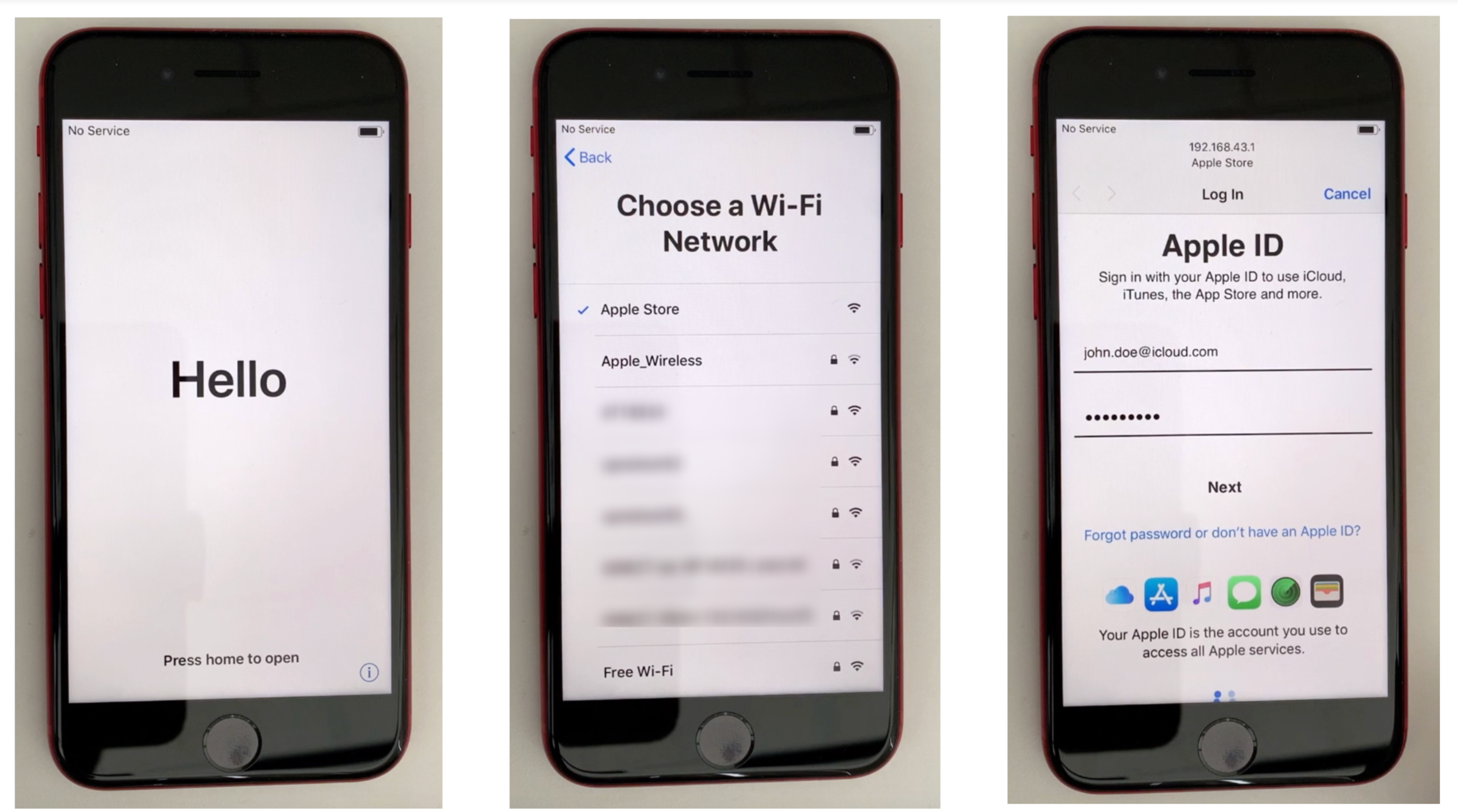
An attacker in physical proximity of an Apple Store or an Apple retailer may be able to force a user onto a malicious Wi-Fi network during device setup, if the device discovers the network with the name “Apple Store.” This may occur if you’re setting up your first iOS device or if you want to start over after a factory reset, then you are at risk.
An attacker can easily setup a rogue access point and if a customer unboxes a brand new iPhone to set up, it would automatically – without requesting user’s permission – connect to the ssid “AppleStore” which in this case would be the rogue access point, and the attacker can intercept iCloud/Apple credentials.
Often an attacker can also perform a KARMA attack – an attack that exploits a behavior of some Wi-Fi devices, combined with the lack of access point authentication in numerous WiFi protocols – to show any requested networks as available. In this case, an attacker does not even need to perform a KARMA because Apple devices automatically connected to any network with the name “Apple Store.”
Action Taken
An inconsistency in Wi-Fi network configuration settings was addressed as part of iOS 13.2 and iPadOS 13.2
Of note, prior to CVE-2019-8804, Zimperium’s zIPS alerted the user to disconnect from the network if it connected to such a rogue network.


