
Mobile apps require continuous testing throughout the development process to ensure proper compliance and security measures are in place. If you are using Jenkins continuous integration server in your pipeline, continually testing your mobile app builds is simple with Zimperium’s mobile application security testing platform, zScan.
Here we will describe how you can automate mobile application security testing from your Jenkins implementation and increase your testing cadence to produce better apps while reducing your time to market and the associated manual effort. Every time new code is submitted to Jenkins, zScan will test the compiled app and provide specific details about improving any security gaps in your mobile apps.
In this blog, we provide details on:
- Why mobile application security testing remains difficult;
- How to automate and configure testing from Jenkins;
- Available outputs and optional Jira integrations;
- Test Data categorizations; and
- How to install in your existing processes
Successful Continuous Mobile App Testing
Today, successful mobile application development organizations utilize a combination of native and cross-platform frameworks. Cross-platform frameworks allow for a single code base without compromising a great user experience. This means features and fixes are rolled out much more frequently than ever before.
Keeping pace requires testing solutions to not only assess these frameworks accurately, but also allow for complete automation. You need mobile specific tools since it’s not just Android and iOS operating systems that are changing; the hybrid frameworks are evolving as well.
“With zScan, we are detecting security vulnerabilities before release – in hours rather than weeks – and then automatically provide our third party developer with a list of fixes.” – Application Security Manager, Global Banking Company
Failing to identify errors in mobile apps correctly can lead to disastrous results. Governing bodies can fine your company for failing to comply with a compliance mandate or, worse, your company could suffer severe brand damage if a mobile app breach became public.
There are several public mobile app breach examples from this year. Some of the more notable breaches from this year include the Walgreens mobile app, BHIM data leak, and several coronavirus contact tracing apps that leaked private user data.
Automated App Testing Using CI/CD Platforms
Automating mobile application security testing in your DevOps toolchain provides your teams the opportunity to test early and test often. Developers continue to commit code in the same fashion when developing new features, bug fixes, and modifications. However, by integrating continuous testing to Jenkins during the development cycle, you identify compliance, security, and privacy risks early when they are less expensive to fix.
If you reduce the number of bugs by testing more often, your overall delivery costs decrease, and throughput increases. Integrating security tools into existing DevOps frameworks allows for more productivity and better quality without forcing developers to unlearn and relearn new processes. Sounds good, right?
zScan Automates Mobile Application Security Testing
Zimperium’s zScan mobile application security testing platform provides security and development teams with privacy, data leakage, compliance violations, and security findings on any iOS or Android application. Zimperium’s proprietary processing engine dissects each mobile application binary directly from Jenkins and provides data on your apps’ resident risks.
Each finding provides developers specific descriptions and remediation instructions. The detailed instructions can integrate into existing ticketing systems like Jira. The platform can be further customized to focus on categories that align with your enterprise or industry.
Incorporating the scan results into your ticketing system allows for further downstream efficiencies. These integrations mean developers can work faster and reduce cycle times for bug fixes and enhancements. Teams can customize and filter findings as tracked, mitigated, confirmed, or fixed to prioritize workflows and deadlines.
How to Configure Your Jenkins Server and zScan
Integrating Zimperium’s mobile application security testing to Jenkins is simple.
- Download Jenkins plugin from zScan administration console;
- Open Jenkins and navigate to “Manage Plugins;”
- Upload zScan plugin to zScan; and
- Configure Jenkins
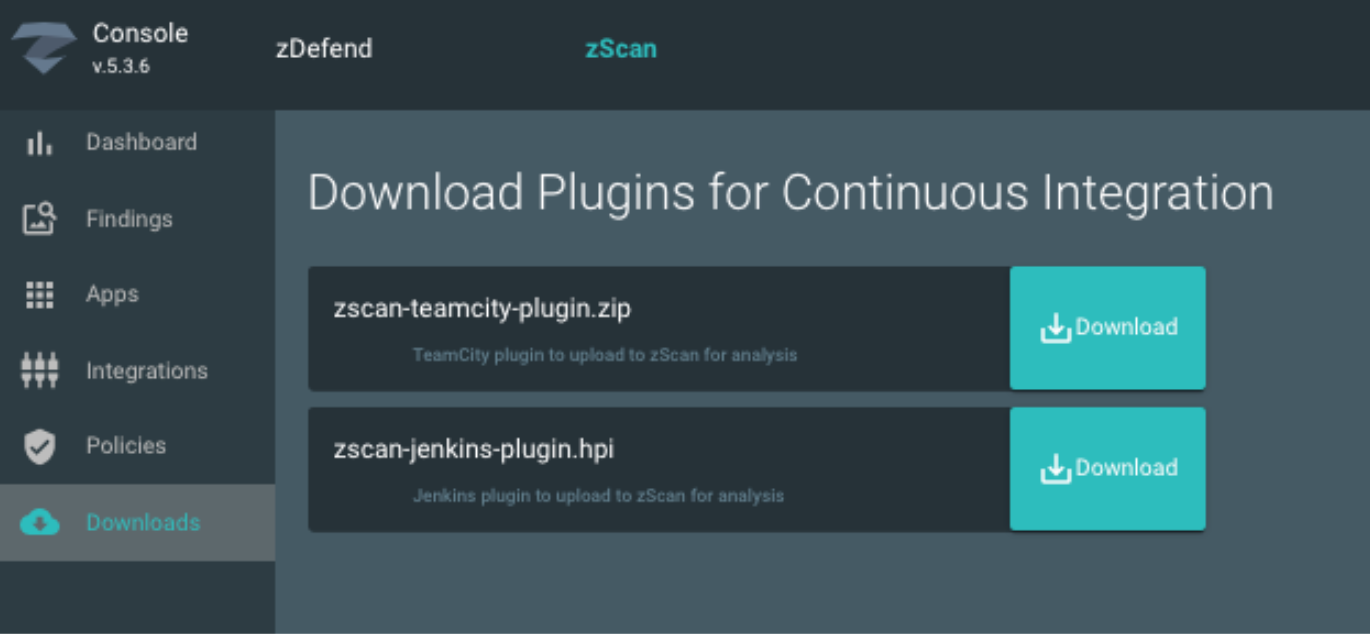
Download the Jenkins plugin provided in your zConsole administration panel.
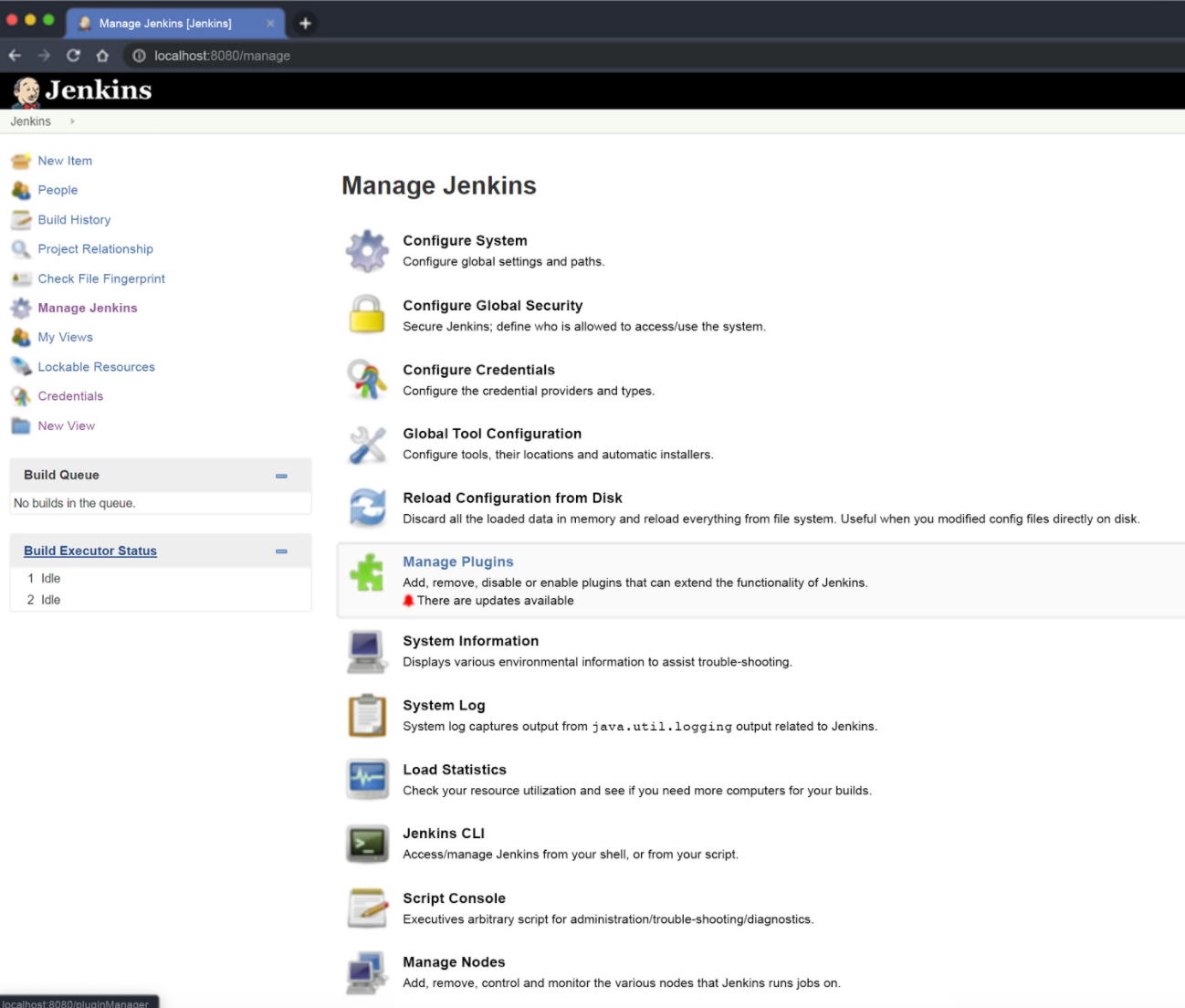
Navigate to Manage Jenkins and select Manage Plugins.
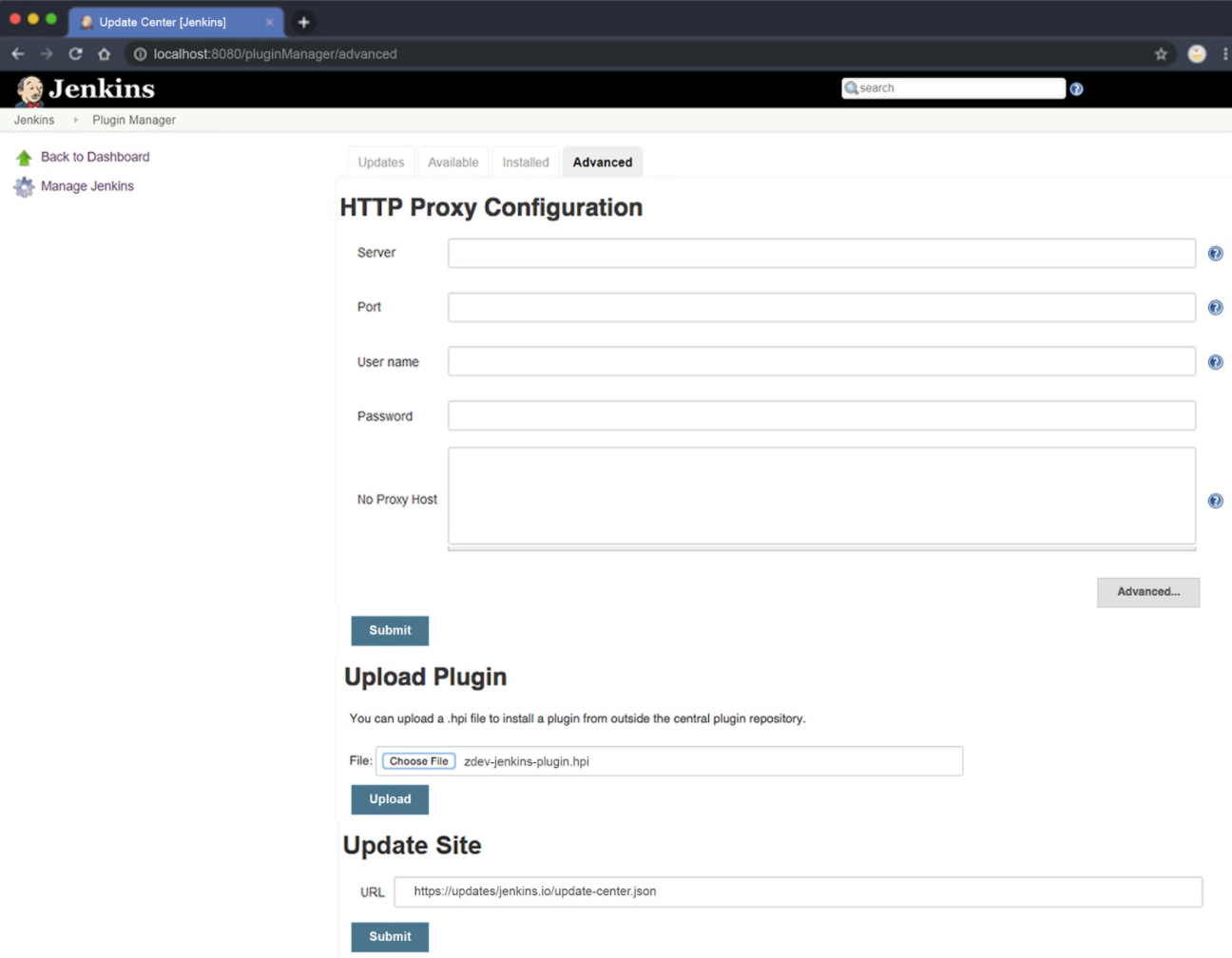
Click the Advanced tab and in the Upload Plugin section, choose and upload the file zScan-jenkins-plugin.hpi.
Then restart Jenkins.
Jenkins Configuration
In the Configure section of your project, select Add Post-Build Action, and click “Upload Build Artifacts to zScan.”
Available fields in your configuration include:
- Zimperium Server URL Endpoint
- This is your root URL to your Zimperium console.
- Client ID
- This value is from your Zimperium Console Authorizations. Your Client ID is created after you generate your API Key.
- Client Secret
- This client secret is only displayed when you initially generate your API key along with the client identifier value.
- Source Files
- This allows you to specify patterns using ANT script. Zimperium provides several possible ANT statement examples that can help you get started.
- Excluded Files
- This field provides the ability to specify patterns to exclude files. This field is the opposite of the Source Files field. Similarly, multiple patterns are comma-separated.
Findings, Instances, and Compliance Categories
After you configure Zimperium’s mobile application security testing platform with Jenkins and begin testing, zScan will provide you with security findings and instances. Findings are potential issues discovered in the app analysis. Each of the findings describing each issue is categorized by affecting security, data leakage, and compliance (OWASP, NIAP, NIST, CCPA, GDPR) mandates and recommendations.
Instances are specific locations where the finding is present in your app’s code. A hypothetical finding example in a physical penetration test could be that the doors in your house remain unlocked. If both the front door and back door are unlocked, there are two instances of the finding. Both of the findings may or may not need to be fixed. You can choose to accept one instance, allowing the back door to remain unlocked for a given house (app). Customizable policies can filter findings in future assessments for unlocked doors so you can focus on new findings.
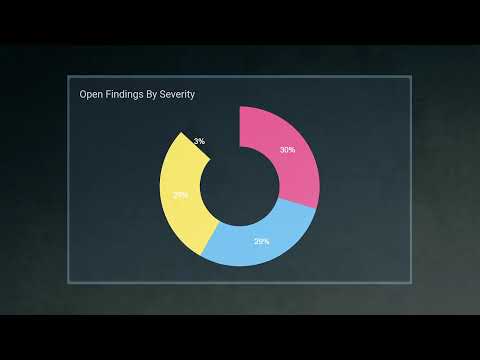
zScan Helps Reduce Mobile App Risk
To reduce risk and limit fraud, organizations worldwide are testing native and hybrid mobile apps with zScan to identify potential data leakage and security vulnerabilities. Mobile application development teams from the banking, financial services, healthcare, and public sector depend on Zimperium to secure, harden and detect real-time attacks to their apps, no matter the health of their users’ device.
“With zScan, we are detecting security vulnerabilities before release – in hours rather than weeks – and then automatically provide our third-party developer with a list of fixes.” – Application Security Manager, Global Banking Company
Contact us today for more information on zScan and how you can automate your mobile application security testing.



