Campaign is still active and growing; second bank app identified
Zimperium, in collaboration with a leading Asian bank, have uncovered the early stages of a coordinated effort by scammers to defraud existing and new bank customers. In this blog, we will:
- Alert the general public about the scam before it gains traction;
- Outline the entire scam around the fake bank app; and
- Show how it is also targeting other financial services, including another bank.
The campaign coincided with the bank’s announcement about its development of a digital exchange, enabling institutional investors and accredited investors to tap into a fully integrated tokenization, trading, and custody ecosystem for digital assets.
Thus far, dozens have downloaded the app and have lost an average of $1,500 each. The app – first seen on VirusTotal on December 22, 2020 – has still not been identified as malware or scamware by any anti-virus companies.
The campaign remains active and is, in fact, growing:
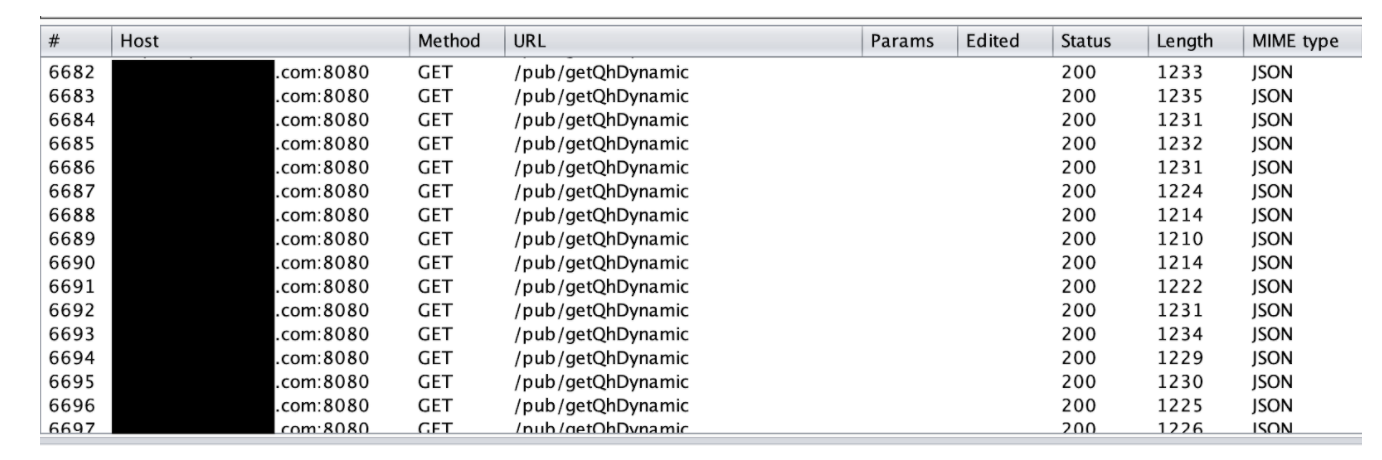
- It appears to be downloadable via third party sites and/or phishing links;
- The command and control servers are still operational;
- The elaborate scam itself features, among other aspects, active customer support; and
- We’ve learned of a similar campaign targeting a second bank. We are reaching out to that bank directly, before revealing the name.
Downloading the app
Once the app is downloaded from a third party store or phishing link and is opened, the victim is presented with the following login page:
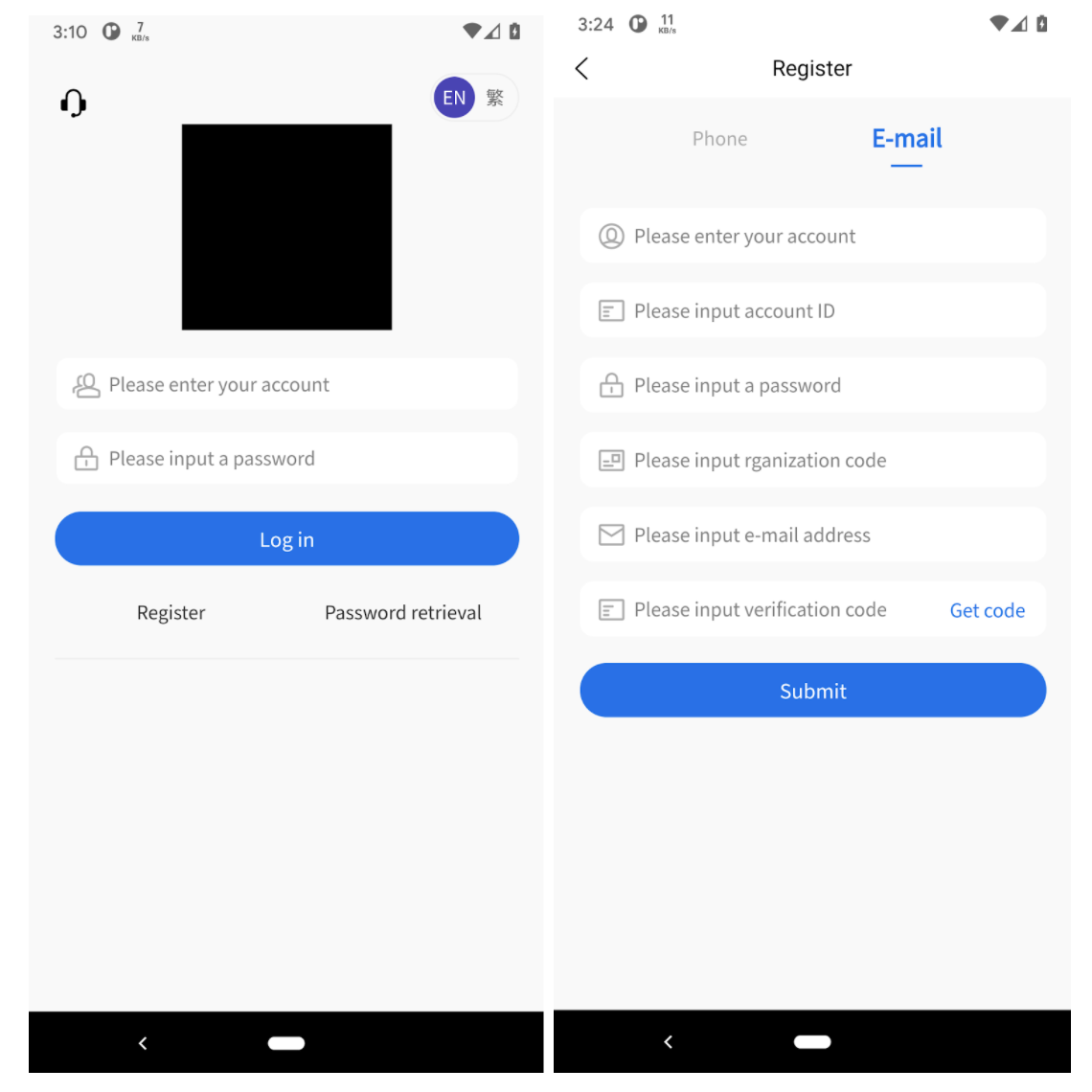
As part of the registration process, users are asked to provide an email address, account number, “rganization code” (note the typo appears in the app itself) and other details.
In an attempt to appear legitimate, registration generates an automated email containing a verification code trying to impersonate a legitimate email from the bank (including using the bank’s name in the email address). We received verification codes when we registered with legitimate and fake information.
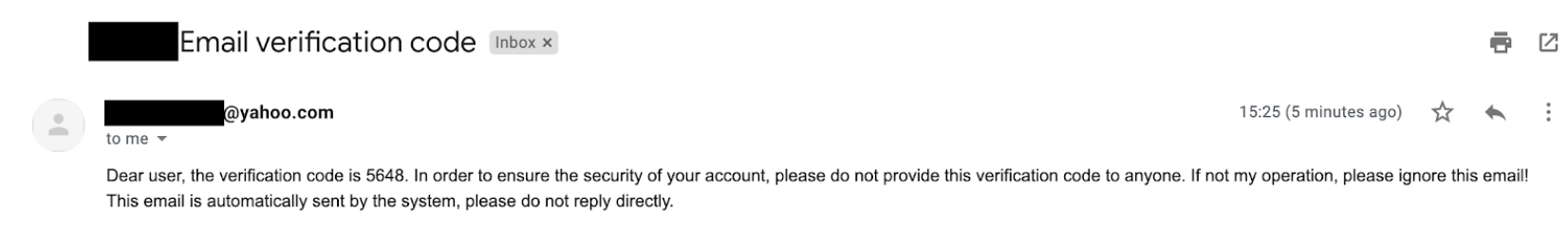
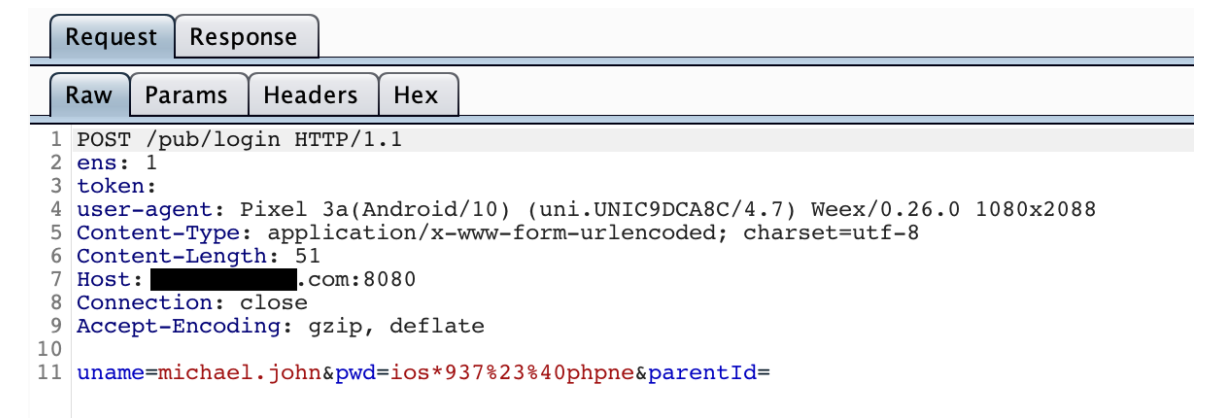
The entire communication takes place with a server that does not belong to the impersonated institution. Instead, the user has unknowingly shared personal and financial information with the attackers.
App experience
Once logged in, the application presents the victim with a seemingly legit cryptocurrency trading platform using the brand value of the impersonated organization as a lure. It looks more convincing with the dynamically changing prices.
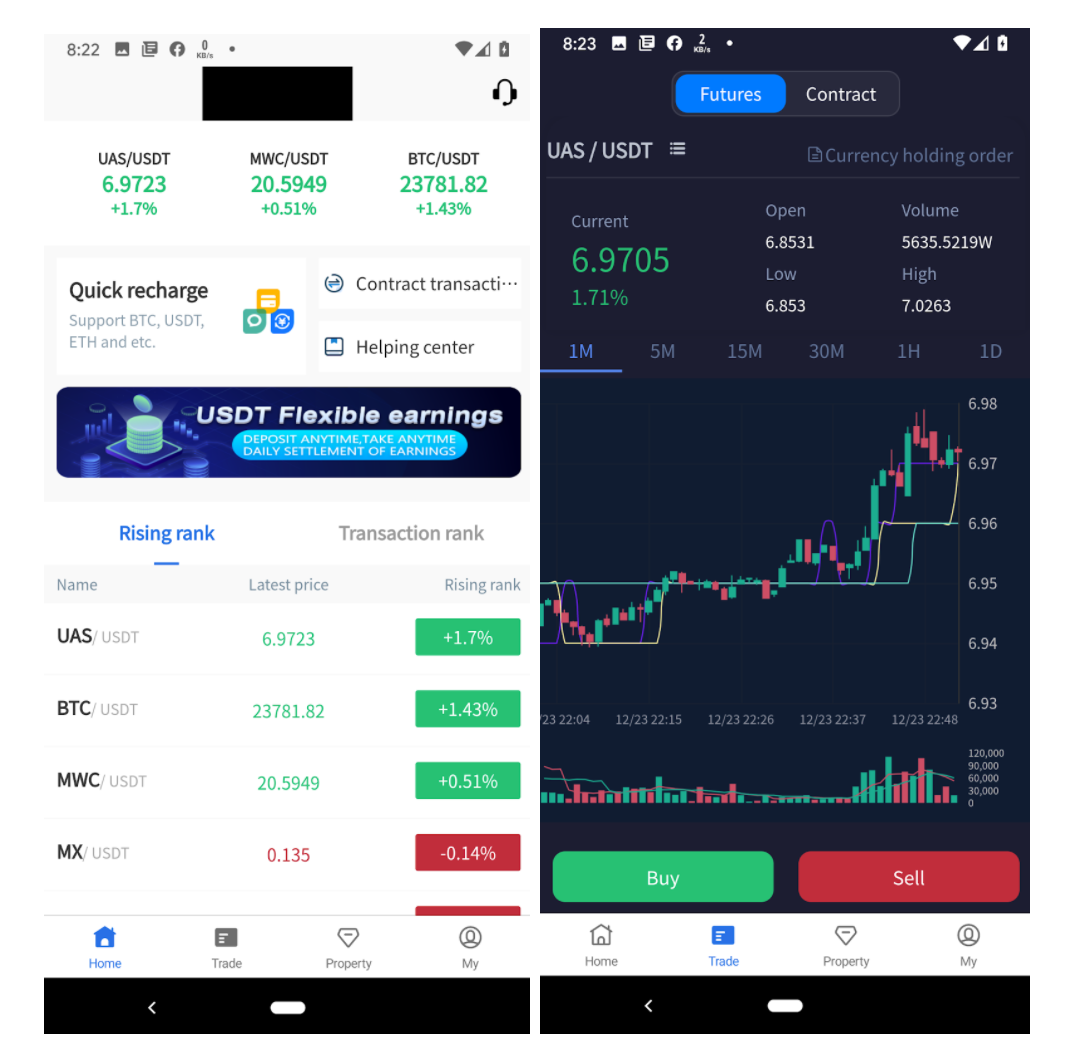
Customer support
Moreover, the presence of a customer support option provides the victim with additional confidence of being able to contact the financial institution (the scammers) with any questions or issues.
When we attempted this, we received the following:
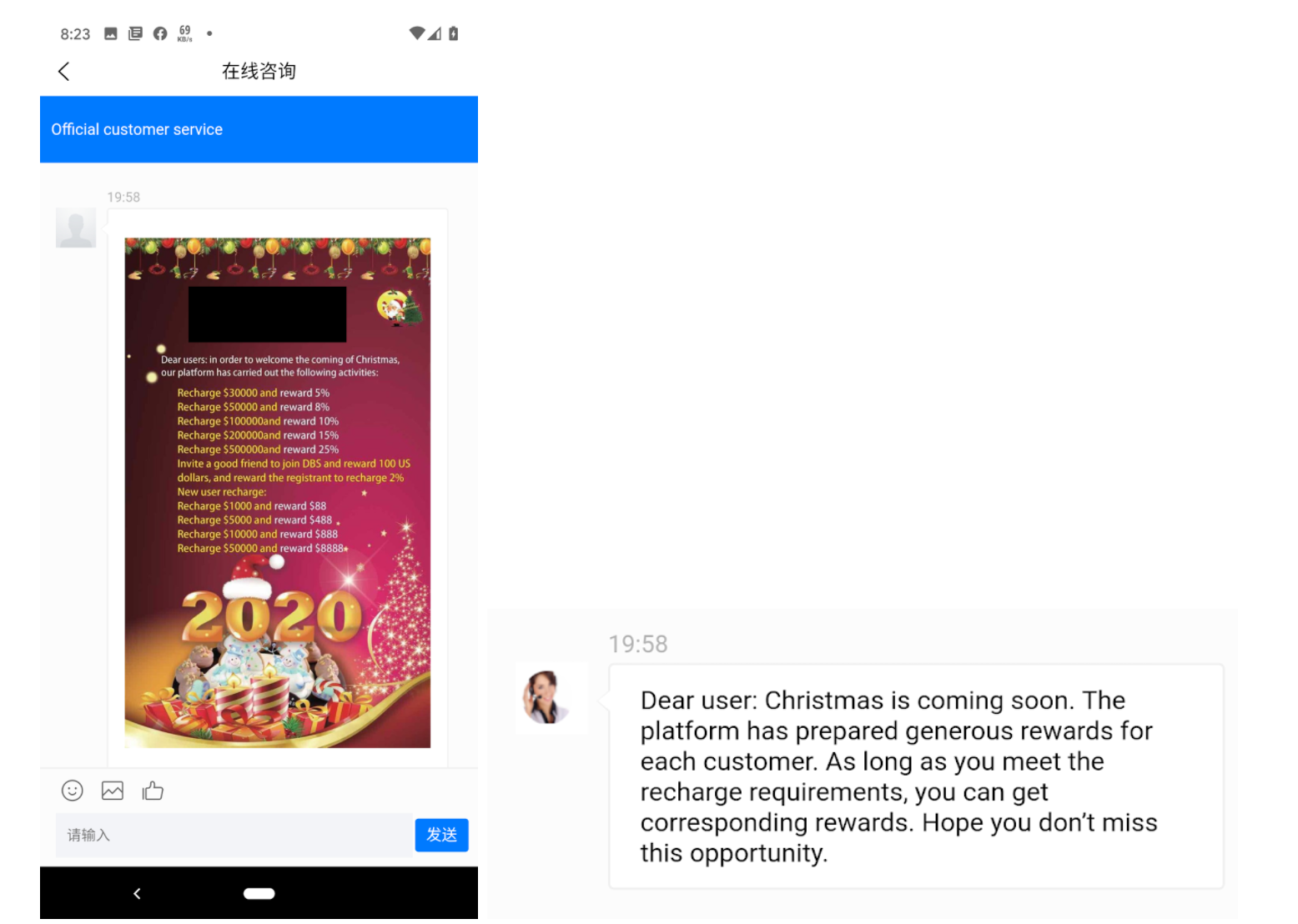

Customer support would be the first choice for the victim to complain about discrepancies, but the scammers cleverly set it up in such a way that it convinces the victim to “Recharge” and invest to reap (non-existent) benefits.
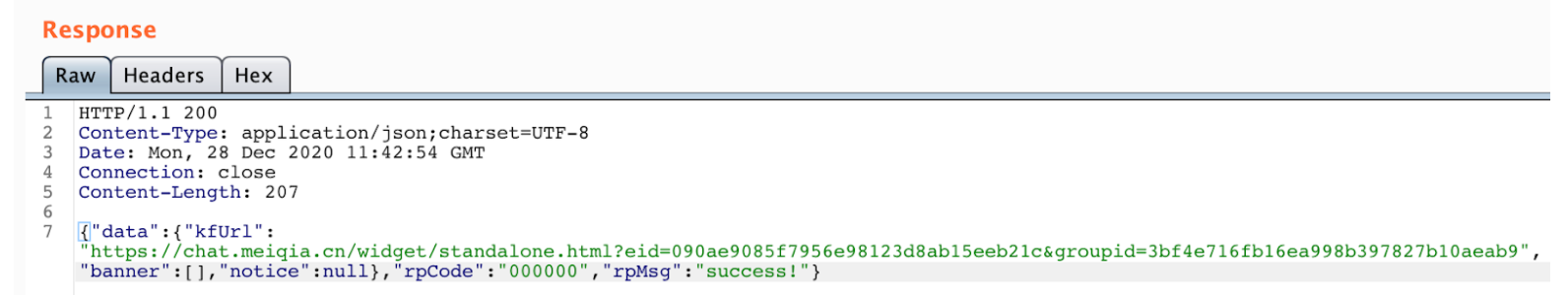
Making use of legitimate platforms that offer services to communicate with customers through customer support, the scammers offer “Customer Service Solutions” as seen below with this command and control’s response:
If the upward trend makes the victim interested in investing, the scammers have set up a “Funds Management” page allowing for the continued exploitation of the victim as seen below:
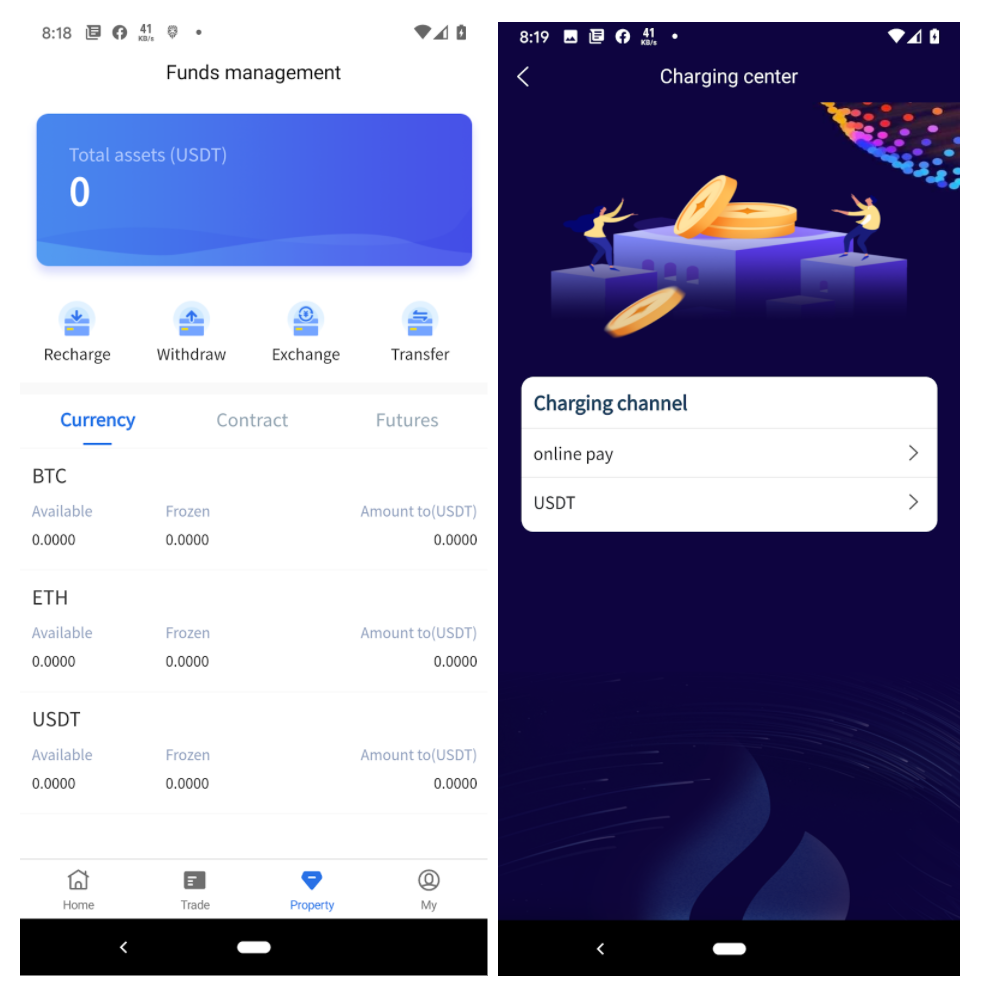
The Recharge option mentioned above is the first go-to for a new victim to begin investing through the platform.
The two investment options offered are “Online Pay” and “USDT,” where the victims were asked to chat with the customer support and pay online or transfer the funds to a provided BTC or ETH wallet and attach proof of the transaction.
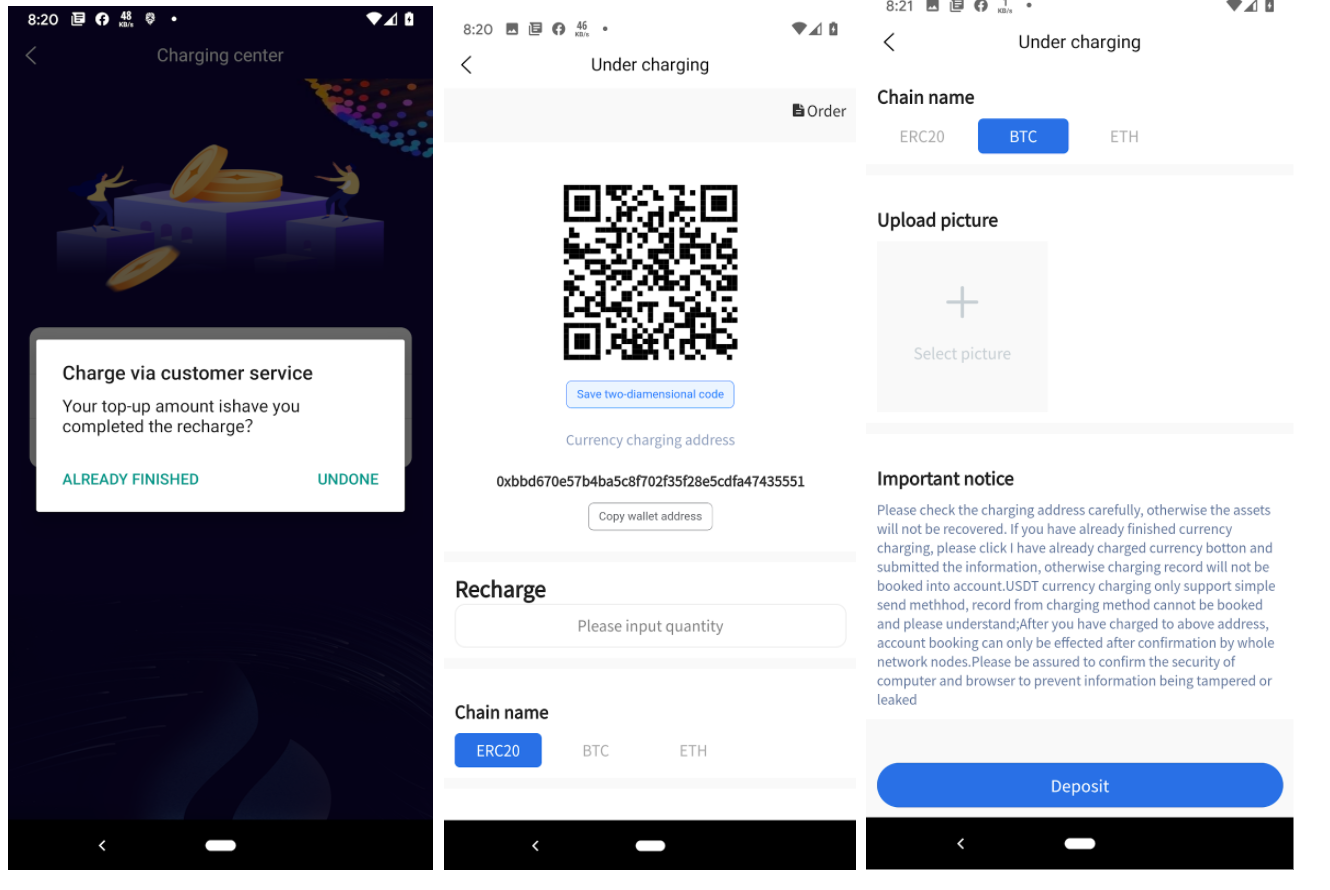
What can you do?
It’s clear this campaign is just beginning and – as we mentioned – targeting a different bank already. Here’s what you can do:
From a consumer perspective, never download apps from third-party sites; rely solely on the App Store and Google Play. Be leery of apps that may have grammatical or other errors – like “rganization code” which appeared in the app itself.
From an enterprise perspective, Zimperium is the global leader in mobile device and app security, offering the only real-time, on-device, machine learning-based protection against Android, iOS and Chromebooks threats. We detect this attack and others like it.
Please contact us to learn more.