
2020 has been crazy… to say the least. But in many ways, 2020 has thrust a huge spotlight on something we’ve known for quite some time – – mobile threats are real and mobile devices and apps need protection. It truly is crazy how many stories we’ve seen – and the year isn’t over yet – where the need for mobile security is front and center.
Recently, Scott King and I hosted a webinar on the Top Five Mobile Security Stories of a Crazy 2020. For those who may not know, Scott – among many other things – has authored many of our threat reports related to mobile apps, including a recent series on security and privacy risks on financial apps from around the world. To watch the webinar on-demand, please click here.
We each developed a list of the top five mobile security stories independently, and tried to refrain from any COVID-specific stories. With that in mind, here are Scott’s top five:
A tip from a young girl on TikTok who found three TikTok users, one of whom had more than 300,000 followers, promoting what appeared to be an abusive app. The girl reported it to Be Safe Online, a project in the Czech Republic that educates children about online safety.
The tip led to the discovery of aggressive adware and exorbitant prices lurking in iOS and Android smartphone apps with a combined 2.4 million downloads from the App Store and Google Play.
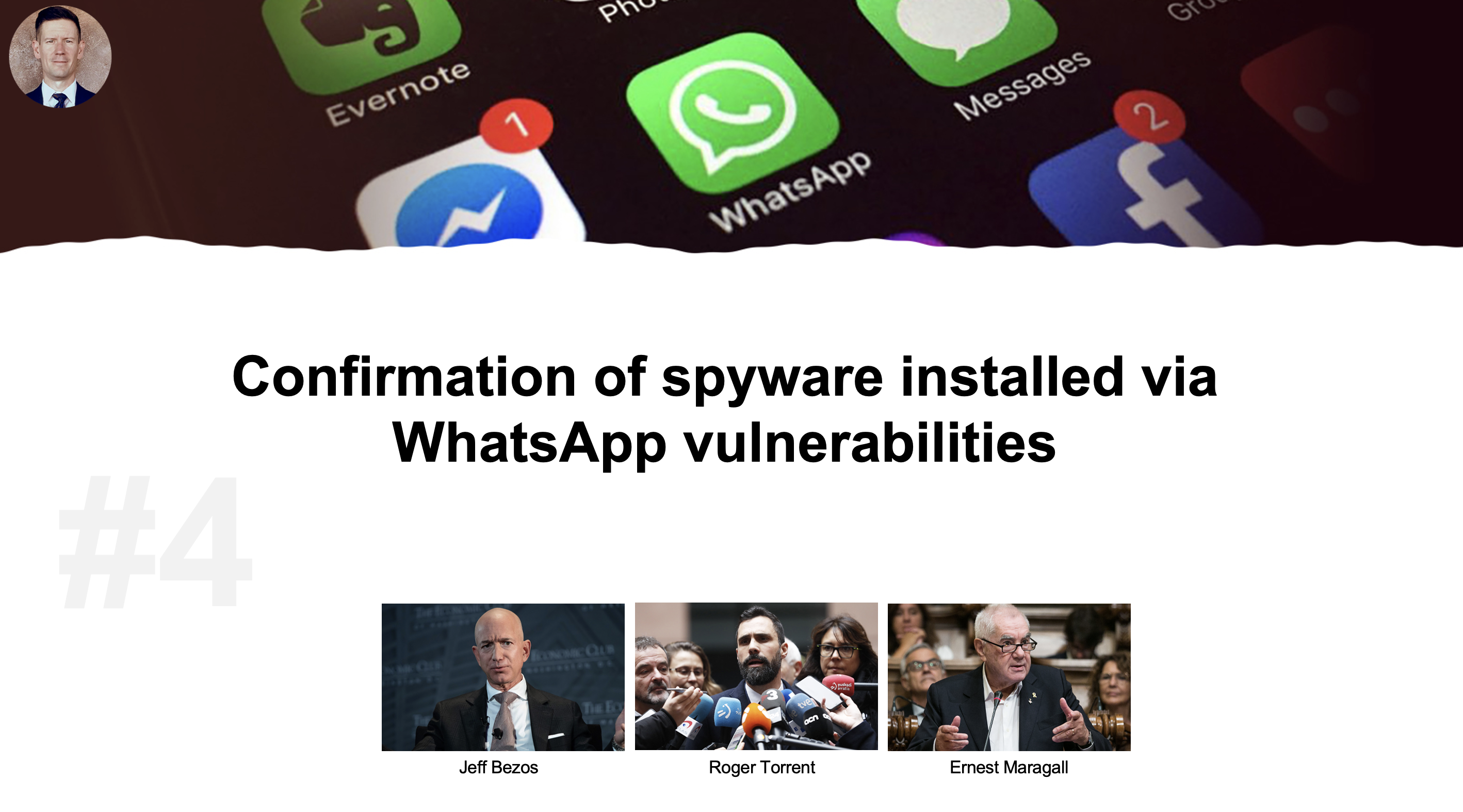
In 2020, we not only received confirmation that popular apps like WhatsApp are vulnerable, we saw that vulnerable apps are being used as a way to install spyware. Roger Torrent and Ernest Maragell – two Catalonia politicians – and Jeff Bezos were all victims of targeted spear phishing campaigns where attackers took advantage of the vulnerabilities of an app as a means to their end.
The simple fact is, no platform is 100 percent bulletproof and no app is 100 percent bulletproof. That’s why in the mobile world, just like in the traditional endpoint world, we constantly have to be looking for, finding and patching vulnerabilities, as well as providing protection behind vulnerabilities when something goes and exploits it – – like what happened here with WhatsApp.

This is related to the iOS 14 beta when it first came out, and people installed it. Users noticed that some apps had access to their pasteboard or their keyboard and the operating system would warn you – ‘Reddit is monitoring what you’re typing right now in LinkedIn or Twitter or some other app.’
There were a lot of videos on Twitter on how this works. The privacy aspect of that is going to change the way we really think about our private information.

Unfortunately throughout 2020, we’ve seen the continuing evolution of remote access banking Trojans. Anubis…BlackRock…Cerberus…Alien. One is released; does its damage by grabbing our banking credentials; signature is created; here comes the slightly tweaked next one….and so on….and so on. It’s clear we must monitor this as the Trojans continue to evolve and evade detection.

Okay, so at first blush this may seem self-serving, and we are very proud that the Department of Defense (DoD) selected Zimperium Mobile Threat Defense (MTD) to deliver comprehensive Mobile Endpoint Protection (MEP) to the unclassified government furnished (GFE) devices of servicemen and women around the world.
The fact that we will protect DoD mobile users and endpoints against phishing, malicious/risky apps, OS exploits and network attacks, points to the real story: The DoD saw a proliferation of threats and attacks on mobile devices – as we’ve described above and will continue to do so below – and recognized the need for protection. Now.
Scott had a great list. Here’s mine which again, I developed separate from Scott:

Back in January, the Associated Press (and the world) reported that two U.N. experts called for the U.S. to investigate a likely hack of Jeff Bezos’ phone. A commissioned forensic report found with “medium to high confidence” that Bezos’ iPhone X was compromised by a video MP4 file he received in May 2018.
The Bezos hack was the highest profile mobile breach to date, bringing into focus the need to protect mobile devices.

Much like the Bezos hack, so much has been written about TikTok. One aspect not receiving the attention it deserves is the idea that the TikTok app is the exception when it comes to mobile app privacy and security is false. It is the rule – – almost every mobile app has privacy and security risks. The degrees obviously vary, but the results are indisputable – – mobile apps are fraught with privacy and security risks.
For example, in the last year, we’ve researched the top banking apps in 2020 and 2019, leading travel apps, shopping apps and dating apps. The overwhelming majority of the apps have privacy and security concerns.

Another example of a vulnerability occurred in April, when Apple acknowledged that every iPhone released in the last eight years was vulnerable to remote attacks through the iOS Mail app. Apple did patch the vulnerability in the iOS 13.4.5 beta. This further demonstrates the fact that every platform and app can be vulnerable. This is not an iOS thing; this is a reality of all platforms and apps thing.

To reiterate Scott’s points, the big takeaway for me is that – thanks to the DoD – the spotlight is brightly on two things: 1) mobile devices are the major, if not only, endpoint for many users going forward and 2) that mobile endpoints are under attack and need protecting.

COVID-19 created a situation unlike anything many of us have ever seen; yet one that will likely leave permanent changes in remote working and learning. With the overnight shift towards entire workforces working remotely from home, on all variety of corporate and personal (bring your own) devices, IT and security teams have been in triage mode from a security and risk perspective.
We saw, and continue to see increases in COVID-related phishing and malware attacks as businesses scramble to provide protection to its employees.
It’s not just remote working. Faced with uncertainty in an ever-evolving climate, school districts and higher learning institutions are struggling to do what is best for students and teachers alike. For schools relying on Chromebooks for remote education, students, teachers and administrators face the same privacy and security threats associated with laptops and mobile devices, without the same security measures.
Contact us
To watch the webinar on-demand, please click here. To learn more about how we can help protect your mobile devices, please click here.



