
written and researched by Nicolás Chiaraviglio and Santiago A. Rodriguez
CISOs worldwide are scrambling to address phishing attacks. In the second quarter of 2019 alone, there were close to 130 million phishing attacks, taking place on different types of devices within an enterprise – – desktops, laptops and mobile devices. And as unfortunate as it sounds, unscrupulous individuals are using the coronavirus pandemic as a way to leverage phishing attacks.
Mobile devices are even more susceptible to phishing attacks because of the small form factor and the inherent trust we have for something that is within reach or in our hands other than when we’re sleeping.
Enterprise organizations have increased risk exposure as a result of mobile phishing in multiple ways. In this blog, we will:
- Show how phishing attacks can be used to deliver ransomware and malware, letting the attacker create backdoors into organizations;
- Explain how phishing attacks can result in damage to organizations including exposing private and sensitive information;
- Illustrate how phishing domains are active long before being detected; and
- Expose how many current solutions require data to be sent to the cloud for analysis which raises privacy and compliance issues.
Fortunately, Zimperium’s patented, machine learning-based engine that runs completely on-device, immediately identifies phishing attempts with 99.99% accuracy and protects the user without sending any data to the cloud.
The recent Key Criteria for Evaluating Phishing Protection Platforms from GigaOm provides an overview on the different solutions available, and includes Zimperium – – the only mobile phishing solution that met the criteria to be profiled. In the Zimperium profile, GigaOm states:
- In the phishing prevention ecosystem, Zimperium’s approach enables them to deploy on BYOD or managed systems. It gives them an edge with regard to broad coverage that includes not only enterprise email, but all email on the device as well as messaging while maintaining user privacy;
- Because of their concept, they’re able to cover more ground than traditional phishing prevention platforms on mobile devices; and
- They put much of their R&D into understanding what sort of behaviors and changes indicate not only phishing attacks but compromised devices, network attacks and malicious apps.
To read GigaOm’s complete profile on us, click here. To listen to our webinar, click here.
How does Zimperium do it?
At Zimperium, we know there is no single silver bullet approach; instead, the right combination of techniques is the most effective approach. Hence, we designed zIPS – on-device protection for mobile devices – with this concept in mind, protecting the user from device, network, malicious apps and phishing attacks.
We use in parallel, proven techniques in the industry along with unique machine learning techniques in order to detect not only known phishing domains but also the most dangerous type of attack for an organization: zero days phishing attacks. Ultimately, this creates a bulletproof shield around our user’s personal and corporate information.
At the core of Zimperium’s solutions is z9, the patented machine learning engine that runs completely on device, immediately identifying phishing attempts with 99.99% accuracy. We are also protecting the user without sending any data to the cloud.
z9 works independently of where the attack is coming from. This means, Zimperium’s users are protected regardless of the delivery method used by an attacker (SMS, email) or even user misbehavior (a user clicking on a phishing link while browsing).
What is a phishing attack?
With smaller screens, and less space to identify troublesome URLs, phishing attacks on mobile devices are becoming more prevalent and successful. Some studies estimate 90 percent of emails are read on mobile devices and a significant percentage of successful phishing attacks are through mobile.
The fact that mobile devices are an endpoint containing or access to the same information as the traditional endpoints – desktops and endpoints – is of major concern for CISOs.
Phishing attacks are usually performed by impersonating a trustworthy entity, making the victim think they are providing the information to a trusted party. This type of attacks target not only desktop computers but mobile devices and even phone calls.
We’ve all received emails claiming our account on a social network may be compromised and we need to answer with our credentials to check if this is the case. We’ve also probably received offers to buy products online by a third of what they actually cost, and we’ve also probably inherited a fortune from an unknown distant relative who, for some reason, knew about us and left us all he had. If that’s the case, congrats! You’ve been the target of a phishing attack.
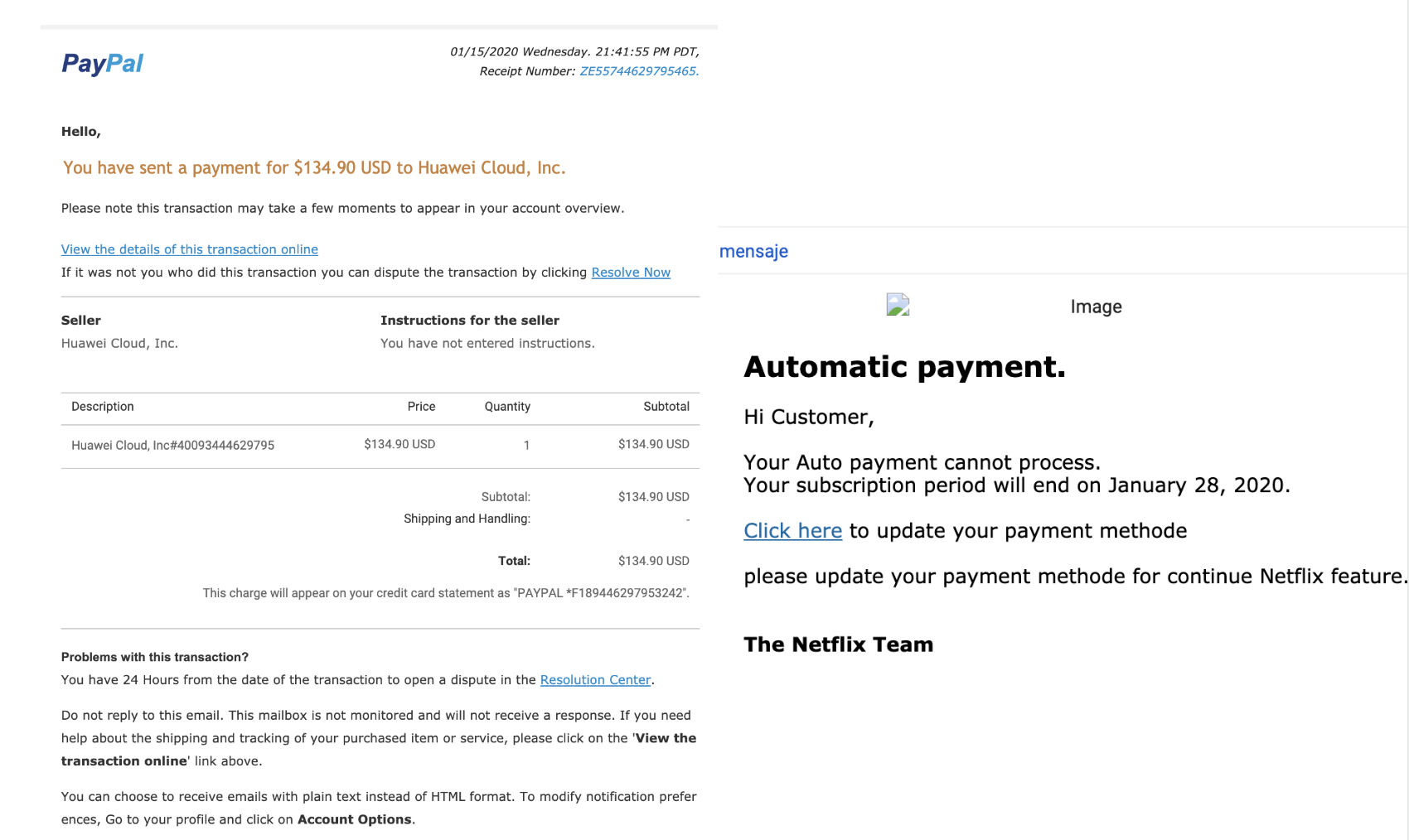
Another use for phishing attacks is to trick the victim into downloading and installing malware, which allows the attacker to access the device whenever he/she wants to do so.
There are several different types of phishing attacks: deceptive, spear (or whale), clone, smishing and domain spoofing/link manipulation. Definitions are sometimes blurry and can change from one source to the other.
Creating a phishing attack requires some degree of technical skills, unless they use a phishing kit, which allows the creation of phishing domains with just one click. Scary, right?
If you want to go down the rabbit hole, click here. You’ll find more information about phishing attacks and kits.
What’s at stake with phishing?
Spoiler alert: everything. Or at least a lot. Phishing attacks are becoming increasingly sophisticated and most untrained users fall prey to some form of attack. When these attacks are successful, they can cause identity theft, financial loss and compromising personal information.
But what’s happening when what’s being targeted is a company and not an individual?
The damage can be immense, potentially putting customer information in danger, damaging the company’s reputation, causing financial losses or loss of intellectual property. Moreover, phishing attacks can also be used to deliver ransomware attacks which cost billions every year.
In order to be successful, a phishing attack against an organization only needs a single employee taking the bait. That’s it. Just one. The weakest link.
A phish x-ray

Let’s take a look inside the world of phishing attacks. As we said before, most attacks impersonate legitimate sites, but which ones? In general, any known website can be used to trick a potential victim but the bigger the brand, the better.
It’s more likely to find a phishing attack impersonating amazon.com than one impersonating mylittleonlinestore.com (don’t bother to click on it, it’s not a real site).
In order to answer the previous question, we analyzed three months of phishing sites data (October 2019 – December 2019) without repetition. More detailed data is in our State of Enterprise Mobile Security Report, 2019.
The impersonated brand was determined using Zimperium’s patent pending phishing engine and the impact of each brand in the dataset was calculated.
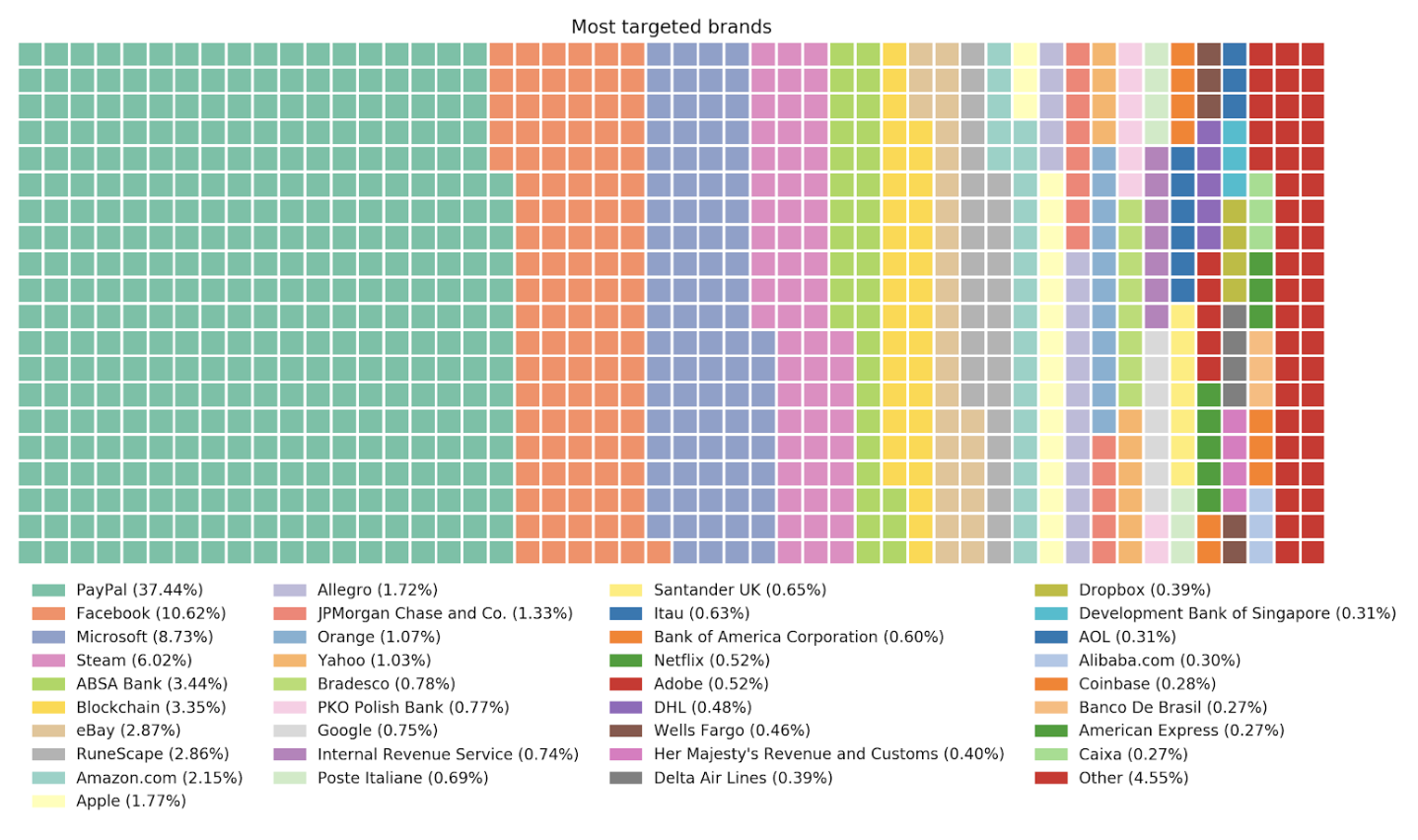
No big surprises here. Sorry PayPal.
What about where are the attacks coming from? We can get a glimpse of the answer to this question by finding where phishing domains were registered.
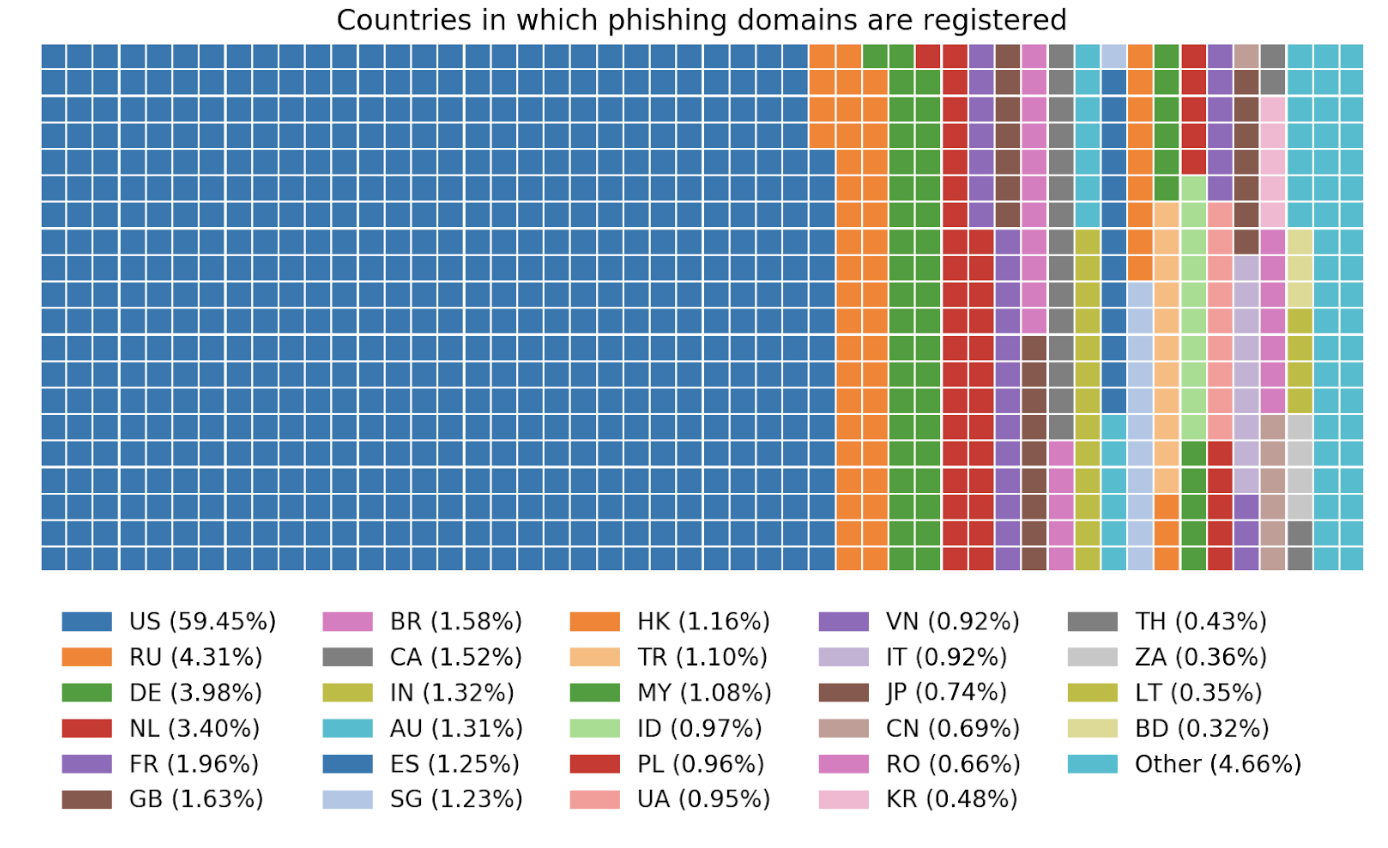
This doesn’t necessarily mean that most hackers are located in the US, but that they are registering the domains used for phishing in the US. If we consider domain registrars by number of registered domains, and group them by country, we end up with this:
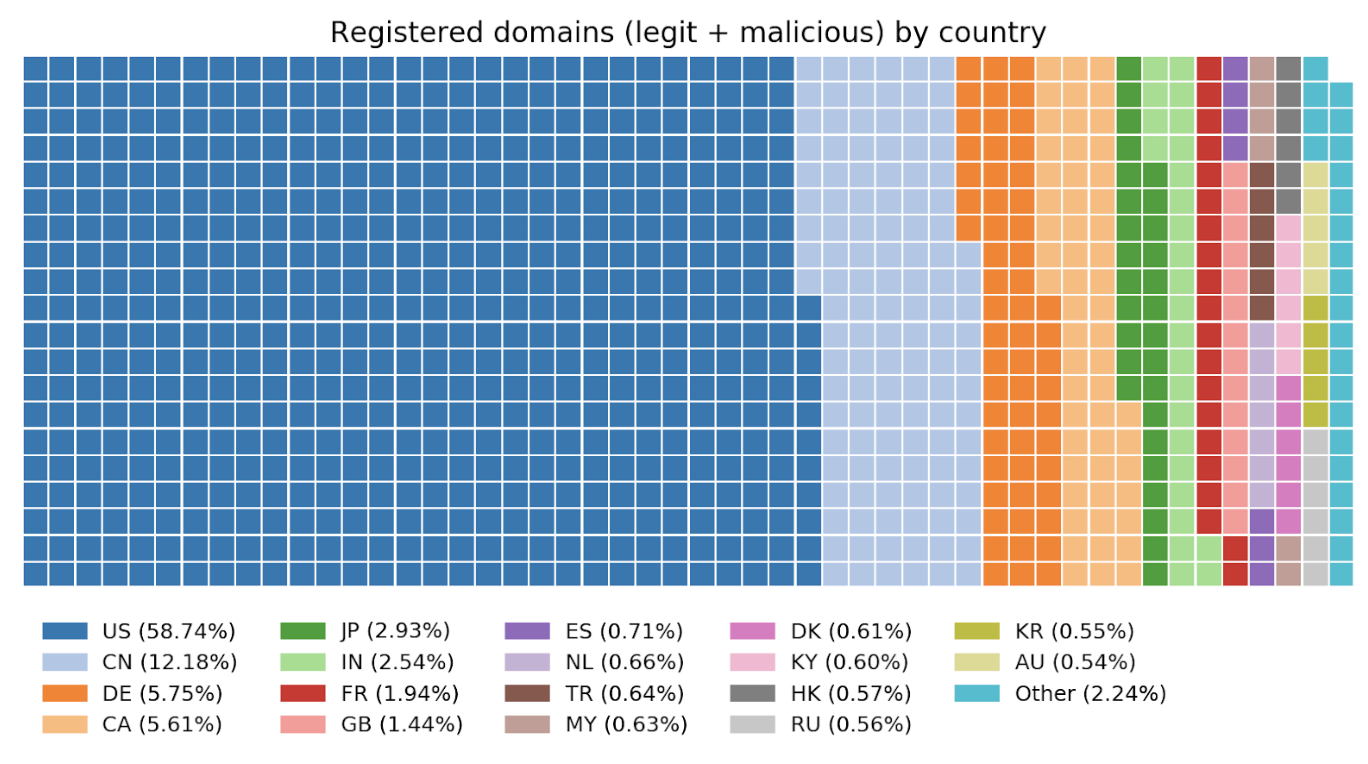
Comparing this chart with the previous one, it is easy to draw a few conclusions:
- The amount of phishing domains, compared with legit domains that are registered in some countries suggests that scammers pick the location in which they register their websites. There are some countries that are favored by attackers. This can be shown by comparing the proportion of phishing domains to the total number of domains registered in a specific country.
- Countries such as Russia and the Netherlands have a huge number of phishing scammers. While only 0.56 % and 0.66 % of legit domains are registered in those countries, 4.3 % and 3.4 % of the total amount of phishing domains are registered in them.
Let’s take a look at the ratio of Phishing Domains Registered/(Phishing + Legit domains registered) for some countries:
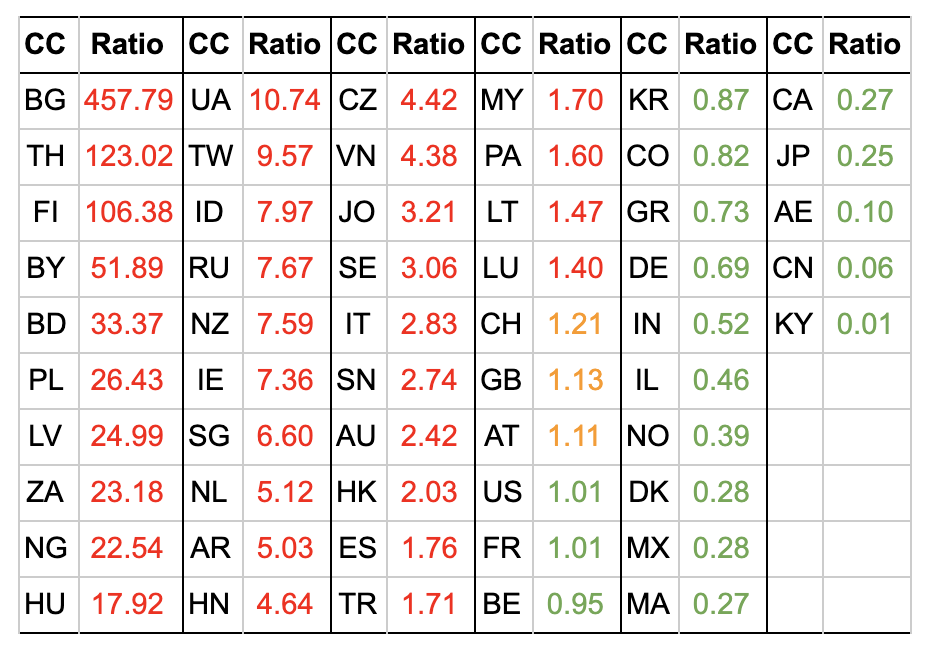
The countries in which the ratios are higher than one (colored in red) have more phishing domains than what is expected if they were randomly distributed. For example, the Czech Republic has 4.42 times more phishing domains than it should. In the same way, Bulgaria has 457 times more phishing domains registered on their servers than expected.
This can be explained because of geographical proximity (i.e. the attacker uses a registrar in the same country they are in) or lower controls when registering domains.
Another interesting metric to consider is how long phishing domains remain active. We will consider two different metrics:
- How long a domain is active before being detected as phishing.
- How long a domain remains active after being detected.
We need to identify three moments in the history of a website:
- Creation date: this will be estimated based on publicly available information about each tested website. We are aware that this metric is not always reliable, but in most cases it is a fair approximation.
- Detection as a phishing website: in order to perform a more objective analysis while excluding Zimperium detection techniques, we’ll consider that a URL is a known phishing site at the moment it’s listed in open, 3rd party phishing databases.
- Becoming inactive: this will be determined based on the same resources as the detection time. The uncertainty of this timestamp will be one day.
To compute metric #1, we’ll plot the number of days between the detection and the creation. The resulting histogram is shown below:
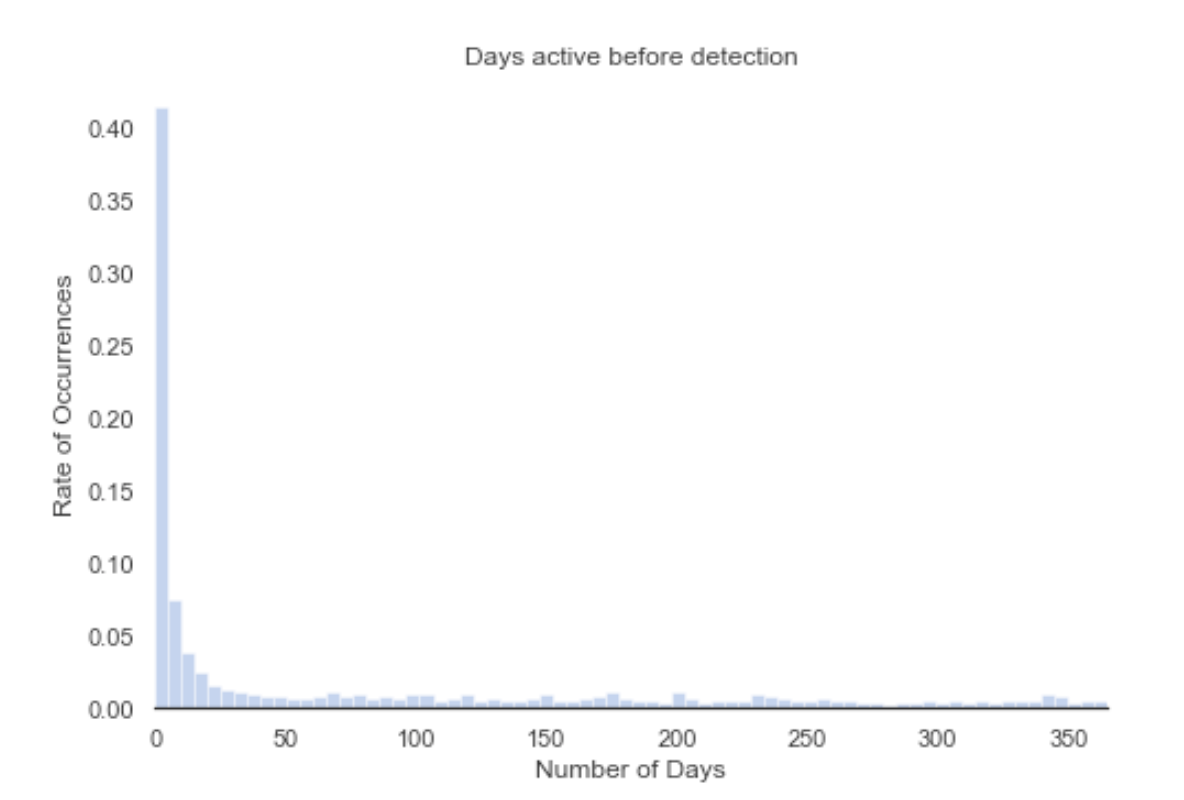
Each bar in this histogram represents five days. Let’s zoom in a bit, since most phishing sites do not remain active that long.
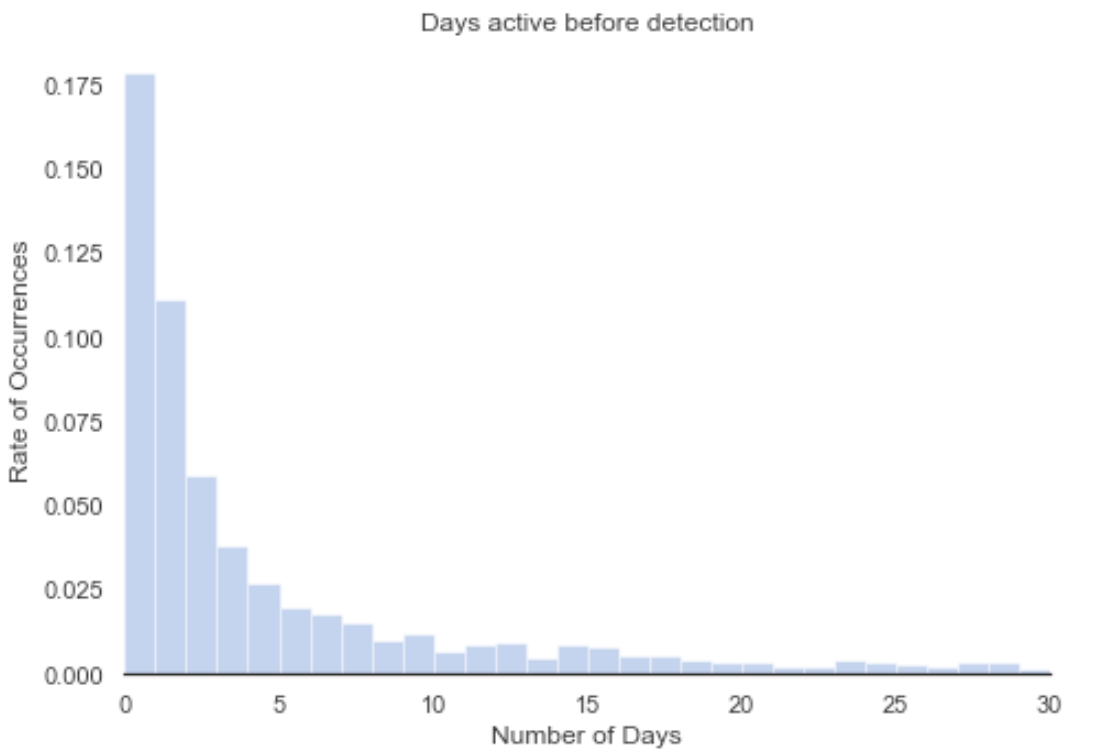
Fortunately, most phishing sites are detected quickly. Around 35% of phishing sites are detected in the first three days after their creation. Within five days, 41% of the sites are detected, while in 10 days 49% of the sites are detected. This means that most phishing sites are active for more than 10 days, which is a time window long enough to perform a successful attack.
Metric #2 is shown as the number of days a website remains active after it was detected. The resulting histogram is shown below:
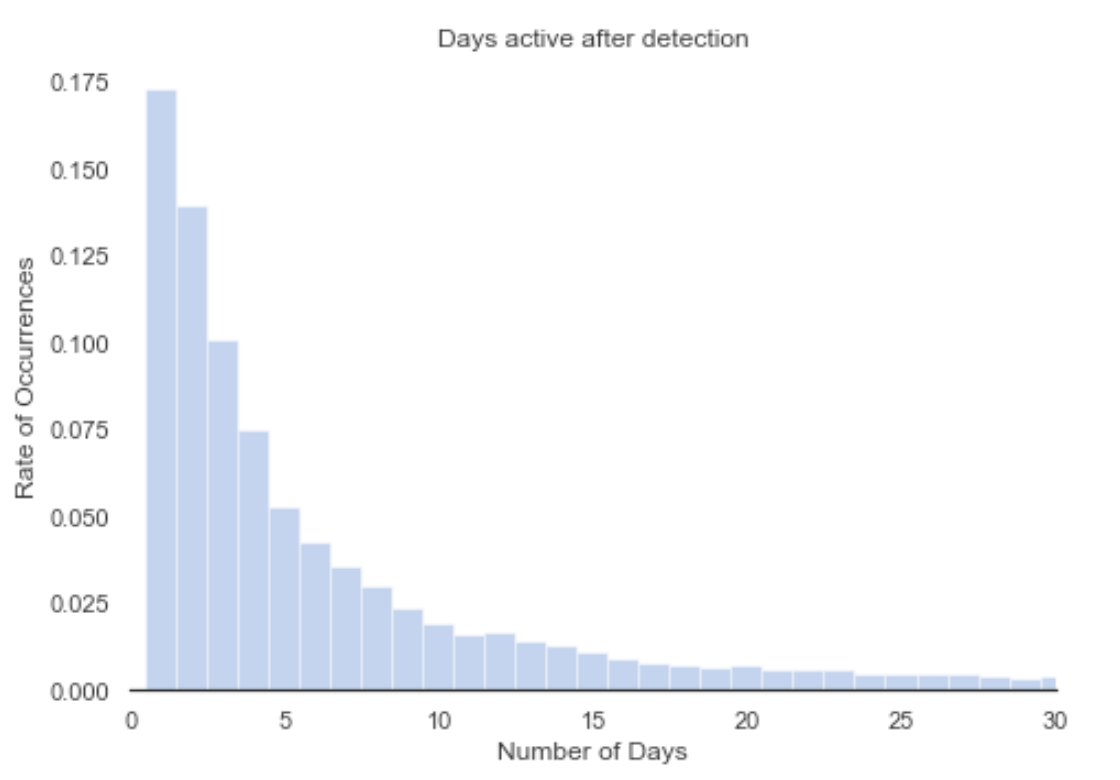
We can see that both histograms are very similar. It seems that being detected doesn’t have a considerable effect on how long a given domain remains active. This is indicative of attackers with very limited expertise since there is no point to maintain an active website that has been detected as a phishing website, when most browsers will block them.
These websites are most likely going offline because the time window considered by the attacker is fulfilled or they are blocked by the registrars. Compared with the previous case, after three, five and 10 days, the number of detected sites are 41%, 54% and 69%.
Last, let’s take a look at how many of these domains are using encryption. This can simply be obtained by looking at the protocol used. Websites using HTTP are not using encryption while websites using HTTPS are using SSL as part of the communication.
The amount of HTTPS domains represents 47% of the total websites. Just a year ago, this number was 10% which shows how attacks are becoming more sophisticated.
Phishing detection, the good, the bad and the ugly
There isn’t a single solution to detect all types of phishing. Training the user to follow simple rules (such as don’t click shady links, use a password manager and double check with the sender when an unexpected email is received) can help avoid phishing attacks, but as we mentioned earlier, they are becoming increasingly sophisticated and even security experts can be fooled by these attacks.
Some automatic countermeasures are implemented by different solutions, for example email filters warn us if we are receiving an email from someone that is obviously impersonating someone from our contact list. In the same way, crowdsourced projects such as phishtank provide open databases of known phishing sites that are used by browsers and VPNs to block access to these URLs.
But these methods don’t protect us against zero-day or currently unknown phishing sites. As we showed before, phishing sites can remain undetected for a long time before being detected, rendering this approach ineffective for new or silent attacks.
Contact us
If you’d like to learn how to secure your mobile devices from phishing attacks, please contact us. We are here to help.


