Cybersecurity Maturity Model Certification (CMMC) & Mobile Devices

What is the Cybersecurity Maturity Model Certification (CMMC)?
The Cybersecurity Maturity Model Certification (CMMC) is a unified standard for implementing cybersecurity across the defense industrial base (DIB). The US Department of Defense (DoD) released version 1.0 on January 31, 2020 and version 2.0 in February, 2022.
What’s Included in the CMMC Requirements?
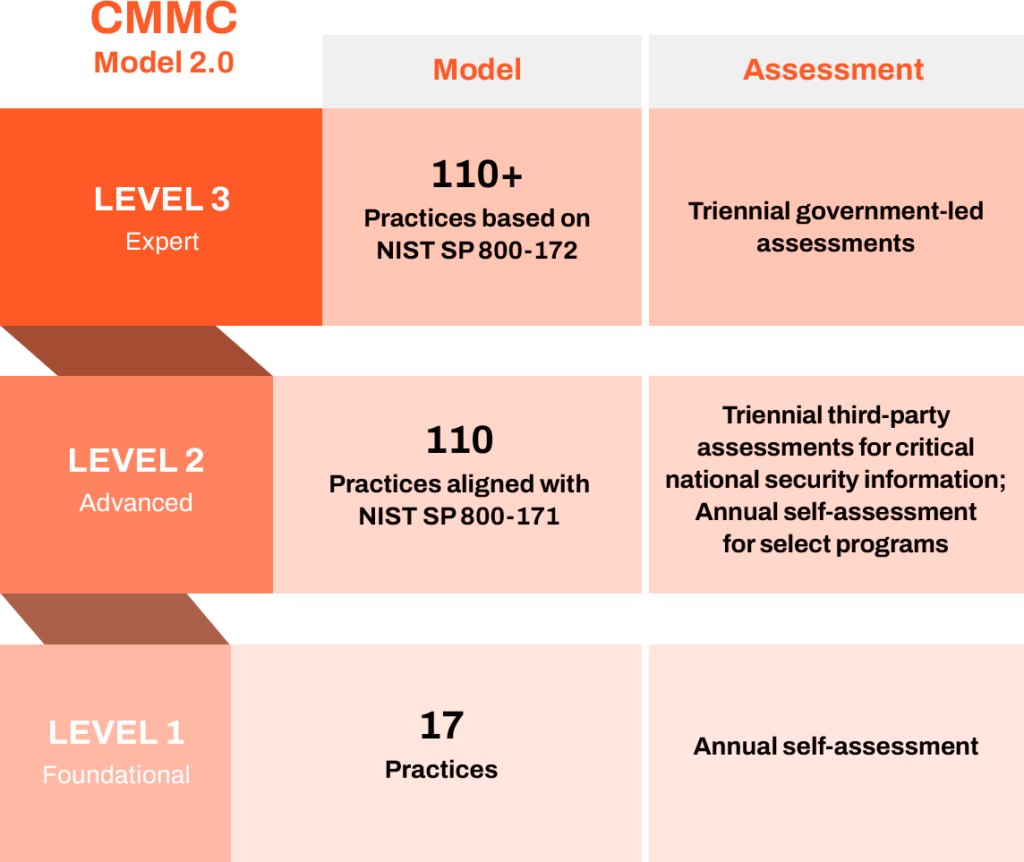
CMMC 2.0 consists of three levels:
- Level 1 (Foundational) only applies to companies that focus on the protection of federal contact information (FCI). It looks to protect covered contractor information systems and restrict access to only authorized users.
- Level 2 (Advanced) applies to companies working with controlled unclassified information (CUI). It mirrors requirements in National Institute of Standards and Technology (NIST) Special Publication (SP) 800-171.
- Level 3 (Expert) focuses on reducing the risk from Advanced Persistent Threats (APTs) and is intended for companies working with CUI on DoD’s highest priority programs. It is based on a subset of requirements from National Institute of Standards and Technology (NIST) Special Publication (SP) 800-172.
Certifications are awarded after passing an assessment conducted by a CMMC Third-Party Assessment Organization (C3PAO) and Certified Assessor.
How and Where Does Mobile Factor into CMMC?
There are specific requirements around incorporating mobile device usage restrictions, scanning a device for software updates and patches, and conducting operating system (OS) integrity checks within the cybersecurity mix of an organization. A Mobile Threat Defense (MTD) solution provides DIB members with the mobile security capabilities needed in order to achieve their CMMC mobile security compliance.
The CMMC Level 2 Assessment Guide references NIST SP 800-124r2 “Guidelines for Managing the Security of Mobile Devices in the Enterprise” under practice AC.L2-3.1.18. In section 4 “Overview of Mobile Security Technologies,” NIST explains that mobile security technologies have evolved over the past decade and details how these solutions work together to enable robust mobile device security. NIST 800-124r2 specifically distinguishes MTD from EMM, MDM, and MAM in section 4.2.3 “Mobile Threat Defense” by outlining the following MTD capabilities:
- Real-time continuous monitoring
- Assessing apps after deployment and during runtime
- Detecting and protecting mobile devices, apps, and end users against attack via wireless network
- Detecting attacks against an app or OS software, such as side-loaded apps
- Detecting and alerting users to unexpected interactions among apps or use of data on the device
Organizations Seeking Certification (OSCs) must supplement their management tools (MDMs and MAMs) with an MTD security solution. The CMMC Level 2 Assessment Guide’s “Discussion [NIST 800-171 R2]” references SP 800-124, which defines MTD’s capabilities for augmenting mobile device security technology stack specifically. MTD is critical for companies seeking CMMC Level 2 Assessments because it ensures comprehensive threat mitigation and provides countermeasures for exploitation of underlying vulnerabilities in devices and credential theft via phishing.
How Zimperium Uniquely Protects Mobile Devices for CMMC 2.0 Compliance
Zimperium Mobile Threat Defense (MTD) – formerly known as zIPS – is an advanced mobile security solution for enterprises and government agencies in the DIB striving to meet current CMMC standards as part of their mobile device security controls. To safeguard CUI and FCI against mobile threats and risks, Zimperium MTD detects mobile threats, notifies security teams of incidents, and blocks access to the resources.
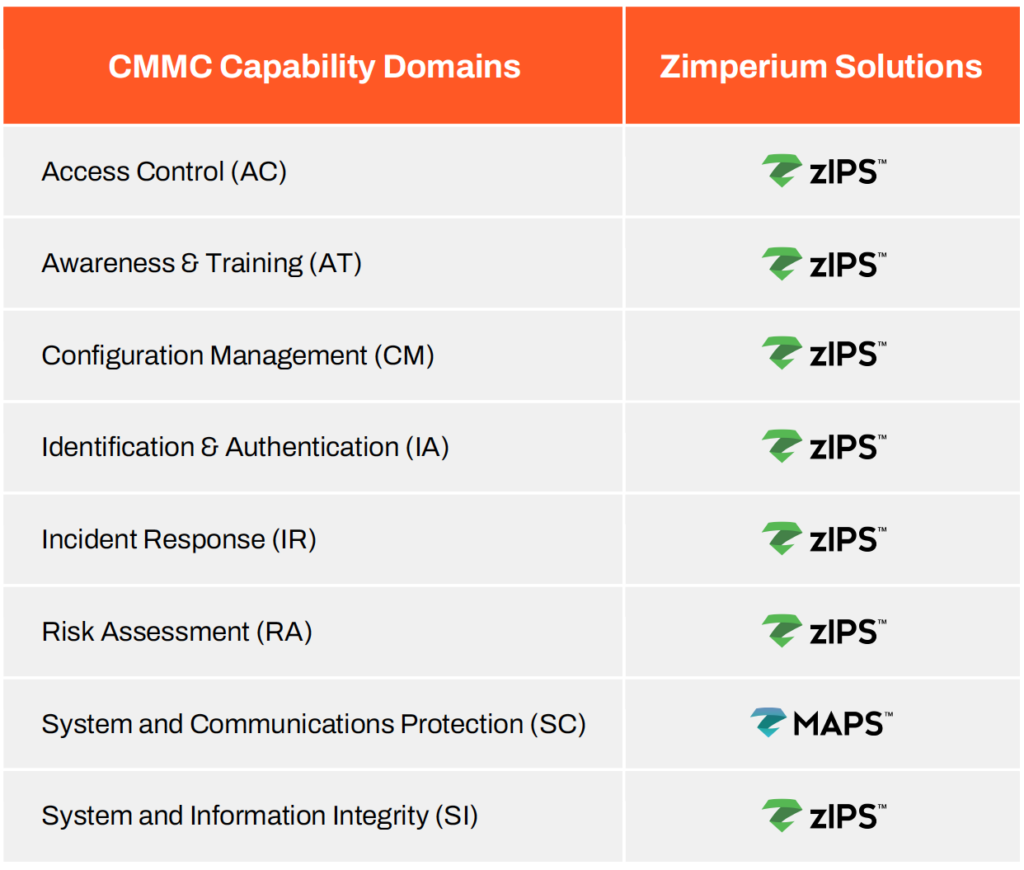
With Zimperium’s Mobile Application Protection Suite (MAPS) and Advanced Mobile Threat Defense solution, Zimperium MTD, the DIB can implement the controls necessary for reaching their desired CMMC level effectively and efficiently. This chart depicts some of the CMMC Capability Domains that Zimperium’s product suite aligns with, and that DIB members can utilize in order to meet CMMC compliance.
Zimperium was the first mobile threat defense (MTD) provider to be granted an Authority to Operate (ATO) status from the Federal Risk and Authorization Management Program (FedRAMP) and is used by many government organizations, including the U.S. Department of Defense (DoD).

Key Features of Zimperium’s Mobile Threat Defense Solution

- Critical Data, Where You Need It: With integrations into enterprise SIEM, IAM, UEM, and XDR platforms, administrators always have the data they need.
- Deploy Anywhere: Address local data laws and compliance needs by deploying to any cloud, on-premise, or air-gapped environments.
- Zero-Touch Deployment: Deploy and activate Zimperium MTD on your employees’ and contractors’ mobile endpoints without the need for complicated activation steps by the end-user.
- Critical Data: Comprehensive device attestation enables enterprises to have a complete picture of their mobile endpoint security and shores up Zero Trust architectures through existing integrations.
- Complete Mobile Coverage: No matter the mobile device, from tablet to phones, Zimperium provides complete security coverage across Android, iOS, and ChromeOS.
- Dynamic Content Filtering: Minimize web-based threats through advanced detection and prevention for malicious and risky sites through 70 content categories and granular policies.
By incorporating Zimperium MTD, you can improve your mobile security strategy and prepare for CMMC compliance. Zimperium can help protect the DIB sector from rising mobile threats and risks so you can remain competitive. For more information on how Zimperium can help you meet CMMC requirements, contact us today.