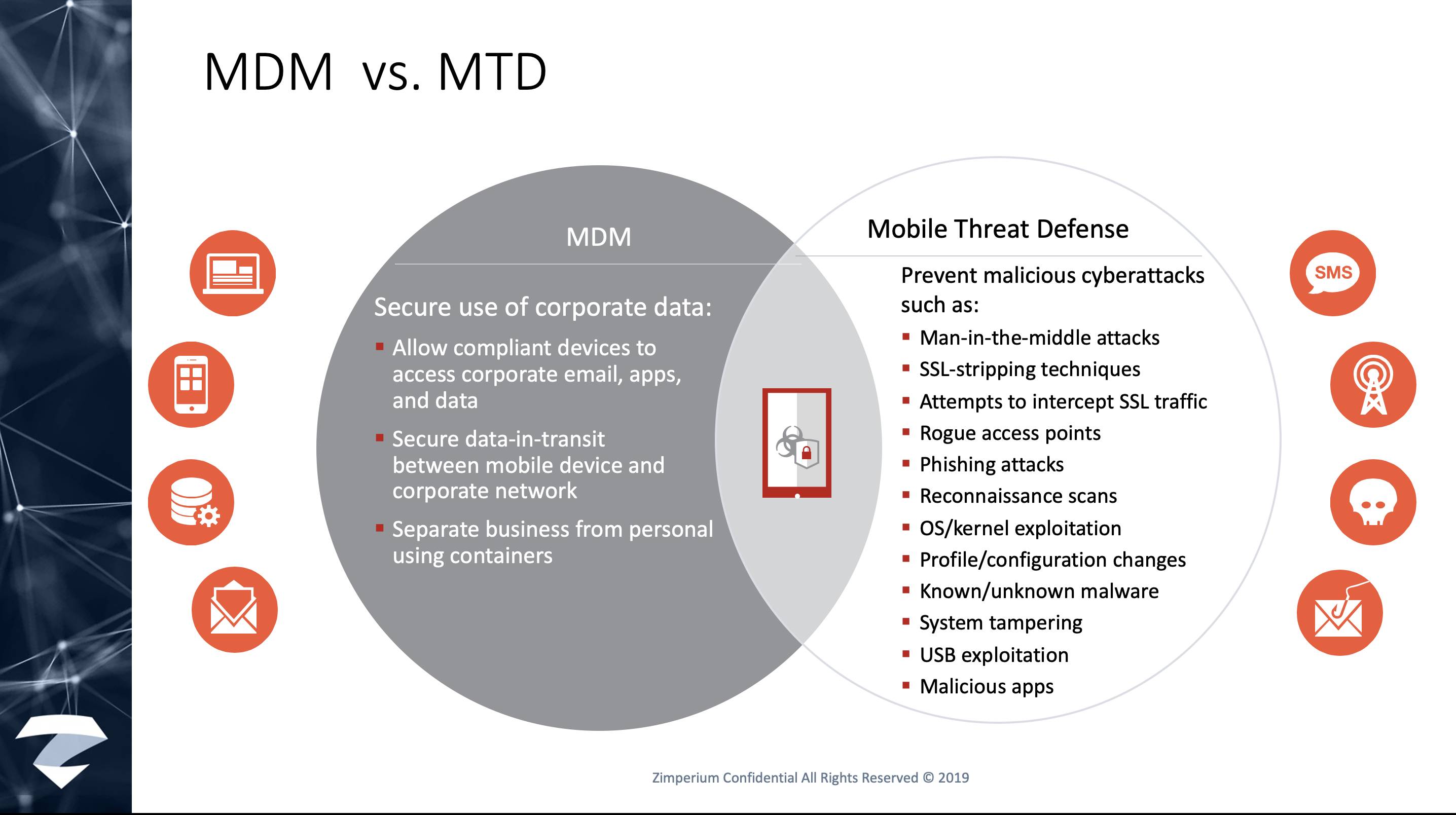
One manages an enterprises’ mobile devices; the other detects and prevents mobile device, network, phishing and malicious app attacks
I recently had the pleasure of participating in a webinar with Mikel Draghici – a Principal Engineer at Zimperium – and JT Keating – our SVP of Marketing, in which we talked about the differences between mobile threat defense (MTD) and mobile device management (MDM).
The webinar – The Other Half of the Equation: Why Security-conscious Agencies Combine UEM and MTD – really came about over confusion I’ve seen with some entities within the government sector as to the roles and differences between MDMs and MTDs.
To view the webinar in its entirety, please click here.
Over the years, we’ve seen parity between how laptops/desktops and mobile devices are used and the information/data contained. However, while the overwhelming majority of laptops and desktops are protected by enterprises (would you ever leave your office without some sort of protection on your laptop), the same cannot be said about mobile devices.
Similar to a configuration manager for laptops and desktops, enterprises may have an MDM in place to manage mobile devices from a central location.
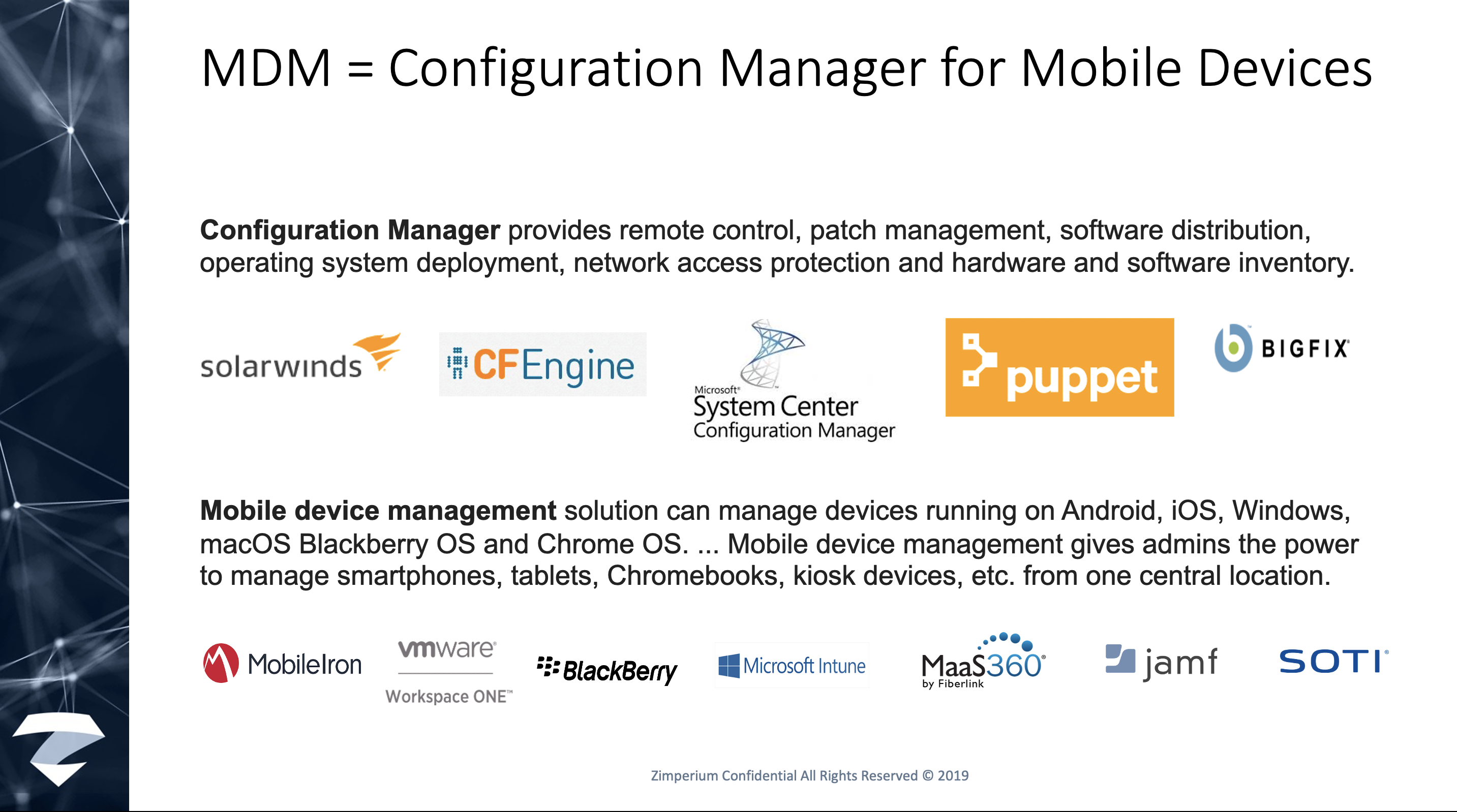
An MDM is a management tool. It allows compliant devices to access corporate email, apps via the corporate app store, and data, and it secures data-in-transit between the mobile device and the corporate network.
MTD solutions detect and prevent mobile device, network, phishing and malicious app attacks. As an example of these types of threats, we’ve seen increases and spikes in mobile breaches and compromises during COVID. And we are not alone:
- More than 18 million daily malware and phishing emails related to COVID-19 scams were seen by Google just in the past week. That’s on top of the more than 240 million daily spam messages it sees related to the novel coronavirus; and
- Wall Street Journal warned of a significant rise in phishing, robocall and “smishing” (text-message scams sent to your phone) schemes involving stimulus checks, airline refunds, charities, fines for breaking social-distancing rules, “mandatory” COVID-19 preparedness tests, unproven treatments and sales of in-demand supplies like masks or thermometers.
MDMs manage; MTDs prevent and detect.
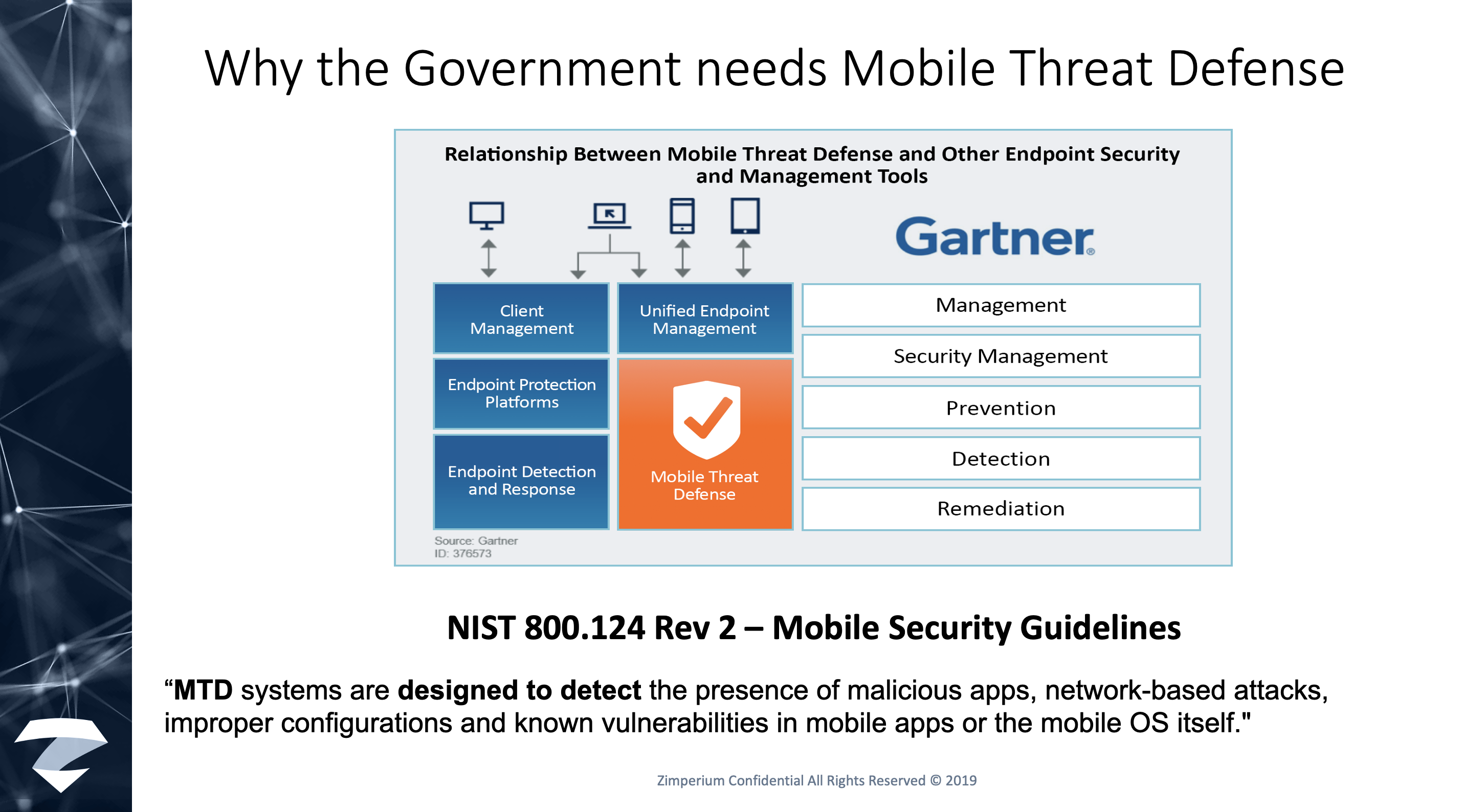
Both Gartner and the National Institute of Standards and Technology (NIST) acknowledge the importance of MTD in securing endpoints.
Better Together
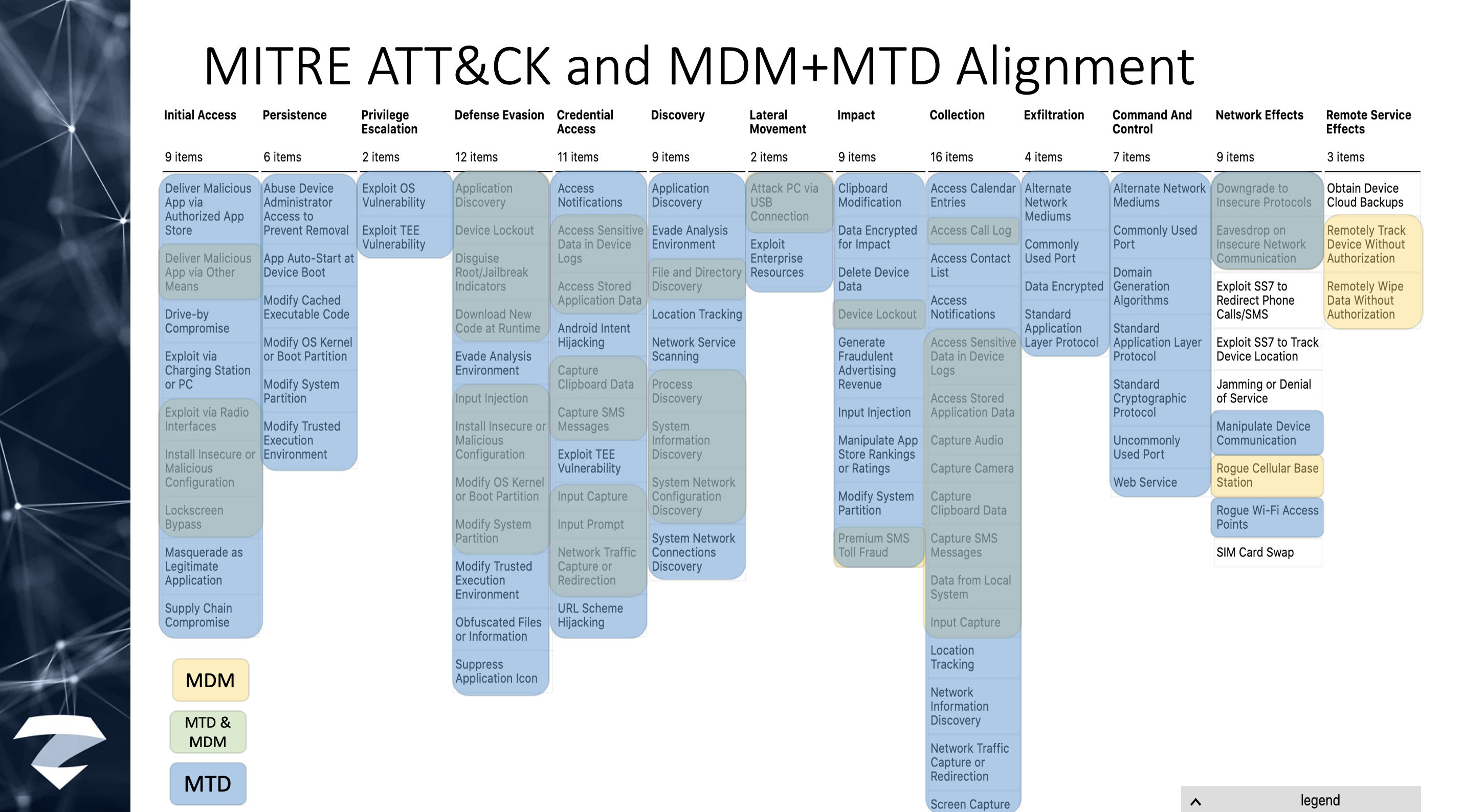
MITRE ATT&CK is a globally-accessible knowledge base of adversary tactics and techniques based on real-world observations. The ATT&CK knowledge base is used as a foundation for the development of specific threat models and methodologies in the private sector, in government, and in the cybersecurity product and service community.
Alone, MDMs don’t address these tactics and techniques (again, MDMs are not designed to do so).
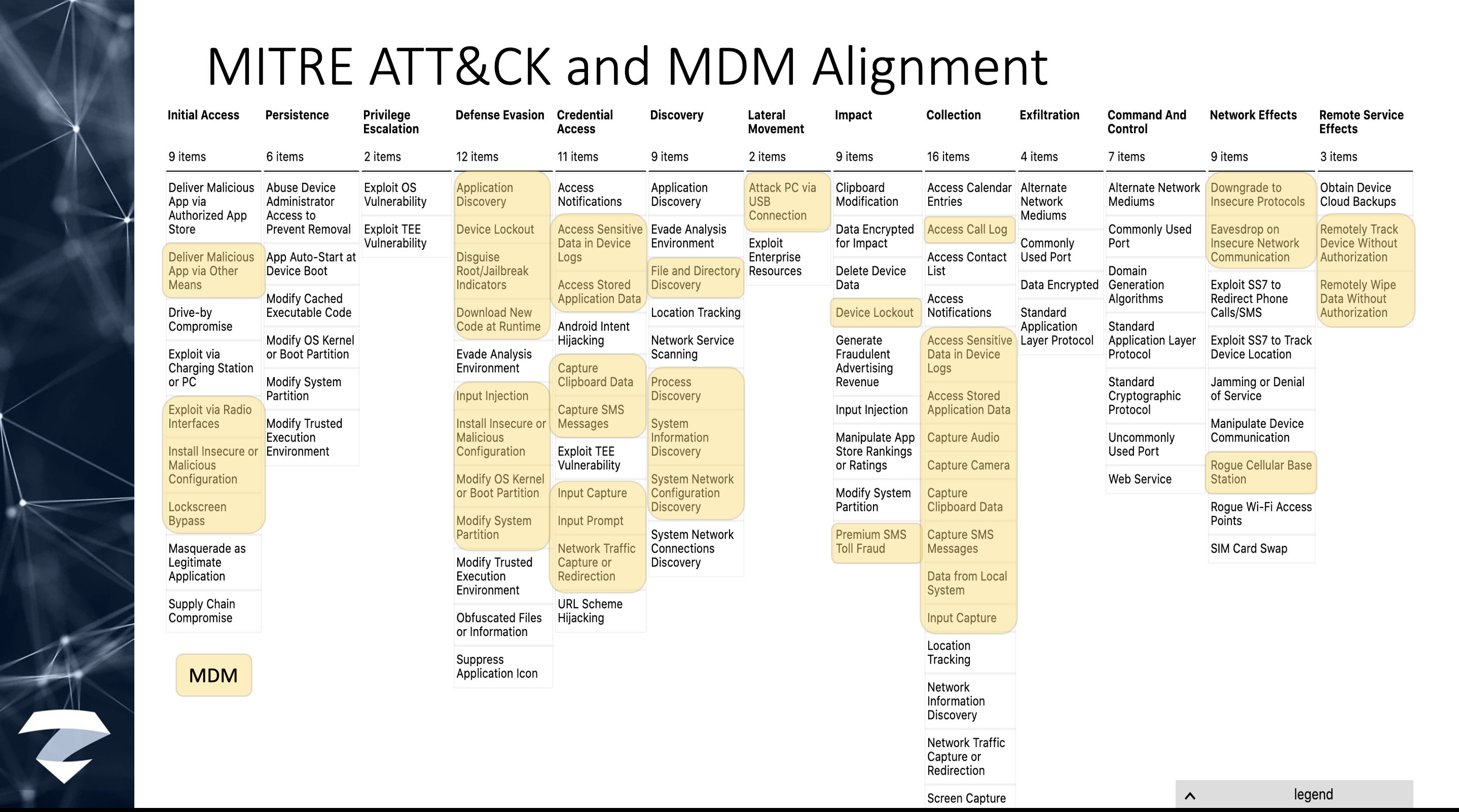
Together with an MTD, it’s a much better protective posture.
Learn more
To view the webinar in its entirety, please click here. If you would like to learn more about actual mobile attacks and what enterprises and agencies can do to protect themselves, please download our “Anatomy of a Mobile Attacks” whitepaper. To learn more, please contact us. We are here to help.




