On June 28th, a group of eight academics across three different universities released a research paper outlining a new Android vulnerability called “RAMpage”. It’s a variation of previous attacks that use the Rowhammer hardware vulnerability to run malicious code by changing what’s stored in a device’s memory (RAM) and has […]
ZipperDown Vulnerability: 100 Million iOS Users (Not Using Zimperium) at Risk of Exploit
Last Monday, security researchers from iOS jailbreak firm, Pangu Lab, announced a vulnerability that they believe affects around 10% of all iOS apps. In a blog on its newly created information site, https://zipperdown.org/ , Pangu stated that its researchers noticed “a common programming error, which leads to severe consequences such […]
Don’t be caught on the wrong side of an attack
Using only cloud sourcing as the basis for mobile threat defense is the wrong side of an attack. We respect the boldness of a competitor’s CEO taking on the leader in his market. In a very literal sense, he laid his and his company’s cards on the table. This is […]
New Crucial Vulnerabilities in Apple’s bluetoothd daemon
By: Rani Idan Follow Rani Idan (@raniXCH) As part of our platform research team in Zimperium zLabs, we investigated iOS mach message IPC, focusing on available services accessible from within the iOS sandbox. The goal of this effort was to assess potential opportunities to gain privilege escalation and escape the sandbox, […]
Threat Advisory: Meltdown & Spectre
According to the team at Graz University of Technology that responsibly disclosed the new bugs, Meltdown and Spectre exploit critical vulnerabilities in modern processors. These hardware bugs allow programs to steal data which is currently processed on the computer. While programs are typically not permitted to read data from other […]
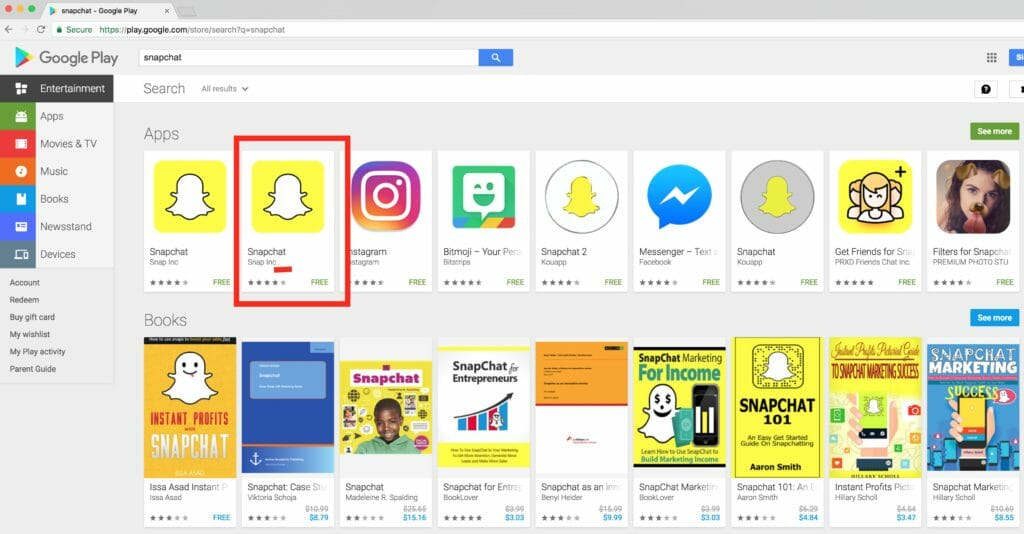
Fake Snapchat in Google Play Store
Zimperium discovered and reported a fake version of the popular Snapchat app in the official Google Play Store; At the time of our discovery, it was the second result when searching for “Snapchat”. The fake version of Snapchat app is using “Snap Inc .” as Company Name, with a ” […]
Zimperium zLabs iOS Security Advisories
As part of zLab’s platform research team, I’ve tried to investigate an area of the kernel that wasn’t thoroughly researched before. After digging into some of Apple’s closed-source kernel modules, one code chunk led to another and I’ve noticed a little-known module, which I’ve never seen before, called AppleAVE. AppleAVE was written neglecting basic security […]
NDAY-2017-0105: Elevation of Privilege Vulnerability in MSM Thermal Driver
By: Zuk Avraham Follow Zuk Avraham (@ihackbanme) Nicolas Trippar Follow Nicolas Trippar (@ntrippar) Following our announcement on the N-Days Exploit Acquisition Program for smartphones, we are delighted to share the first couple of submissions. We received many submissions and we’re in the process of sharing them with ZHA followed by a public disclosure. […]
Secure Your Smart Phones at RSA with Zimperium
Mobile is Your Greatest Cyber Vulnerability and the Zimperium team will be demonstrating the latest in enterprise Mobile Threat Defense at RSA. Get a Trial at the Expo Booth Visit our expo booth N4710, Moscone North to meet with the zLabs Global Threat Intelligence team, for an in-depth look at our industry-leading […]
Analysis of multiple vulnerabilities in AirDroid
Reported by: Simone Margaritelli Security Researcher at Zimperium zLabs Edit: 11:02AM PDT: added exploit POC code below the disclosure timeline. Edit2: 06:01PM PDT: edited timeline to reflect 4.0.0 and 4.0.1 release dates and confirming that both versions are still vulnerable. Edit3: Dec 12th, 2016, 10:41AM PDT: edited timeline to reflect […]
Mobile Security Updates
Recent Posts
- What Good Mobile App Security Visibility Looks Like: Discover What Lurks Within Your Enterprise’s Mobile Ecosystem
- Zimperium Positioned as the Leader in the 2024 SPARK MatrixTM for In-App Protection by Quadrant Knowledge Solutions
- Understanding IRAP: Australia’s Commitment to Upholding Best-in-Class Security Standards