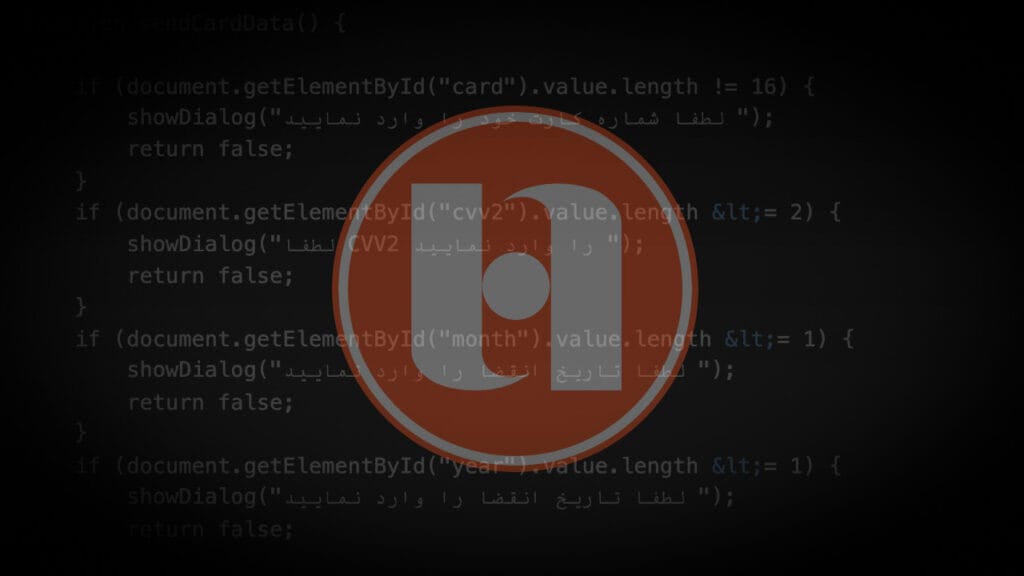
Research by Aazim Bill SE Yaswant and Vishnu Pratapagiri In July 2023, it was discovered that an Android mobile campaign, which consisted of banking trojans, was targeting major Iranian banks. Zimperium’s research team recently found that the campaign not only remains active but also extended its capabilities. These newly found samples are completely […]
Leveraging NIST Standards to Streamline Your Mobile-First Security Strategy
This webinar teaches how cybersecurity professionals rely on resources, such as NIST standards, to develop their mobile device security approach.
Predator Spyware Strikes Again
On September 22nd, Citizen Lab, in collaboration with Google Project Zero, released a joint report revealing that Ahmen Eltantawy, a former Egyptian member of parliament, was targeted using highly sophisticated spyware. The recent payload obtained and analyzed by Citizen Lab matches the findings reported in a previous report, confirming that […]
Unveiling the Tactics of Lapsus$: A Review of Internal Attacks Vectors, Mobile Device Exploitation, and Social Engineering Techniques
On August 10, 2023, the U.S. Department of Homeland Security (DHS) released the Cyber Safety Review Board (CSRB) report summarizing the findings of its review into the activities of threat actor group Lapsus$, who, beginning in late 2021 and continuing into late 2022, attempted to extort dozens of well-known global […]
Kimsuky: Infamous Threat Actor Churns Out More Advanced Malware
The Hacker News recently published a story that discussed a joint communication among the German intelligence apparatus, the Federal Office for the Protection of the Constitution (BfV), and South Korea’s National Intelligence Service (NIS), warning readers about new tactics used by a North Korean threat actor called Kimsuky. Learn more about Kimsuky and how Zimperium Mobile Threat Defense (MTD) customers are protected against these threats.
Risky Business: How Mobile Apps Can Pose Threats to Your Organization
Today, organizations need to mitigate threats arising from risky applications. While all third-party apps may not be malicious, they can lead to data loss and leakage. Learn how Zimperium MTD can help organizations identify which mobile devices have risky or banned apps and enable organizations to identify, block, and enforce policies to reduce the harm from risky apps to their business. Read more.
MoneyMonger: Predatory Loan Scam Campaigns Move to Flutter
The Zimperium zLabs team recently discovered a Flutter application with malicious code. The Flutter-obfuscated malware campaign, MoneyMonger, is solely distributed through third-party app stores and sideloaded onto the victim’s Android device and most commonly take advantage of social engineering through phishing messages, compromised websites, rogue WiFi networks, and social media to distribute the download links. Read more to learn how Zimperium customers are protected.
More Than MDM: Mobile Device Security for CMMC Compliance
To meet CMMC compliance, you need to prove that you have a comprehensive approach to mobile device security. Learn how Zimperium zIPS MTD solution helps enterprises and government agencies in the DIB to meet current CMMC standards as part of their mobile device security controls.
Zimperium Named One of the Fastest-Growing Companies in North America on the 2021 Deloitte Technology Fast 500™
Dallas, Texas – November 18, 2021 — Zimperium today announced it was named to the Deloitte Technology Fast 500™, a ranking of the 500 fastest-growing technology, media, telecommunications, life sciences, fintech, and energy tech companies in North America, now in its 27th year. Zimperium grew 251% from 2017-2020 and is […]
CISOs and CIOs: Protecting Traditional Endpoints Isn’t Enough
As government cyber teams feverishly perform damage control from the SolarWinds hack, one major question for CISOs and CIOs cannot be ignored: “Protecting traditional endpoints isn’t enough; how am I going to assess and protect my mobile devices?” Threat visibility comes from sensors, and if your mobile devices don’t utilize […]