When it comes to compliance, you’re never truly done. The environments you’re tasked with securing and auditing continue to evolve, and so do the standards and deadlines you have to meet. The EU’s Payment Service Directive 2 (PSD2) is a current case in point. The directive had several goals, including […]
All posts by Krishna Vishnubhotla

Posts by Krishna Vishnubhotla:
LA Secure Wins ATARC GITEC Emerging Technology Award
LA Secure: Award-Winning Cybersecurity Bridges the Digital Divide The saying that “no good deed goes unpunished” often proves to be true. That’s why when good deeds actually get recognized and awarded, it is especially nice to see. It is within this context that we were delighted to hear the news […]
Los Angeles Partners with Zimperium to Keep Residents Safe on Mobile
Mobile devices keep us tethered to the rest of the world. With the shift to remote work, schooling, banking, and healthcare, residents have become increasingly reliant on remote connectivity and mobile devices. Accessing digital services via mobile helps remove friction and improve residents’ quality of life. Whether at home, school, […]
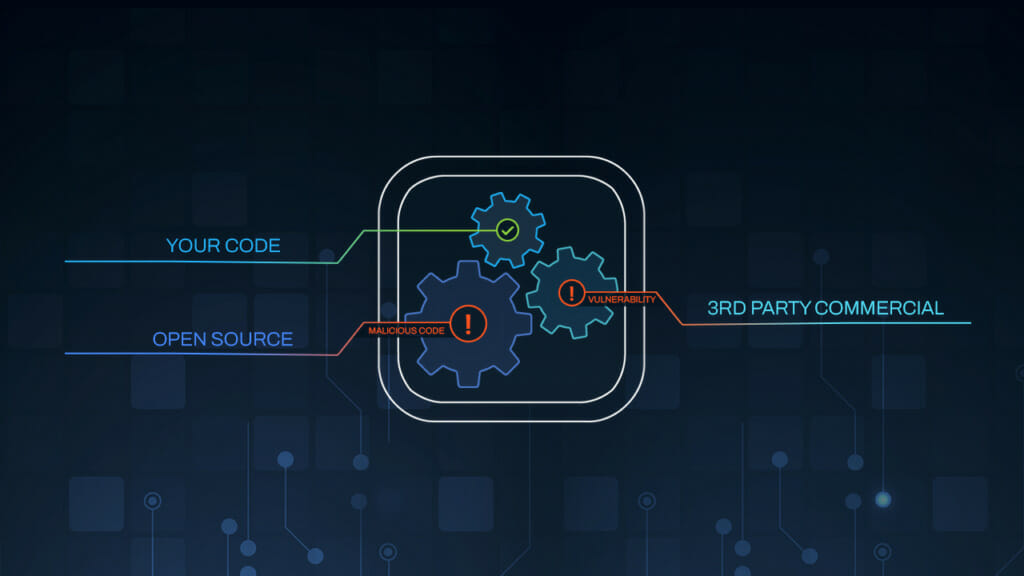
Why the Software Bill Of Materials(SBOM) Must Extend to the Mobile App Supply Chain
Supply Chain attacks are not a new problem, but their frequency has been increasing since 2013 when Target was breached. But the recent attacks on SolarWinds Orion, Kaseya VSA, Accellion, Microsoft have highlighted the fact that cybercriminals have shifted their focus from the primary targets to their suppliers. Why? […]
Zimperium Named One of the Fastest-Growing Companies in North America on the 2021 Deloitte Technology Fast 500™
Dallas, Texas – November 18, 2021 — Zimperium today announced it was named to the Deloitte Technology Fast 500™, a ranking of the 500 fastest-growing technology, media, telecommunications, life sciences, fintech, and energy tech companies in North America, now in its 27th year. Zimperium grew 251% from 2017-2020 and is […]
Are Healthcare Mobile Applications Really Healthy
Mobile apps are one of the most significant areas of growth in the healthcare industry. Before 2020, the market grew at more than 20% a year and is on its way to being worth $130 billion by 2022. And that was before the COVID-19 crisis, which has pushed a considerable […]
Zimperium Powers the Telkomsel JagaJaga App to Protect Consumers on Their Mobile Devices.
Last year 67% percent of the population in Indonesia used a smartphone. The number of smartphone users in the country is estimated to reach 239 million by 2026. These are staggering stats for the 4th most populous country in the world. It’s also one of the world’s fastest-growing mobile app […]
Your new car may be safer and smarter, but is it cyber-secure?
The auto industry reached an important milestone in 2020: more than half of the cars sold globally included internet connectivity as a standard feature. Modern vehicles have started to resemble mobile supercomputers, with each one containing millions of lines of code and able to process vast amounts of data. They’ve […]
Financial Apps Are Not As Safe As You Think
The Rise of Financial Mobile Apps Financial mobile applications help businesses across all sectors take advantage of growing markets. They create additional value through improved customer experience and reduce costs through process automation. Whether used for traditional banking or payment processing, apps are changing how businesses operate. This steep but […]
Automate Mobile Application Security Testing from Jenkins
Mobile apps require continuous testing throughout the development process to ensure proper compliance and security measures are in place. If you are using Jenkins continuous integration server in your pipeline, continually testing your mobile app builds is simple with Zimperium’s mobile application security testing platform, zScan. Here we will describe […]
Mobile Security Updates
Recent Posts
- What Good Mobile App Security Visibility Looks Like: Discover What Lurks Within Your Enterprise’s Mobile Ecosystem
- Zimperium Positioned as the Leader in the 2024 SPARK MatrixTM for In-App Protection by Quadrant Knowledge Solutions
- Understanding IRAP: Australia’s Commitment to Upholding Best-in-Class Security Standards